A Syrian danger actor named EVLF has been outed as the creator of malware people CypherRAT and CraxsRAT.
“These RATs are built to allow for an attacker to remotely execute actual-time steps and command the target device’s digicam, place, and microphone,” Cybersecurity company Cyfirma mentioned in a report published previous week.
CypherRAT and CraxsRAT are said to be made available to other cybercriminals as aspect of a malware-as-a-support (MaaS) plan. As lots of as 100 exclusive risk actors are approximated to have bought the twin applications on a life span license around the previous a few many years.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
EVLF is reported to be operating a web shop to publicize their warez due to the fact at the very least September 2022.

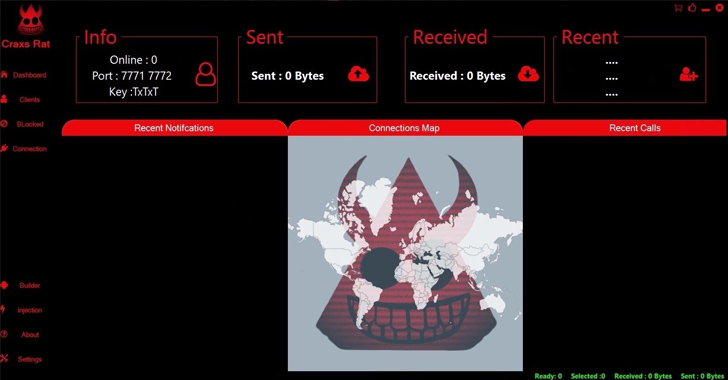
CraxsRAT is billed as an Android trojan that allows a menace actor to remote command an infected device from a Windows computer, with the developer continually releasing new updates based on opinions from the shoppers.
The malicious bundle is produced working with a builder, which comes with possibilities to personalize and obfuscate the payload, choose an icon, the application title, and the capabilities and permissions that need to have to be activated the moment mounted on the smartphone.
“CraxsRAT is a person of the most perilous RATs in the current Android risk landscape, with impactful attributes such as Google Play guard bypass, are living display look at, as perfectly as a shell for command execution,” Cyfirma spelled out.
“The ‘Super Mod’ function renders the app more lethal nevertheless, producing it really hard for victims to uninstall the app (every time the target tries to uninstall, it crashes the web site).”
The Android malware also requests victims to grant it permissions to Android’s accessibility services, allowing it to harvest a wealth of details that would be precious to cyber criminals, including call logs, contacts, exterior storage, site, and SMS messages.
EVLF has been observed functioning a Telegram channel named “EvLF Devz” that was produced on February 17, 2022. It has 10,678 subscribers as of composing.

A lookup for CraxsRAT surfaces many cracked versions of the malware hosted on GitHub, whilst it appears that Microsoft has taken down some of them more than the earlier couple of days. The GitHub account of EVLF, nevertheless, remains energetic on the code-hosting service.
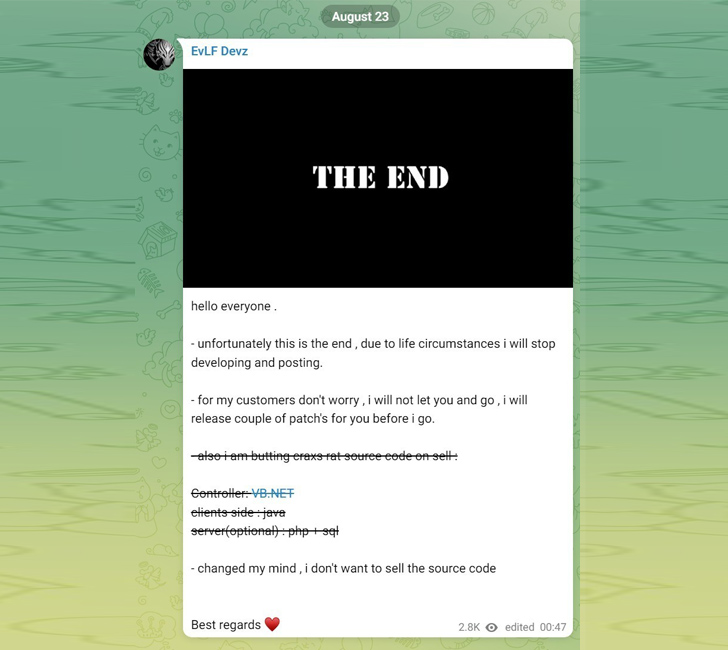
On August 23, 2023, EVLF posted a information on the channel stating they were hanging up the boots on the job, likely in reaction to the general public disclosure of their pursuits.
“unfortunately this is the conclude , owing to life circumstances i will stop acquiring and putting up,” EVLF reported in the article. “for my clients will not worry , i will not let you and go , i will launch couple of patch’s for you ahead of i go.”
Discovered this write-up appealing? Comply with us on Twitter and LinkedIn to study a lot more unique content material we put up.
Some parts of this posting are sourced from:
thehackernews.com

 Spacecolon Toolset Fuels Global Surge in Scarab Ransomware Attacks
Spacecolon Toolset Fuels Global Surge in Scarab Ransomware Attacks