A financially enthusiastic cyber actor has been noticed abusing Microsoft Azure Serial Console on virtual machines (VMs) to put in third-party distant management resources within just compromised environments.
Google-owned Mandiant attributed the action to a threat team it tracks under the name UNC3944, which is also recognized as Roasted 0ktapus and Scattered Spider.
“This strategy of attack was exclusive in that it averted lots of of the standard detection solutions utilized inside of Azure and provided the attacker with full administrative obtain to the VM,” the danger intelligence firm explained.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The emerging adversary, which first came to light in late final 12 months, is recognised to leverage SIM swapping attacks to breach telecommunications and company procedure outsourcing (BPO) businesses considering the fact that at the very least Could 2022.
Subsequently, Mandiant also observed UNC3944 employing a loader named STONESTOP to install a destructive signed driver dubbed POORTRY which is built to terminate procedures linked with security application and delete data files as component of a BYOVD attack.
It is really at present not recognized how the risk actor conducts the SIM swaps, while the preliminary accessibility methodology is suspected to require the use of SMS phishing messages targeting privileged end users to get their credentials and then staging a SIM swap to get the two-factor authentication (2FA) token to a SIM card under their handle.
Armed with the elevated entry, the threat actor then moves to survey the goal network by exploiting Azure VM extensions these as Azure Network Watcher, Azure Windows Visitor Agent, VMSnapshot, and Azure Plan guest configuration.
Impending WEBINARLearn to Prevent Ransomware with True-Time Protection
Sign up for our webinar and study how to cease ransomware attacks in their tracks with authentic-time MFA and assistance account security.
Save My Seat!
“As soon as the attacker completes their reconnaissance, they hire the serial console operation in buy to achieve an administrative command prompt inside of an Azure VM,” Mandiant explained, incorporating it noticed UNC3944 making use of PowerShell to deploy legitimate distant administration tools.
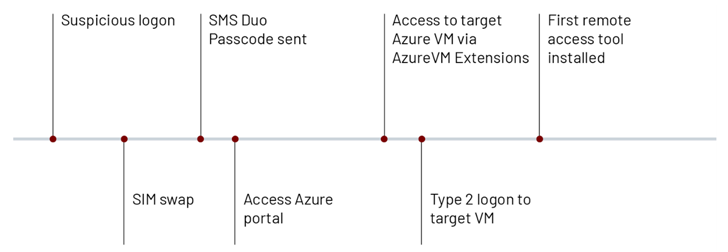
The development is but yet another proof of attackers taking benefit of residing-off-the-land (LotL) approaches to maintain and advance an attack, when at the same time circumventing detection.
“The novel use of the serial console by attackers is a reminder that these attacks are no longer constrained to the operating system layer,” Mandiant claimed.
“Sad to say, cloud sources are often improperly misunderstood, main to misconfigurations that can leave these assets vulnerable to attackers. Even though strategies of preliminary entry, lateral motion, and persistence range from one attacker to another, 1 detail is very clear: Attackers have their eyes on the cloud.”
Identified this short article appealing? Abide by us on Twitter and LinkedIn to read through more special content material we write-up.
Some elements of this write-up are sourced from:
thehackernews.com

 Serious Unpatched Vulnerability Uncovered in Popular Belkin Wemo Smart Plugs
Serious Unpatched Vulnerability Uncovered in Popular Belkin Wemo Smart Plugs