The infamous facts-stealer acknowledged as Vidar is continuing to leverage popular social media services these types of as TikTok, Telegram, Steam, and Mastodon as an intermediate command-and-control (C2) server.
“When a person generates an account on an on the net platform, a exclusive account website page that can be accessed by anybody is generated,” AhnLab Security Unexpected emergency Response Center (ASEC) disclosed in a technological assessment released late very last month. “Menace actors compose determining characters and the C2 deal with in elements of this web page.”
In other text, the method relies on actor-managed throwaway accounts developed on social media to retrieve the C2 deal with.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
An advantage to this technique is that must the C2 server be taken down or blocked, the adversary can trivially get all-around the limitations by environment up a new server and editing the account webpages to allow for the formerly dispersed malware to communicate with the server.
Vidar, very first discovered in 2018, is a commercial off-the-shelf malware that is capable of harvesting a extensive vary of information and facts from compromised hosts. It typically relies on delivery mechanisms like phishing e-mail and cracked program for propagation.
“Right after details selection is full, the extorted information is compressed into a ZIP file, encoded in Base64, and transmitted to the C2 server,” ASEC researchers reported.
What is new in the most up-to-date edition of the malware (variation 56.1) is that the gathered information is encoded prior to exfiltration, a adjust from the prior variants that have been identified to send out the compressed file information in plaintext format.
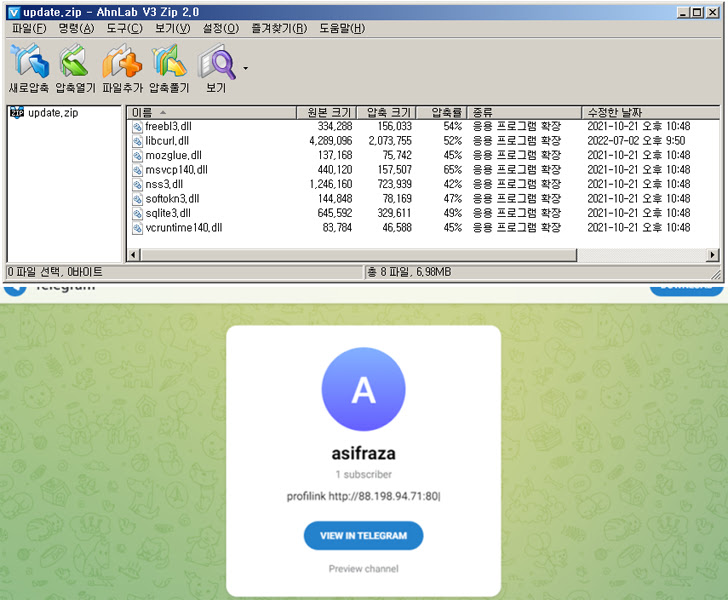
“As Vidar utilizes renowned platforms as the middleman C2, it has a lengthy lifespan,” the scientists reported. “A risk actor’s account designed 6 months in the past is nonetheless currently being preserved and continuously updated.”
The enhancement arrives amid latest conclusions that the malware is becoming dispersed applying a wide range of strategies, including malicious Google Adverts and a malware loader dubbed Bumblebee, the latter of which is attributed to a menace actor tracked as Unique Lily and Projector Libra.
Risk consulting firm Kroll, in an assessment revealed last month, said it uncovered an ad for the GIMP open up resource image editor that, when clicked from the Google research result, redirected the victim to a typosquatted domain hosting the Vidar malware.
If anything, the evolution of malware shipping strategies in the risk landscape is in section a response to Microsoft’s determination to block macros by default in Place of work information downloaded from the internet considering the fact that July 2022.
This has led to an increase in the abuse of choice file formats like ISO, VHD, SVG, and XLL in email attachments to bypass Mark of the Web (MotW) protections and evade anti-malware scanning steps.
“Disk impression documents can bypass the MotW function simply because when the files inside of them are extracted or mounted, MotW is not inherited to the data files,” ASEC scientists explained, detailing a Qakbot campaign that leverages a mix of HTML smuggling and VHD file to start the malware.
Located this posting exciting? Abide by us on Twitter and LinkedIn to study much more exclusive information we article.
Some areas of this post are sourced from:
thehackernews.com


 Fortinet and Zoho Urge Customers to Patch Enterprise Software Vulnerabilities
Fortinet and Zoho Urge Customers to Patch Enterprise Software Vulnerabilities