Critical security flaws have been disclosed in the Open Authorization (OAuth) implementation of preferred on the internet companies such as Grammarly, Vidio, and Bukalapak, building upon earlier shortcomings uncovered in Scheduling[.]com and Expo.
The weaknesses, now resolved by the respective firms next liable disclosure between February and April 2023, could have authorized destructive actors to obtain access tokens and probably hijack consumer accounts.
OAuth is a common that is typically utilized as a system for cross-application access, granting web sites or apps obtain to their info on other internet websites, these kinds of as Fb, but devoid of supplying them the passwords.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“When OAuth is utilized to present assistance authentication, any security breach in it can lead to identification theft, financial fraud, and obtain to many individual details which include credit card quantities, personal messages, well being information, and much more, depending on the specific services currently being attacked,” Salt Security researcher Aviad Carmel claimed.
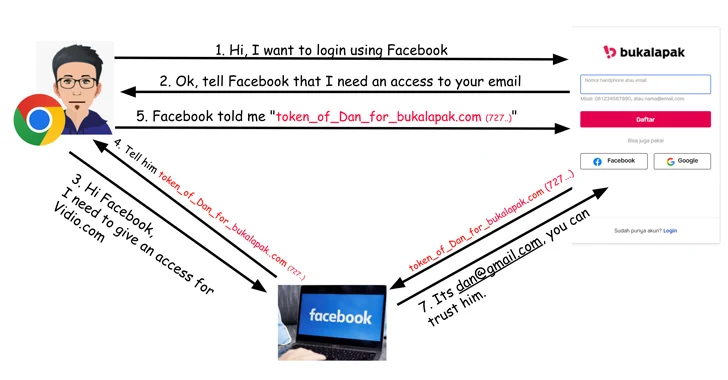
The challenge identified in Vidio stems from an absence of token verification, which means an attacker can use an access token created for a different Application ID, a random identifier produced by Fb for each software or web site that gets registered in its developer portal.
In a potential attack circumstance, a menace actor could generate a rogue web site that offers a sign-in option as a result of Fb to acquire the accessibility tokens and subsequently use them versus Vidio.com (which has the Application ID 92356), thereby allowing full account takeover.
The API security business stated it also found out a equivalent issue with token verification on Bukalapak.com through Fb login that could end result in unauthorized account obtain.

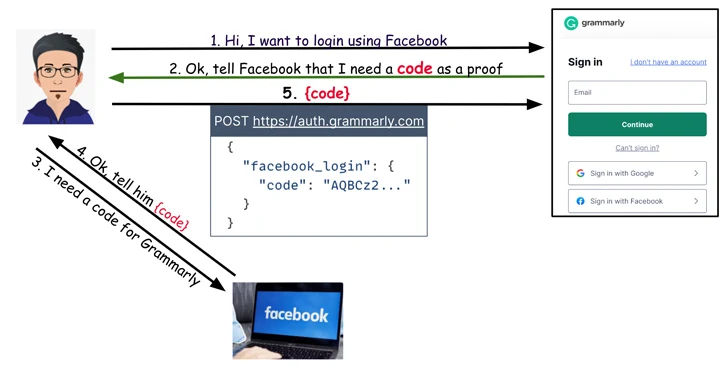
On Grammarly, it emerged that when users attempt to login to their accounts making use of the “Indicator in with Facebook” solution, an HTTP Post ask for is despatched to auth.grammarly[.]com to authenticate them using a secret code.
As a result, whilst Grammarly is not susceptible to a token reuse attack like in the circumstance of Vidio and Bukalapak, it is however susceptible to a unique kind of trouble whereby the Write-up ask for can be altered to substitute the magic formula code with an access token attained from the aforementioned destructive web-site to obtain accessibility to the account.
“And like with the other web pages, the Grammarly implementation did not conduct token verification,” Carmel said, adding, “an account takeover would give an attacker accessibility to the victim’s stored files.”
Observed this post exciting? Follow us on Twitter and LinkedIn to read through much more exclusive written content we write-up.
Some elements of this article are sourced from:
thehackernews.com

 The Rise of S3 Ransomware: How to Identify and Combat It
The Rise of S3 Ransomware: How to Identify and Combat It