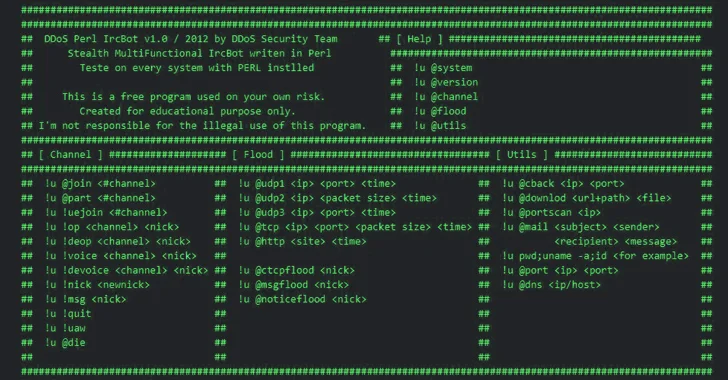
The threat actors powering ShellBot are leveraging IP addresses transformed into its hexadecimal notation to infiltrate badly managed Linux SSH servers and deploy the DDoS malware.
“The general move stays the exact, but the obtain URL made use of by the threat actor to set up ShellBot has modified from a typical IP deal with to a hexadecimal benefit,” the AhnLab Security Unexpected emergency response Middle (ASEC) said in a new report published now.
ShellBot, also recognized by the name PerlBot, is acknowledged to breach servers that have weak SSH credentials by usually means of a dictionary attack, with the malware applied as a conduit to phase DDoS attacks and produce cryptocurrency miners.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Formulated in Perl, the malware employs the IRC protocol to communicate with a command-and-management (C2) server.
The hottest set of noticed attacks involving ShellBot has been uncovered to set up the malware employing hexadecimal IP addresses – hxxp://0x2763da4e/ which corresponds to 39.99.218[.]78 – in what is actually witnessed as an attempt to evade URL-primarily based detection signatures.
“Because of to the utilization of curl for the down load and its ability to help hexadecimal just like web browsers, ShellBot can be downloaded productively on a Linux method atmosphere and executed by Perl,” ASEC said.
The advancement is a signal that ShellBot carries on to witness continuous utilization to start attacks versus Linux devices.
With ShellBot capable of staying used to set up supplemental malware or launch distinct types of attacks from the compromised server, it truly is advisable that users change to sturdy passwords and periodically alter them to resist brute-pressure and dictionary attacks.

The disclosure also arrives as ASEC discovered that attackers are weaponizing abnormal certificates with unusually very long strings for Matter Name and Issuer Name fields in a bid to distribute information and facts stealer malware this sort of as Lumma Stealer and a variant of RedLine Stealer known as RecordBreaker.
“These kinds of malware are dispersed by using malicious internet pages that are quickly obtainable by look for engines (Search engine marketing poisoning), posing a risk to a wide vary of unspecified consumers,” ASEC explained. “These malicious web pages generally use keywords relevant to illegal courses these types of as serials, keygens, and cracks.”
Discovered this post appealing? Comply with us on Twitter and LinkedIn to examine much more exclusive articles we article.
Some components of this posting are sourced from:
thehackernews.com

 How to Guard Your Data from Exposure in ChatGPT
How to Guard Your Data from Exposure in ChatGPT