An superior pressure of malware masquerading as a cryptocurrency miner has managed to fly the radar for in excess of five yrs, infecting no a lot less than one million equipment all over the entire world in the process.
That’s in accordance to conclusions from Kaspersky, which has codenamed the menace StripedFly, describing it as an “intricate modular framework that supports both of those Linux and Windows.”
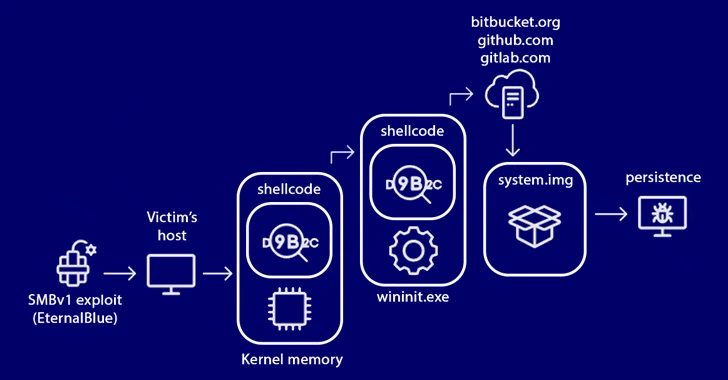
The Russian cybersecurity vendor, which first detected the samples in 2017, reported the miner is aspect of a much much larger entity that employs a personalized EternalBlue SMBv1 exploit attributed to the Equation Group in buy to infiltrate publicly-available units.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The destructive shellcode, sent via the exploit, has the ability to download binary information from a remote Bitbucket repository as effectively as execute PowerShell scripts. It also supports a collection of plugin-like expandable characteristics to harvest sensitive knowledge and even uninstall by itself.
The platform’s shellcode is injected in the wininit.exe method, a legitimate Windows procedure which is begun by the boot manager (BOOTMGR) and handles the initialization of various expert services.
“The malware payload alone is structured as a monolithic binary executable code designed to guidance pluggable modules to extend or update its performance,” security researchers Sergey Belov, Vilen Kamalov, and Sergey Lozhkin said in a technical report printed past week.
“It will come equipped with a constructed-in TOR network tunnel for conversation with command servers, along with update and delivery functionality through reliable expert services these kinds of as GitLab, GitHub, and Bitbucket, all employing custom made encrypted archives.”

Other noteworthy spy modules allow it to obtain credentials each individual two several hours, seize screenshots on the victim’s system devoid of detection, history microphone enter, and start off a reverse proxy to execute distant actions.
Upon gaining a thriving foothold, the malware proceeds to disable the SMBv1 protocol on the infected host and propagate the malware to other machines utilizing an worming module by means of equally SMB and SSH, working with keys harvested on the hacked methods.
StripedFly achieves persistence by both modifying the Windows Registry or by creating undertaking scheduler entries if the PowerShell interpreter is put in and administrative access is offered. On Linux, persistence is achieved by usually means of a systemd user provider, autostarted .desktop file, or by modifying /and so on/rc*, profile, bashrc, or inittab files.
Also downloaded is a Monero cryptocurrency miner that leverages DNS in excess of HTTPS (DoH) requests to resolve the pool servers, adding an added layer of stealth to the destructive routines. It has been assessed that the miner is employed as a decoy to prevent security application from exploring the complete extent of the malware’s capabilities.
In an hard work to decrease the footprint, malware parts that can be offloaded are hosted as encrypted binaries on numerous code repository hosting providers this kind of as Bitbucket, GitHub, or GitLab.
For occasion, the Bitbucket repository operated by the menace actor since June 2018 features executable information able of serving the original an infection payload across both Windows and Linux, examining for new updates, and eventually updating the malware.
Interaction with the command-and-manage (C2) server, which is hosted in the TOR network, usually takes area employing a personalized, light-weight implementation of a TOR client that is not centered on any publicly documented approaches.
“The amount of devotion shown by this performance is exceptional,” the researchers reported. “The intention of hiding the C2 server at all expenses drove the improvement of a exceptional and time-consuming undertaking – the creation of its have TOR consumer.”
Yet another hanging characteristic is that these repositories act as fallback mechanisms for the malware to download the update information when its principal source (i.e., the C2 server) becomes unresponsive.
Kaspersky claimed it even further uncovered a ransomware relatives referred to as ThunderCrypt that shares sizeable resource code overlaps with StripedFly barring the absence of the SMBv1 an infection module. ThunderCrypt is reported to have been applied in opposition to targets in Taiwan in 2017.
The origins of StripedFly continue to be presently mysterious, even though the sophistication of the framework and its parallels to EternalBlue exhibit all the hallmarks of an sophisticated persistent threat (APT) actor.
It really is worthy of pointing out that while the Shadow Brokers’ leak of the EternalBlue exploit took spot on April 14, 2017, the earliest identified variation of StripedFly incorporating EternalBlue dates a year back to April 9, 2016. Considering the fact that the leak, the EternalBlue exploit has been repurposed by North Korean and Russian hacking outfits to distribute the WannaCry and Petya malware.

That claimed, you can find also evidence that Chinese hacking teams may well have had access to some of the Equation Group’s exploits in advance of they ended up leaked on the internet, as disclosed by Check Issue in February 2021.
The similarities to malware affiliated with the Equation team, Kaspersky said, is also reflected in the coding type and methods resembling these seen in STRAITBIZARRE (SBZ), another cyber espionage system wielded by the suspected U.S.-connected adversarial collective.
The development arrives approximately two decades immediately after researchers from China’s Pangu Lab detailed a “top-tier” backdoor referred to as Bvp47 that was allegedly place to use by the Equation Team on much more than 287 targets spanning multiple sectors in 45 nations.
Useless to say, a vital element of the campaign that proceeds to be a mystery – other than to those who engineered the malware – is its genuine purpose.
“Although ThunderCrypt ransomware suggests a professional motive for its authors, it raises the question of why they failed to opt for the perhaps more rewarding route rather,” the scientists explained.
“It really is tricky to take the idea that this sort of subtle and professionally developed malware would serve these kinds of a trivial intent, supplied all the evidence to the contrary.”
Identified this write-up appealing? Abide by us on Twitter and LinkedIn to study additional distinctive content material we article.
Some elements of this article are sourced from:
thehackernews.com

 Okta’s Recent Customer Support Data Breach Impacted 134 Customers
Okta’s Recent Customer Support Data Breach Impacted 134 Customers