VMWare has shipped updates to Workstation, Fusion, and ESXi products to deal with an “crucial” security vulnerability that could be weaponized by a menace actor to choose command of affected programs.
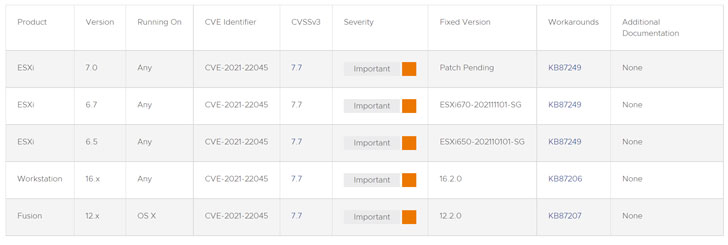
The issue relates to a heap-overflow vulnerability — tracked as CVE-2021-22045 (CVSS score: 7.7) — that, if correctly exploited, outcomes in the execution of arbitrary code. The firm credited Jaanus Kääp, a security researcher with Clarified Security, for reporting the flaw.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“A malicious actor with access to a digital machine with CD-ROM product emulation may possibly be able to exploit this vulnerability in conjunction with other issues to execute code on the hypervisor from a virtual machine,” VMware explained in an advisory printed on January 4.
The error impacts ESXi variations 6.5, 6.7, and 7. Workstation variations 16.x and Fusion versions 12.x, with the business yet to release a patch for ESXi 7.. In the interim, the firm is recommending buyers to disable all CD-ROM/DVD equipment on all working digital equipment to avoid any potential exploitation —
- Log in to a vCenter Server process applying the vSphere Web Client.
- Right-click the virtual machine and click Edit Settings.
- Decide on the CD/DVD travel and uncheck “Connected” and “Hook up at ability on” and remove any connected ISOs.
With VMware’s virtualization answers widely deployed across enterprises, it is no shock that its items have emerged as a common option for risk actors to stage a multitude of attacks in opposition to susceptible networks. To mitigate the risk of infiltration, it is really recommended that corporations transfer promptly to use the required updates.
Identified this posting interesting? Abide by THN on Fb, Twitter and LinkedIn to examine more unique content we article.
Some pieces of this short article are sourced from:
thehackernews.com


 Google Releases New Chrome Update to Patch Dozens of New Browser Vulnerabilities
Google Releases New Chrome Update to Patch Dozens of New Browser Vulnerabilities