The Vietnamese menace actors behind the Ducktail stealer malware have been linked to a new campaign that ran concerning March and early Oct 2023, focusing on advertising and marketing experts in India with an goal to hijack Facebook business accounts.
“An significant function that sets it aside is that, compared with former campaigns, which relied on .NET applications, this 1 made use of Delphi as the programming language,” Kaspersky explained in a report printed last week.
Ducktail, along with Duckport and NodeStealer, is component of a cybercrime ecosystem working out of Vietnam, with the attackers principally using sponsored advertisements on Fb to propagate destructive ads and deploy malware capable of plundering victims’ login cookies and eventually getting management of their accounts.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
These kinds of attacks generally one out people who may have obtain to a Fb Enterprise account. The fraudsters then use the unauthorized entry to spot commercials for economical attain, perpetuating the bacterial infections even further.

In the campaign documented by the Russian cybersecurity company, prospective targets hunting for a career modify are despatched archive documents that contains a malicious executable that’s disguised with a PDF icon to trick them into launching the binary.
Doing so results in the destructive file preserving a PowerShell script named param.ps1 and a decoy PDF document regionally to the “C:UsersPublic” folder in Windows.
“The script utilizes the default PDF viewer on the system to open up the decoy, pauses for 5 minutes, and then terminates the Chrome browser method,” Kaspersky stated.
The mum or dad executable also downloads and launches a rogue library named libEGL.dll, which scans the “C:ProgramDataMicrosoftWindowsStart MenuPrograms” and “C:ProgramDataMicrosoftInternet ExplorerQuick LaunchUser PinnedTaskBar” folders for any shortcut (i.e., LNK file) to a Chromium-based mostly web browser.
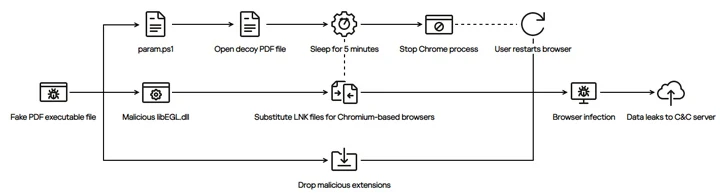
The subsequent stage entails altering the browser’s LNK shortcut file by suffixing a “–load-extension” command line change to start a rogue extension that masquerades as the genuine Google Docs Offline incorporate-on to fly less than the radar.
The extension, for its component, is designed to send out info about all open tabs to an actor-managed server registered in Vietnam and hijack the Fb small business accounts.
Google Sues Scammers for Using Bard Lures to Unfold Malware
The findings underscore a strategic shift in Ducktail’s attack techniques and come as Google filed a lawsuit from a few unfamiliar men and women in India and Vietnam for capitalizing on the public’s desire in generative AI equipment this sort of as Bard to spread malware through Facebook and pilfer social media login credentials.

“Defendants distribute one-way links to their malware through social media posts, advertisements (i.e., sponsored posts), and internet pages, each and every of which purport to provide downloadable variations of Bard or other Google AI solutions,” the firm alleged in its complaint.
“When a consumer logged into a social media account clicks the one-way links displayed in Defendants’ ads or on their webpages, the one-way links redirect to an external internet site from which a RAR archive, a style of file, downloads to the user’s laptop or computer.”
The archive files consist of an installer file that is capable of putting in a browser extension adept at pilfering victims’ social media accounts.
Previously this May perhaps, Meta claimed it noticed danger actors making deceptive browser extensions obtainable in formal web stores that assert to offer ChatGPT-similar applications and that it detected and blocked about 1,000 exceptional URLs from becoming shared across its companies.
Uncovered this article interesting? Comply with us on Twitter and LinkedIn to examine far more distinctive content we post.
Some parts of this posting are sourced from:
thehackernews.com


 CISA Sets a Deadline – Patch Juniper Junos OS Vulnerabilities Before November 17
CISA Sets a Deadline – Patch Juniper Junos OS Vulnerabilities Before November 17