The Iranian risk actor recognized as Tortoiseshell has been attributed to a new wave of watering gap attacks that are designed to deploy a malware dubbed IMAPLoader.
“IMAPLoader is a .NET malware that has the means to fingerprint target units using native Windows utilities and acts as a downloader for further more payloads,” the PwC Danger Intelligence claimed in a Wednesday assessment.
“It makes use of email as a [command-and-control] channel and is capable to execute payloads extracted from email attachments and is executed by way of new assistance deployments.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Energetic considering that at least 2018, Tortoiseshell has a record of utilizing strategic web site compromises as a ploy to facilitate the distribution of malware. Earlier this May possibly, ClearSky linked the group to the breach of 8 sites associated with shipping and delivery, logistics, and fiscal services businesses in Israel.
The risk actor is aligned with the Islamic Groundbreaking Guard Corps (IRGC) and is also tracked by the broader cybersecurity local community beneath the names Crimson Sandstorm (earlier Curium), Imperial Kitten, TA456, and Yellow Liderc.
The most current established of attacks among 2022 and 2023 entails embedding destructive JavaScript in compromised reputable internet websites to get much more particulars about the site visitors, such as their spot, machine information and facts, and time of visits.
These intrusions targeted largely on the maritime, delivery and logistics sectors in the Mediterranean, in some instances major to the deployment of IMAPLoader as a adhere to-on payload ought to the target be considered a superior-value goal.
IMAPLoader is claimed to be a substitution to a Python-centered IMAP implant Tortoiseshell previously utilized in late 2021 and early 2022, owing to the similarities in the performance.

The malware acts as a downloader for next-phase payloads by querying difficult-coded IMAP email accounts, specially examining a mailbox folder misspelled as “Recive” to retrieve the executables from the information attachments.
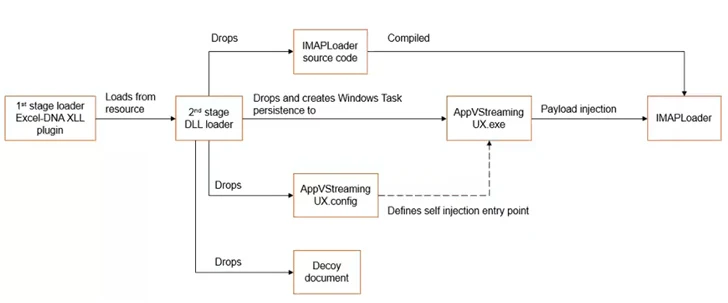
In an alternate attack chain, a Microsoft Excel decoy document is applied as an original vector to kick-start a multi-stage method to supply and execute IMAPLoader, indicating that the threat actor is making use of a assortment of ways and techniques to comprehend its strategic ambitions.
PwC reported it also uncovered phishing web pages designed by Tortoiseshell, some of which are aimed at the journey and hospitality sectors in just Europe, to conduct credential harvesting applying phony Microsoft indication-in web pages.
“This threat actor stays an energetic and persistent risk to numerous industries and international locations, such as the maritime, transport, and logistics sectors inside the Mediterranean nuclear, aerospace, and protection industries in the U.S. and Europe and IT managed provider companies in the Center East,” PwC stated.
Discovered this short article intriguing? Comply with us on Twitter and LinkedIn to read through far more exclusive written content we submit.
Some areas of this post are sourced from:
thehackernews.com


 Critical Flaw in NextGen’s Mirth Connect Could Expose Healthcare Data
Critical Flaw in NextGen’s Mirth Connect Could Expose Healthcare Data