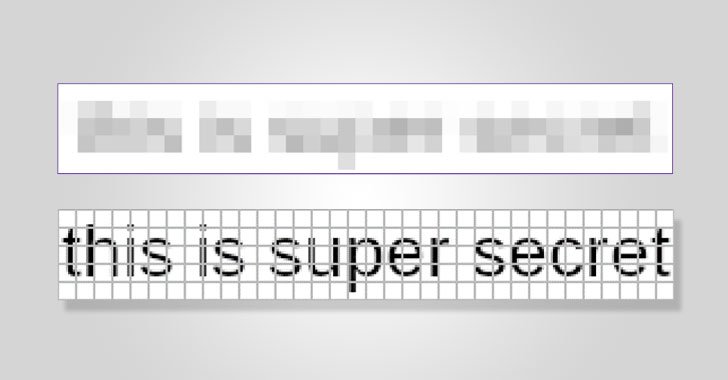
The practice of blurring out text making use of a process termed pixelation may perhaps not be as safe as earlier considered.
Though the most foolproof way of concealing sensitive textual information is to use opaque black bars, other redaction strategies like pixelation can attain the opposite outcome, enabling the reversal of pixelized text again into its authentic type.
Dan Petro, a guide researcher at offensive security agency Bishop Fox, has demonstrated a new open up-source software termed Unredacter to reconstruct text from the pixelated illustrations or photos, successfully leaking the incredibly information and facts that was meant to be guarded.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The resource is also seen as an improvement around an present utility named Depix, which performs by on the lookout up what permutations of pixels could have resulted in specific pixelated blocks to recuperate the textual content.
The menace product operates on the underlying hypothesis that given a piece of text that contains each redacted and un-redacted information and facts, the attacker uses the data about the font dimensions and style gleaned from the distinct textual content to predict the hid data.
This is significantly from the to start with time very similar procedures have been proposed to get back again redacted facts from pixelated material. In January 2022, researchers from Beneficial Security in-depth a approach to reverse pixelation in videos.
“Information creators and journalists ought to be knowledgeable of the added dangers when redacting details in films and use a adequately high mosaic dimension/blur radius, or greater nevertheless, use an opaque, solitary-colored box,” researcher Fabian Braunlein mentioned.
Petro concurs. “The base line is that when you need to have to redact textual content, use black bars covering the entire textual content. By no means use anything else. No pixelation, no blurring, no fuzzing, no swirling.”
“The very last point you will need just after producing a fantastic technological document is to unintentionally leak delicate information and facts simply because of an insecure redaction technique,” Petro additional.
Located this short article appealing? Comply with THN on Facebook, Twitter and LinkedIn to read additional distinctive material we write-up.
Some areas of this short article are sourced from:
thehackernews.com



 Researchers Warn of a New Golang-based Botnet Under Continuous Development
Researchers Warn of a New Golang-based Botnet Under Continuous Development