Customers of Mirth Hook up, an open up-supply facts integration system from NextGen Healthcare, are staying urged to update to the latest version pursuing the discovery of an unauthenticated distant code execution vulnerability.
Tracked as CVE-2023-43208, the vulnerability has been resolved in variation 4.4.1 produced on Oct 6, 2023.
“This is an very easily exploitable, unauthenticated distant code execution vulnerability,” Horizon3.ai’s Naveen Sunkavally explained in a Wednesday report. “Attackers would most very likely exploit this vulnerability for original access or to compromise delicate health care data.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Termed the “Swiss Military knife of healthcare integration,” Mirth Link is a cross-platform interface motor made use of in the health care industry to connect and exchange data amongst disparate systems in a standardized method.

Further technological information about the flaw have been withheld in gentle of the truth that Mirth Join variations going as significantly again as 2015/2016 have been discovered to be vulnerable to the issue.
It is really value noting that CVE-2023-43208 is a patch bypass for CVE-2023-37679 (CVSS rating: 9.8), a critical remote command execution (RCE) vulnerability in the program that makes it possible for attackers to execute arbitrary commands on the hosting server.
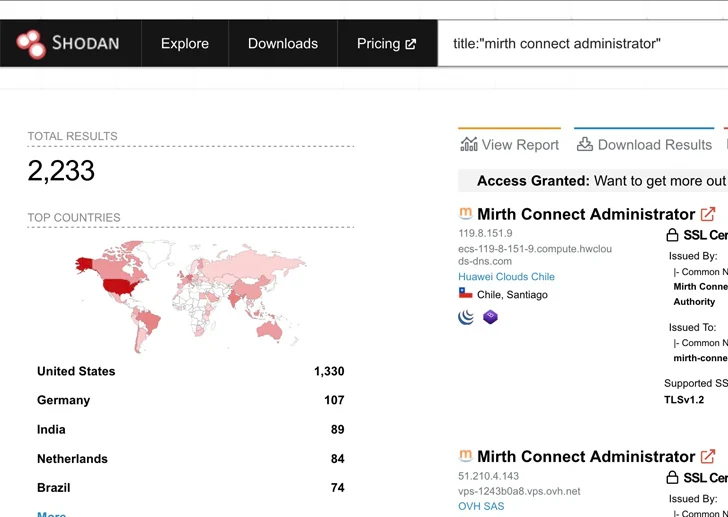
Even though CVE-2023-37679 was explained by its maintainers as only influencing servers running Java 8, Horizon3.ai’s investigation located that all cases of Mirth Connect, irrespective of the Java version, were prone to the issue.
Given the ease with which the vulnerability can be trivially abused, coupled with the point that the exploitation strategies are well identified, it’s encouraged to update Mirth Link, especially that are publicly obtainable around the internet, to edition 4.4.1 as shortly as possible to mitigate potential threats.
Observed this post interesting? Abide by us on Twitter and LinkedIn to browse much more unique material we publish.
Some areas of this post are sourced from:
thehackernews.com


 YoroTrooper: Researchers Warn of Kazakhstan’s Stealthy Cyber Espionage Group
YoroTrooper: Researchers Warn of Kazakhstan’s Stealthy Cyber Espionage Group