Scientists have issued a warning about an rising and sophisticated form of voice phishing (vishing) recognized as “Letscall.” This system is at present focusing on men and women in South Korea.
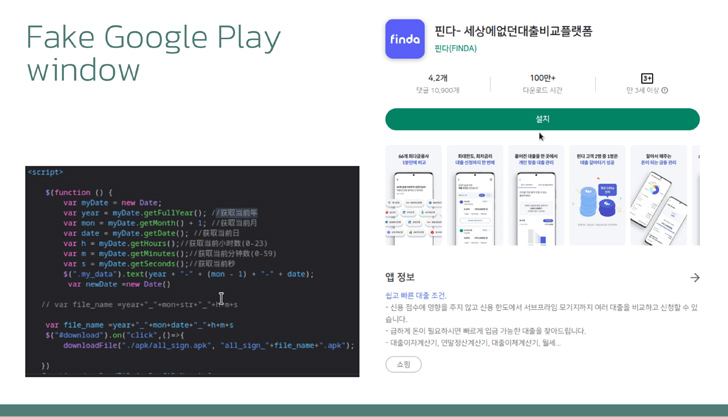
The criminals at the rear of “Letscall” use a multi-step attack to deceive victims into downloading malicious applications from a counterfeit Google Enjoy Retailer web page.
The moment the destructive software is mounted, it redirects incoming calls to a call centre under the command of the criminals. Educated operators posing as financial institution employees then extract sensitive information from unsuspecting victims.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
To aid the routing of voice visitors, “Letscall” makes use of cutting-edge technologies these as voice about IP (VOIP) and WebRTC. It also can make use of Session Traversal Utilities for NAT (STUN) and Traversal Using Relays all-around NAT (Convert) protocols, which includes Google STUN servers, to be certain substantial-quality phone or online video phone calls and bypass NAT and firewall restrictions.
The “Letscall” group is composed of Android developers, designers, frontend and backend developers, as very well as get in touch with operators specializing in voice social engineering attacks.
The malware operates in 3 stages: to start with, a downloader app prepares the victim’s gadget, paving the way for the installation of potent spy ware. This spyware then triggers the ultimate phase, which permits the rerouting of incoming calls to the attackers’ simply call heart.
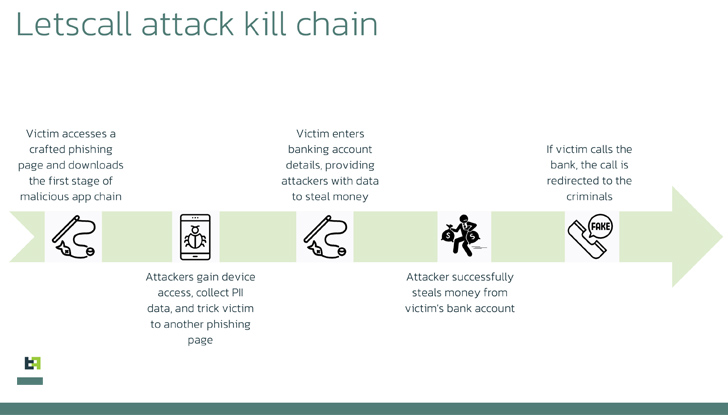
“The third phase has its personal established of instructions, which also consists of Web socket instructions. Some of these instructions relate to the manipulation of the handle guide, these kinds of as building and eradicating contacts. Other instructions relate to producing, modifying, and eliminating the filters that identify which phone calls should be intercepted and which really should be dismissed,” Dutch cell security organization ThreatFabric claimed in its report.
What sets “Letscall” aside is its utilization of highly developed evasion procedures. The malware incorporates Tencent Legu and Bangcle (SecShell) obfuscation all through the first obtain. In afterwards levels, it employs sophisticated naming constructions in ZIP file directories and deliberately corrupts the manifest to confuse and bypass security systems.
Criminals have created programs that instantly contact victims and engage in pre-recorded messages to more deceive them. By combining cellular phone bacterial infections with vishing approaches, these fraudsters can request micro-loans in the victims’ names though assuring them of suspicious things to do and redirecting phone calls to their facilities.
Approaching WEBINAR🔐 Privileged Access Administration: Study How to Conquer Critical Issues
Learn distinct techniques to conquer Privileged Account Administration (PAM) issues and stage up your privileged obtain security system.
Reserve Your Location
The effects of these types of attacks can be sizeable, leaving victims burdened with sizeable loans to repay. Economical establishments normally undervalue the severity of these invasions and are unsuccessful to examine potential fraud.
Despite the fact that this risk is at this time restricted to South Korea, scientists caution that there are no specialized limitations preventing these attackers from growing to other locations, such as the European Union.
This new type of vishing attack underscores the regular evolution of prison techniques and their ability to exploit technology for destructive reasons. The team accountable for the “Letscall” malware demonstrates intricate know-how of Android security and voice routing technologies.
Discovered this report interesting? Comply with us on Twitter and LinkedIn to examine a lot more distinctive information we article.
Some pieces of this posting are sourced from:
thehackernews.com


 Another Critical Unauthenticated SQLi Flaw Discovered in MOVEit Transfer Software
Another Critical Unauthenticated SQLi Flaw Discovered in MOVEit Transfer Software