״Defenders consider in lists, attackers believe in graphs,” mentioned John Lambert from Microsoft, distilling the essential change in state of mind between individuals who defend IT units and those people who try out to compromise them.
The standard technique for defenders is to record security gaps immediately connected to their assets in the network and reduce as many as feasible, setting up with the most critical. Adversaries, in contrast, start with the stop goal in head and target on charting the route toward a breach. They will frequently seem for the weakest website link in the security chain to crack in and development the attack from there all the way to the crown jewels.
Security teams ought to embrace the attacker’s perspective to assure their organization’s cybersecurity defenses are ample. Drawing an analogy to a everyday lifestyle case in point, the normal way to defend our house from intrusion is to make sure all the doors are locked. But to validate that your house is secured necessitates testing your security like a burglar: trying to choose the locks, climb by windows, and hunting for destinations where by house keys may possibly be “securely” stored.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Penetration testing serves this will need precisely: it provides an attacker’s see into what can be compromised. The exercise of penetration tests has been close to for decades, assisting to expose how resilient our networks are towards destructive attacks. On the other hand, with modern day enterprises increasing their use of cloud providers, it is just as necessary to implement the strategy of classic penetration testing to the cloud.
The Cloud’s Not a Secure Haven – Know What You Need to have to Protect
Cloud architectures comprise means, identities, and configurations that are outlined programmatically and alter at a immediate pace. As a outcome, the cloud can be a pandora’s box of extra cybersecurity complexity. Whilst the main cloud service companies put into action rigorous security methods, this may possibly crank out a phony feeling of security for businesses, who may perhaps not be informed of their duty for securing their cloud property, as defined by the cloud shared duty product. For these factors, pentesting in the cloud is just as essential as standard network penetration screening – in some circumstances, even more so.
In this blog publish, we check out the primary cloud pentesting making blocks, focusing on how attackers seem for and exploit security gaps in your cloud.
What Your Cloud Pentest Need to Include
Dependent on your chosen cloud services’ shipping product, the bounds of your duty for security might differ. In common conditions, the cloud assistance providers’ duty finishes exactly where your responsibility begins. The cloud provider is responsible for securing the hardware and the fundamental computer software that enables its solutions. You are dependable for protecting everything you produce in the cloud – your knowledge, keys, property, providers, purposes, and configurations. Think about an case in point of employing Lambda functions to develop cloud-indigenous programs in Amazon Web Solutions (AWS). Although AWS addresses security for the compute and storage infrastructure and the Lambda support by itself, it is your duty to make certain that accessibility to your organization’s code and sources is secure. So it can be up to you to assure that your developers are not storing credentials in the functions’ code or surroundings variables that could be employed to compromise delicate knowledge or laterally transfer in the network if intercepted by malicious actors.
To prepare for different breach eventualities, penetration exams should use different beginning points:
- Black Box – the tester has no initial obtain within the cloud atmosphere.
- Grey Box – the tester has the qualifications of a picked user or part as first input to exhibit the opportunity affect (aka “blast radius”) if an identity is compromised.
For corporations with hybrid cloud and on-premises networks, a full and precise comprehending of risk exposure can only be achieved with the means to exam attack paths that cross between these environments. For example, an On-Prem machine is compromised, and the attacker operates an RCE to harvest qualifications from the equipment. Making use of browser password extraction, the attacker gains the qualifications of a developer with privileges on an Azure VM. From there, the street to breach the cloud is paved, and this approach is recurring on various devices right until the attacker gets a keep of the optimum privileges in the ecosystem and can leverage any useful resource at will. Hence, cloud penetration exams ought to cover eventualities exactly where preliminary obtain on-premises could lead an attacker to compromise cloud assets and vice-versa.
Below are 5 vital creating blocks for cloud penetration screening:
1. Reconnaissance & Discovery
This initially stage involves mapping all the property within your organization’s cloud natural environment workloads, storage, databases, and identities. The information and facts gathered in this section provides the scope of belongings that can be applied or specific inside a exam and a baseline for initiating attack actions.
In standard network pentesting, the examination scope is usually defined by the IP addresses of the endpoints to be bundled in the exam. Cloud resources, in contrast, are discovered by distinctive identifiers, and entry to them is enabled by using APIs. Hence, the standard solution for reconnaissance in cloud pentests is to gather the asset info at the commencing of a take a look at by connecting to the organization’s cloud API.
2. Vulnerability Evaluation
Cloud configuration reviews and vulnerability scans should be done to uncover misconfigurations and recognised program vulnerabilities throughout your cloud belongings. For instance, cloud network security need to be evaluated by assessing the configuration of controls like firewalls, virtual non-public networks (VPNs), accessibility, and network segmentation settings. This process is required to establish weaknesses these types of as publicly available methods or insecure Virtual Private Cloud (VPC) peering connections, which could permit unauthorized access, lateral motion, privilege escalation, and info exfiltration.
A further source at high risk is web applications, which are typically specific by hackers as, by layout, they are open to the Internet. To validate that the security controls and software security implementations never let unauthorized accessibility to products and services and sensitive details, penetration testing ought to include cloud-hosted web purposes. Testing must contain OWASP Leading 10 security pitfalls, such as input validation, SQL injection, cross-website scripting (XSS), and Server-Aspect Request Forgery (SSRF).
