Extremely skilled program and cellular app developers from the Democratic People’s Republic of Korea (DPRK) are posing as “non-DPRK nationals” in hopes of landing freelance employment in an try to empower the regime’s malicious cyber intrusions.
That’s according to a joint advisory from the U.S. Division of Condition, the Office of the Treasury, and the Federal Bureau of Investigation (FBI) issued on Monday.
Targets include things like money, wellbeing, social media, sporting activities, amusement, and life style-concentrated businesses located in North The usa, Europe, and East Asia, with most of the dispatched staff positioned in China, Russia, Africa, and Southeast Asia.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The target, the U.S. companies alert, is to deliver a continual stream of earnings that sidesteps intercontinental sanctions imposed on the country and assist provide its economic and security priorities, together with the enhancement of nuclear and ballistic missiles.
“The North Korean government withholds up to 90 percent of wages of abroad workers which generates an annual earnings to the government of hundreds of thousands and thousands of pounds,” the guidance famous.
Some of the core spots the place DPRK IT staff have been identified to interact are software program development crypto platforms graphic animation on line gambling mobile game titles relationship, AI, and VR apps hardware and firmware growth biometric recognition computer software and database management.
DPRK IT personnel are also known to get on jobs that involve digital currency, reflecting the country’s ongoing curiosity in the technology and its heritage of specific attacks aimed at the economic sector.
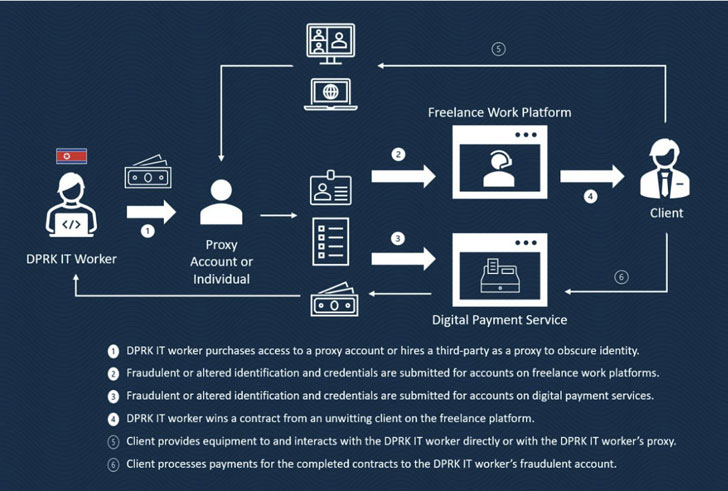
In addition, they are mentioned to abuse the privileged access acquired as contractors to present logistical assistance to North Korean condition-sponsored teams, share access to virtual infrastructure, aid the sale of stolen knowledge, and guide in money laundering and digital currency transfers.
In addition to intentionally obfuscating their identities, areas, and nationality online by working with VPNs and misrepresenting themselves as South Korean citizens, opportunity purple flags indicating the involvement of DPRK IT personnel are as follows –
- Many logins into one particular account from a variety of IP addresses in a limited time period
- Logging into multiple accounts on the very same system from a person IP tackle
- Logged into accounts consistently for 1 or extra days at a time
- Use of ports these kinds of as 3389 that are related with distant desktop sharing application
- Utilizing rogue consumer accounts on freelance do the job platforms to improve developer account rankings
- Numerous developer accounts acquiring substantial rankings from one particular customer account in a brief time
- Regular cash transfers by way of payment platforms to China-based financial institution accounts, and
- Looking for payment in virtual currency

In just one occasion highlighted in the advisory, North Korean developers doing the job for an unnamed U.S. business carried out an unauthorized theft of over $50,000 in 30 compact installments devoid of the firm’s know-how in excess of the study course of numerous months.
“Employing or supporting the actions of DPRK IT employees poses many dangers, ranging from theft of intellectual home, data, and money to reputational hurt and authorized penalties, like sanctions beneath each United States and United Nations authorities,” the U.S. State Section reported.
The advisory also will come as the office declared a $5 million reward final month for information that prospects to the disruption of North Korea’s cryptocurrency theft, cyber-espionage, and other illicit country-point out activities.
Found this posting fascinating? Abide by THN on Facebook, Twitter and LinkedIn to study far more exceptional written content we put up.
Some pieces of this write-up are sourced from:
thehackernews.com


 Microsoft Warns of “Cryware” Info-Stealing Malware Targeting Crypto Wallets
Microsoft Warns of “Cryware” Info-Stealing Malware Targeting Crypto Wallets