In today’s electronic landscape, all around 60% of company data now resides in the cloud, with Amazon S3 standing as the backbone of facts storage for many big companies.
Inspite of S3 being a safe support from a reliable provider, its pivotal role in dealing with huge quantities of delicate facts (buyer personalized information and facts, money data, mental assets, etc.), presents a juicy focus on for risk actors. It remains prone to ransomware attacks which are frequently initiated employing leaked obtain keys that have unintentionally been exposed by human error and have access to the organization’s buckets.
To proficiently fight these evolving threats, it is vital to be certain that your organization has visibility into your S3 natural environment, that you are conscious of how menace actors can compromise facts for ransom and most importantly, very best tactics for minimizing the risk of cyber criminals correctly executing such an attack.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Making certain Visibility: CloudTrail and Server Entry Logs
Visibility serves as the basis for any helpful detection technique. In Amazon S3, nearly every single motion translates to an API connect with, which are meticulously recorded in CloudTrail and documented in AWS documentation.
The two main choices for logging action in S3 buckets — CloudTrail Data Occasions and Server Entry Logs — maintain a wealth of data that security practitioners need to leverage to foresee and detect suspicious action. Every single give unique strengths and trade-offs:
- Cloud Path Info Events: supply visibility into useful resource operations performed on or inside of a source in serious-time, but will come with potential cost implications because of to substantial API phone volumes
- Server Entry Logs: cost-free access to documents for each individual ask for manufactured to your S3 bucket, but occur with probable delays in log availability and probable logging with less integrity.
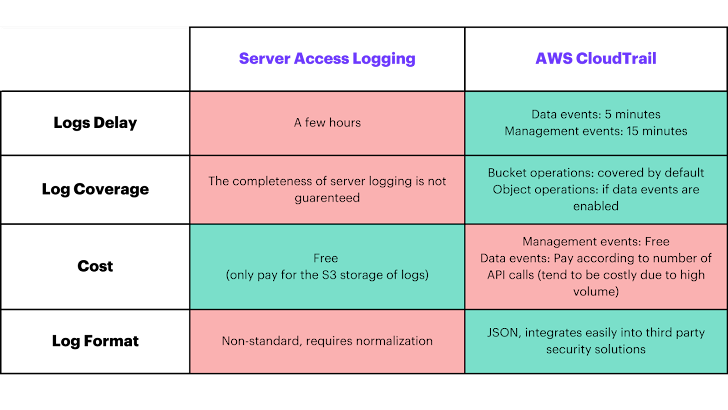 The benefits and trade-offs concerning Server Obtain Logs and AWS CloudTrial logs.
The benefits and trade-offs concerning Server Obtain Logs and AWS CloudTrial logs.
Mitigating Risk by Understanding the Attack Situations
Using the previously mentioned logs to make sure enough visibility, it is achievable to preserve an eye out for likely attack situations in buy to mitigate threats proficiently. There are a few key attack eventualities that we observe with S3 ransomware attacks, all which can avoid an firm from accessing its info. Down below are the attack scenarios, along with back links to searching queries that the qualified threat searching group from Hunters’ Workforce Axon has shared publicly that make it possible for any individual to lookup for these attack scenarios inside of their possess environments:
*Take note: Item Encryption and Object Deletion – Delete Functions demand enabling Cloudtrail Information Situations for the appropriate buckets.
Each individual circumstance poses major disruptions, probably preventing corporations from accessing critical data. By delving into the demanded permissions, attacker perspectives, and detection methods for each and every situation, companies can proactively put together for potential threats.
Defense and Finest Procedures
Knowing the attack eventualities assists to offer context for how to carry out proactive actions to significantly minimize the attack surface area. There are a number of matters that can be finished to enhance the security of S3 buckets from the risk of ransomware.
- Use IAM roles for quick-expression credentials: steer clear of working with static IAM accessibility keys. If you are utilizing IAM users, be sure to help Multi-Factor Authentication (MFA) for them.
- Adhere to the principle of least privilege: this makes certain that end users and roles only possess the permissions required for their responsibilities. Furthermore, make the most of bucket insurance policies to restrict entry to these crucial assets.
- Enable S3 Versioning: this indicates retaining file of every model of each and every item stored in your bucket as a substitute of immediately modifying it. This is extremely successful versus unauthorized override or deletions.
- Help S3 Item Lock: running on a create-at the time, go through-quite a few (WORM) model, indicates that your info can’t be deleted by any one (the details is “locked”) which safeguards from modifications for defined time periods.
- Set up AWS Backup/Bucket Replication: this can be any form of backup that is different in locale and entry regulate from your actual bucket.
- Employ server-aspect encryption with AWS KMS keys: this presents your corporation with unique management more than who can obtain bucket objects. This supplies still one more level of security against who can encrypt and decrypt objects in your bucket.
Summary
As facts volumes carry on to surge, securing Amazon S3 is paramount in safeguarding hundreds of thousands of companies from ransomware attacks and evolving cyber threats.
Prioritizing threats, guaranteeing visibility through CloudTrail and Server Accessibility Logs, and implementing proactive steps are essential methods in mitigating risk. By adopting these approaches, companies can fortify their S3 buckets’ security and assure the integrity and security of their critical information.
For a a lot more in depth breakdown of common attack eventualities and very best methods, check out out a online video deep dive from Team Axon. Staff Axon is the pro risk searching arm of the well-known SIEM substitute Hunters, and offers immediate response to rising cyber threats, on-demand cyber skills and proactive threat searching across customers’ environments. Follow Staff Axon on X for well timed updates on rising cyber threats and premiere cyber material.
Extra S3 Methods:
- AWS Buyer Playbook (GitHub)
- Incident Reaction Workshop for S3 ransomware (AWS)
Found this report exciting? Observe us on Twitter and LinkedIn to browse more distinctive content material we write-up.
Some sections of this report are sourced from:
thehackernews.com


 Act Now: VMware Releases Patch for Critical vCenter Server RCE Vulnerability
Act Now: VMware Releases Patch for Critical vCenter Server RCE Vulnerability