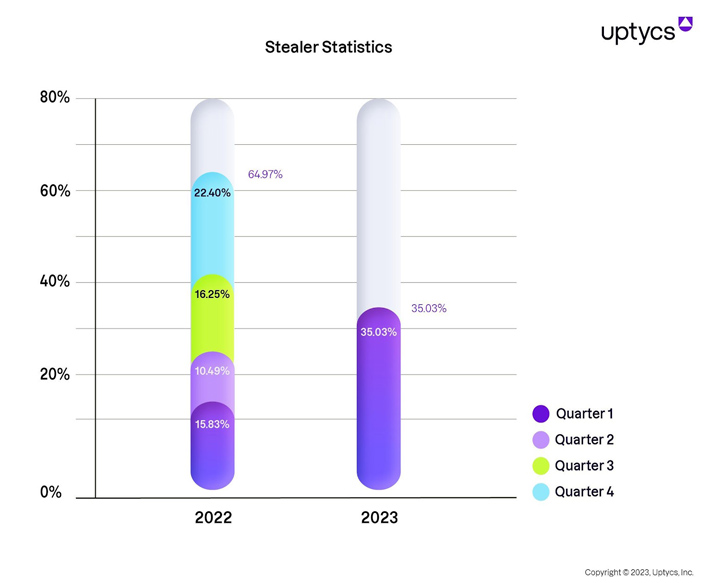
A new examine performed by Uptycs has uncovered a stark enhance in the distribution of information and facts thieving (a.k.a. infostealer or stealer) malware. Incidents have more than doubled in Q1 2023, indicating an alarming craze that threatens global corporations.
In accordance to the new Uptycs’ whitepaper, Stealers are Corporation Killers, a range of new facts stealers have emerged this calendar year, preying on Windows, Linux, and macOS programs.
Telegram has notably been applied extensively by these malware authors for command, regulate, and details exfiltration.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
What is a Stealer?
A stealer is a type of malware that targets its target by thieving delicate information and facts that can contain passwords, login credentials, and other private knowledge. Following gathering these kinds of information, the stealer sends it to the menace actor’s command and regulate (C2) procedure.
RedLine and Vidar, two effectively-recognized stealers, took edge of log-offering expert services to infiltrate non-public systems. RedLine generally targets credentials and cryptocurrency wallets on Windows techniques, as well as browser data, FTP connections, match chat launchers, and OS data. Vidar depends on shipping techniques such as phishing email messages and cracked computer software for dissemination. Alongside with Racoon, it has been included in a Google Advertisements malvertising operation that targets users on the lookout for well-known programs.
In a person of the greatest attacks in 2022, Uber fell victim to an attack by a risk actor employing the Racoon stealer. The attacker tricked victims into clicking on a bogus two-factor authentication notification, compromising their techniques. With obtain to Uber’s VPN, the attacker infiltrated the firm’s inner network methods. They ended up in a position to escalate account privileges by exploiting the firm’s accessibility administration provider. As a consequence, they obtained obtain to several Uber resources, including AWS, Duo, GSuite, OneLogin, Slack, VMware, and Windows.
The infamous Raccoon stealer malware has not long ago struck India, location its sights on eight central govt entities, such as the Earnings Tax Office and central paramilitary forces. By a destructive marketing campaign, attackers properly infiltrated computer techniques, triggering major hurt to these critical institutions.
Unveiling the Modus Operandi of Infostealers
The cybersecurity globe is fraught with advanced threats. Between the most hazardous are info stealers, capable of extracting and leaking delicate details from unique and company networks. Their stealthy functions pose a sizeable problem for detection and mitigation.
In Stealers are Organization Killers, Uptycs researchers existing an in-depth investigation of the operational framework of the infostealer underground, the propagation strategies, and the potential destruction they can inflict on organizations.
Bolster Security Defenses Versus Stealers
Understanding is your organization’s strongest shield in opposition to cyber threats. Comprehension the styles and techniques utilized by these danger actors can fortify your defenses against likely breaches.
Uptycs’ progressive platform gives a unified option to tackle this challenge. It prioritizes your responses to threats, vulnerabilities, and misconfigurations throughout your present day attack surface area, all from a single UI. The platform’s potential to tie jointly threat action as it traverses on-prem and cloud boundaries effects in a extra cohesive business-vast security posture.
Uptycs: A Unified Resolution for Evolving Cyber Threats
With the altering threat landscape, a piecemeal method to security is no more time powerful. Uptycs’ unified technique connects insights throughout your present day attack surface and brings teams collectively to fix essential security and compliance challenges.
The Uptycs Detection Cloud integrates a Google-like research functionality, permitting you to investigate MITRE ATT&CK chains, develop YARA guidelines, and look into stay and historical states, thus offering a detailed option to cybersecurity threats.
The whitepaper elaborates on the various strategies that can be applied to mitigate the challenges posed by details stealers. It serves as a treasure trove of actionable recommendations that can elevate the security posture of your corporation.
Obtain Stealers are Business Killers for an in-depth investigation of these stealers, entire with thorough diagrams and figures.
Ready to Elevate Your Cybersecurity Approach?
The evolving strategies of threat actors necessitate continual vigilance and adaptation. This whitepaper equips infosec pros with the know-how and procedures needed to stay one stage in advance of these threats.
If you happen to be dedicated to fortifying your organization’s defenses and wish to achieve a deeper comprehending of the cyber threats that you might be up towards, this whitepaper is an indispensable useful resource. Will not skip out on this chance to change up your cybersecurity with Uptycs.
Identified this write-up appealing? Abide by us on Twitter and LinkedIn to examine much more exclusive content material we article.
Some areas of this short article are sourced from:
thehackernews.com


 Fenix Cybercrime Group Poses as Tax Authorities to Target Latin American Users
Fenix Cybercrime Group Poses as Tax Authorities to Target Latin American Users