On the other hand, vulnerability scans are just the beginning. Detected misconfigurations and vulnerabilities require to be examined for exploitability, aiming to propagate an attack specifically like an adversary would. For instance, if a publicly obtainable cloud storage bucket is detected, it can then be examined by scanning its content for useful techniques or attempting to exfiltrate details.
3. Privilege Escalation
Privilege escalation strategies can grant adversaries entry to much more delicate knowledge, applications, and solutions. Attackers attempt to attain higher privileges by:
- Exploiting vulnerabilities and misconfigurations that are designed to acquire greater privileges in the network
- Gaps in identification and obtain management (IAM), these kinds of as people that are in teams they should really not be in and roles that are overly permissive
- Compromising identities with increased privileges via credential harvesting – a set of techniques that will involve locating and exposing credentials, keys, and session tokens improperly saved across various sources, together with but not restricted to data files, shell background, registry, setting variables, deployment equipment, and browsers.
When privilege escalation is a prevalent attack method applied in common networks, the obstacle of securing identities and obtain to reduce these types of attacks in the cloud is exponentially greater.
Very first, the complexity of cloud IAM architectures is considerably bigger. The abundance of human and equipment identities and intricate accessibility manage policies put in location to support automatic orchestration of cloud sources are probably to introduce pitfalls that attackers can easily exploit. Not only that, but the mixture of Cloud and On-Prem Obtain controls can lead to a quite complex rule system, and attackers prosper on complexity.
Second, developers using cloud infrastructure to build their apps normally put hardcoded tricks in their code and may possibly ignore or neglect to clear away them, exposing them to malicious actors.
4. Lateral Motion
Tests really should determine achievable paths among cloud methods, which adversaries can leverage to collect further delicate info or insider secrets and advance their attacks.
In hybrid surroundings tests scenarios, lateral motion tactics can be tried as a implies to pivot from on-premises to cloud or vice versa. Hence preserving the cloud environment as a silo won’t get the job done. Corporations might be impacted by attacks propagating across the complete attack surface area – the internal network, exterior-facing assets, and cloud environments. Adversaries don’t look at the organizational attack surfaces as disconnected entities but alternatively as a person surface, so defenders have to have to consider a related approach, functioning throughout domains to intercept attacks. To safe the cloud, one should validate all the inroads that lead to it.
5. Information Collection and Exfiltration
Info assortment in cloud computing refers to the accumulating of knowledge from various assets, mainly sensitive in character, this kind of as credit cards, private details, passwords and so on. This is the major motive attackers break into a network, to get a keep of sensitive info. In some cases the adversaries will shop the information in a centralized place, as a preliminary stage to focus the info they would like to exfiltrate.
A cloud pentest need to assess the capacity to collect and then exfiltrate knowledge to an exterior area and validate the network security controls to test whether they avoid exfiltration to identified IOCs.
Cloud Pentesting: Keys to Accomplishment
As you begin the cloud penetration screening journey, it is important that you shell out some time comprehension the scope of your cloud companies and property, and what elements of the attack area are in your fingers to safeguard according to the shared responsibility model. It is then probable to make informed conclusions on cloud-pentesting investments within just the context of your organization’s risk exposure.
As a final note, the effectiveness of a cloud pentesting application is not only decided by the depth and breadth of tests, but also by the screening frequency. The rate of alter in on-premises networks is serving as a blow to the success of prolonged manual penetration testing cycles. In the cloud, it truly is a knockout. Just like cloud and R&D groups are automating their cloud functions and deployments, security groups will have to change gears to automating their cloud penetration testing pursuits and, eventually, complement the Ongoing Integration/Continuous Deployment loop with Continual Validation.
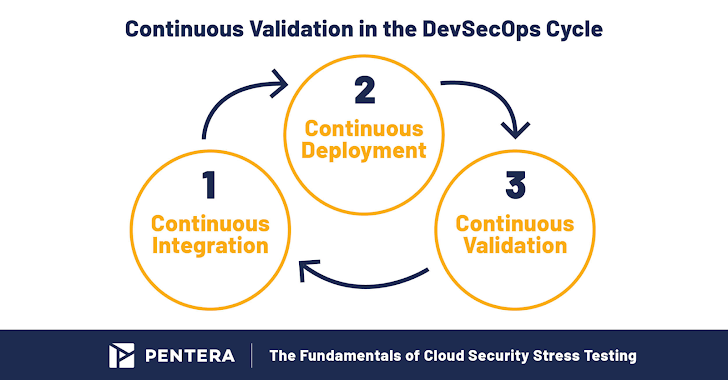
To confidently validate your firm’s resilience to cloud-native attacks, master more about Pentera Cloud, and listen to the On-demand from customers recording about Putting Cloud Security to the Tension Exam.
Located this article interesting? This report is a contributed piece from a person of our valued partners. Stick to us on Twitter and LinkedIn to go through extra exceptional content material we post.
Some sections of this article are sourced from:
thehackernews.com


 Hackers Exploiting LiteSpeed Cache Bug to Gain Full Control of WordPress Sites
Hackers Exploiting LiteSpeed Cache Bug to Gain Full Control of WordPress Sites