The most precious asset in modern information and facts age is the magic formula safeguarded beneath lock and essential. Regrettably, retaining tricks has develop into ever more complicated, as highlighted by the 2023 Condition of Secrets Sprawl report, the premier investigation of general public GitHub action.
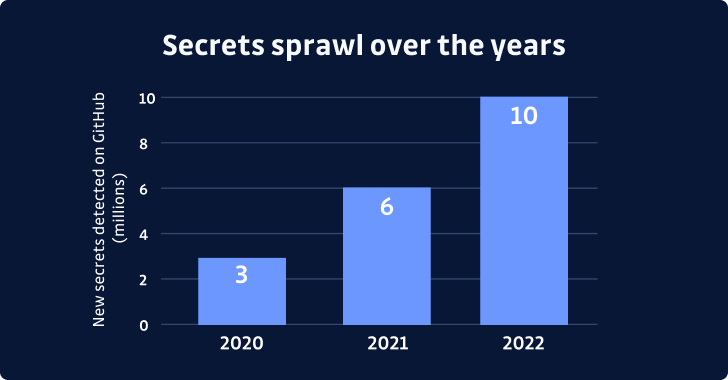
The report demonstrates a 67% 12 months-more than-yr increase in the amount of insider secrets located, with 10 million challenging-coded secrets and techniques detected in 2022 by yourself. This alarming surge in secrets and techniques sprawl highlights the need for motion and underscores the value of secure software development.
Secrets sprawl refers to techniques showing up in plaintext in many sources, these types of as supply code, develop scripts, infrastructure as code, logs, etcetera. When secrets like API tokens and personal keys securely hook up the parts of the fashionable computer software supply chain, their common distribution among builders, equipment, applications, and infrastructure techniques heightens the likelihood of leaks.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Cybersecurity Incidents Emphasize the Hazards of Tough-Coded Secrets and techniques
Two significant-profile cybersecurity incidents involving Uber and Toyota have underlined the urgent have to have to handle the issue of secrets sprawl and prioritize code security. As consciousness all over this issue grows, it is essential for providers to prioritize the safety of tricks and invest in impressive alternatives that detect and remediate prospective threats.
Uber endured an attack in which an attacker gained access to critical systems applying tricky-coded admin qualifications found in a PowerShell script. In contrast, Toyota inadvertently uncovered qualifications granting obtain to purchaser info in a public GitHub repository for pretty much five years. The two incidents serve as obvious reminders of the threats related with insider secrets sprawl. Also, as the report details out, most security incidents entail, at some level, insider secrets: it may well be keys leveraged by attackers or uncovered as a result of leaked supply code, for occasion.
A Major Blind Place in Application Security
With 1 out of every single 10 code authors exposing a solution in 2022, it truly is apparent that this issue transcends working experience degrees and afflicts builders across the board.
Tricks administration is gaining increased attention as far more corporations scrutinize their application source chain procedures subsequent a string of large-profile security breaches. Cybersecurity teams have ordinarily centered on figuring out vulnerabilities somewhat than uncovering inadequately secured qualifications. As a outcome, numerous programs running in creation environments could have undiscovered secrets and techniques management issues.
In a excellent scenario, adopting DevSecOps best procedures would handle this escalating issue. Nevertheless, with the constant enlargement of code repositories, much more primary faults appear. Recognizing software provide chain vulnerabilities, cybercriminals proactively scan repositories to obtain strategies that could facilitate software breaches.
The issue will very likely worsen as attacks on software package source chains are expected to escalate. As technology improvements and code will become more entwined with our daily lives, the pitfalls associated with secrets and techniques sprawl turn into extra urgent.
The intensified concentrate on securing software package provide chains, primarily in light of the Biden administration’s Nationwide Cybersecurity Method, is expected to drive far more IT businesses to put into action conclusion-to-close security measures inside of their software package growth lifetime cycles. As a outcome, DevOps groups must anticipate anincreased emphasis on secrets and techniques administration from cybersecurity authorities.
Embracing Proactive Actions to Mitigate Tricks Sprawl Hazards
To fight this increasing risk, companies must prioritize the defense of their techniques and make investments in answers for detecting and addressing prospective vulnerabilities.
The ongoing advancement of the every little thing-as-code paradigm and the commoditization of digital infrastructure and services means that software program, code, and secrets and techniques will only turn out to be far more critical in their day-to-day organization operations.
The risk of insider secrets exposure are not able to fully be removed, even with centralized magic formula management units. But it can be mitigated by addressing very poor secrets hygiene procedures and implementing remediation playbooks.
To measure how substantially a strategies detection and remediation method could deliver to your corporation, you can use our free Value Calculator to estimate the probable price tag of not working with a security financial debt consisting of 1000’s of tough-coded strategies these days.
By finding out to live with this issue and placing the correct instruments and means in area, businesses can appreciably lower the hazards involved with leaked and exploited secrets.
In conclusion, tricks sprawl is a rising risk requiring organizations’ rapid focus. With the ideal instruments and approaches in location, organizations can mitigate the risks involved with leaked and exploited strategies. It really is time to prioritize techniques administration and invest in revolutionary answers to guarantee our techniques remain secure and safe.
In a planet where information is ability, it can be time to just take motion and ensure our secrets and techniques continue being safely underneath lock and important.
Discovered this write-up attention-grabbing? Comply with us on Twitter and LinkedIn to read a lot more unique material we article.
Some pieces of this report are sourced from:
thehackernews.com

 New WinTapix.sys Malware Engages in Multi-Stage Attack Across Middle East
New WinTapix.sys Malware Engages in Multi-Stage Attack Across Middle East