A destructive toolset dubbed Spacecolon is becoming deployed as component of an ongoing campaign to spread variants of the Scarab ransomware across victim businesses globally.
“It likely finds its way into victim businesses by its operators compromising vulnerable web servers or through brute forcing RDP credentials,” ESET security researcher Jakub Souček reported in a in-depth technical compose-up posted Tuesday.
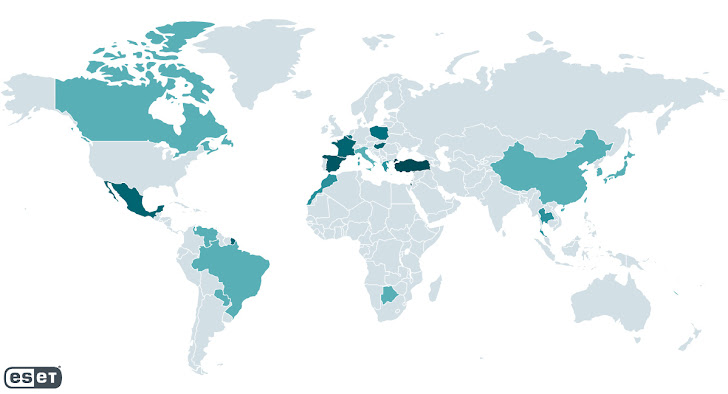
The Slovak cybersecurity company, which dubbed the menace actor CosmicBeetle, mentioned the origins of the Spacecolon date again to Could 2020. The optimum concentration of victims has been detected in France, Mexico, Poland, Slovakia, Spain, and Turkey.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Though the specific provenance of the adversary is unclear, several Spacecolon variants are said to comprise Turkish strings, probably pointing to the involvement of a Turkish-speaking developer. There is no evidence at present linking it to any other acknowledged threat actor group.

Some of the targets contain a hospital and a vacationer resort in Thailand, an coverage firm in Israel, a neighborhood governmental establishment in Poland, an leisure company in Brazil, an environmental enterprise in Turkey, and a school in Mexico.
“CosmicBeetle does not pick out its targets fairly, it finds servers with critical security updates missing and exploits that to its benefit,” Souček pointed out.
It truly is really worth noting that Spacecolon was to start with documented by Polish enterprise Zaufana Trzecia Strona in early February 2023, very likely prompting the adversary to tweak its arsenal in reaction to general public disclosures.
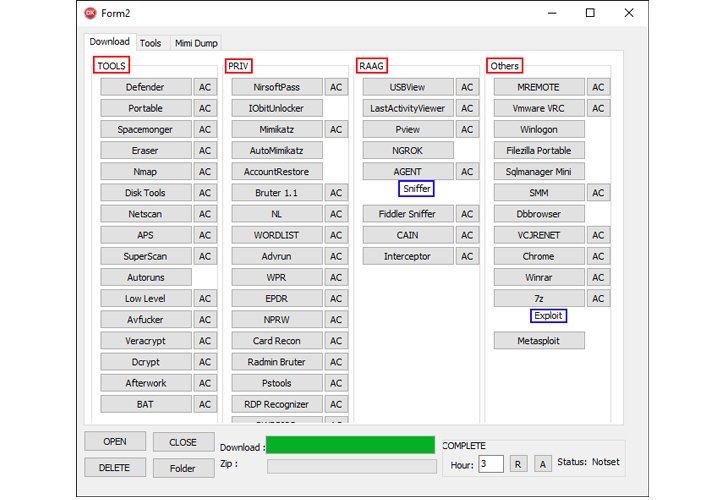
The most important element of Spacecolon is ScHackTool, a Delhi-dependent orchestrator that’s employed to deploy an installer, which, as the title indicates, installs ScService, a backdoor with features to execute custom made commands, obtain and execute payloads, and retrieve system details from compromised equipment.
ScHackTool also functions as a conduit to established up a extensive array of third-party tools fetched from a distant server (193.149.185[.]23). The best aim of the attacks is to leverage the access afforded by ScService to produce a variant of the Scarab ransomware.

An alternate version of the infection chain recognized by ESET involves the use of Impacket to deploy ScService as opposed to applying ScHackTool, indicating that the threat actors are experimenting with distinctive methods.
CosmicBeetle’s monetary motives are further more bolstered by the simple fact that the ransomware payload also drops a clipper malware to continue to keep tabs on the program clipboard and modify cryptocurrency wallet addresses to people less than the attacker’s handle.
Additionally, there is proof that the adversary is actively establishing a new ransomware strain dubbed ScRansom, which makes an attempt to encrypt all difficult, removable, and remote drives working with the AES-128 algorithm with a key generated from a tricky-coded string.
“CosmicBeetle would not make substantially hard work to conceal its malware and leaves lots of artifacts on compromised units,” Souček reported. “Minimal to no anti-examination or anti-emulation techniques are applied. ScHackTool relies seriously on its GUI, but, at the exact time, incorporates many nonfunctional buttons.”
“CosmicBeetle operators use ScHackTool mostly to download further instruments of alternative to compromised equipment and operate them as they see match.”
Observed this post exciting? Observe us on Twitter and LinkedIn to study more unique articles we put up.
Some areas of this short article are sourced from:
thehackernews.com

 Over a Dozen Malicious npm Packages Target Roblox Game Developers
Over a Dozen Malicious npm Packages Target Roblox Game Developers