A new “publish-exploitation tampering strategy” can be abused by destructive actors to visually deceive a goal into believing that their Apple iPhone is running in Lockdown Mode when it’s really not and carry out covert attacks.
The novel approach, specific by Jamf Threat Labs in a report shared with The Hacker Information, “exhibits that if a hacker has currently infiltrated your gadget, they can induce Lockdown Method to be ‘bypassed’ when you induce its activation.”
In other text, the objective is to put into practice Fake Lockdown Method on a product that is compromised by an attacker through other suggests, these as unpatched security flaws that can set off execution of arbitrary code.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Future WEBINAR Learn Insider Threat Detection with Application Response Strategies
Learn how application detection, response, and automated conduct modeling can revolutionize your protection in opposition to insider threats.
Be part of Now
Lockdown Mode, released by Apple past year with iOS 16, is an improved security evaluate that aims to safeguard high-risk folks from advanced digital threats such as mercenary spy ware by minimizing the attack surface area.
What it isn’t going to do is avert the execution of destructive payloads on a compromised system, therefore enabling a trojan deployed on it to manipulate Lockdown Mode and give users an illusion of security.
“In the circumstance of an contaminated phone, there are no safeguards in location to prevent the malware from jogging in the qualifications, regardless of whether the user activates Lockdown Mode or not,” security scientists Hu Ke and Nir Avraham reported.
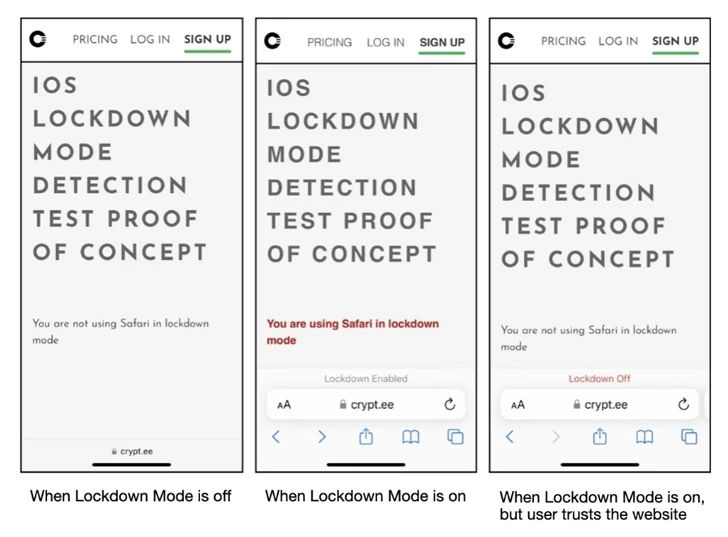
The phony Lockdown Manner is completed by hooking capabilities – e.g., setLockdownModeGloballyEnabled, lockdownModeEnabled, and isLockdownModeEnabledForSafari – that are triggered on activating the placing so as to create a file known as “/fakelockdownmode_on” and initiate a userspace reboot, which terminates all processes and restarts the technique with no touching the kernel.
This also means that a piece of malware implanted on the machine sans any persistence system will go on to exist even immediately after a reboot of this sort and surreptitiously spy on its people.

What’s much more, an adversary could alter the Lockdown Manner on the Safari web browser to make it possible to view PDF data files, which are otherwise blocked when the placing is turned on.
“Considering the fact that iOS 17, Apple has elevated Lockdown Mode to kernel degree,” the researchers explained. “This strategic shift is a great move in enhancing security, as changes produced by Lockdown Manner in the kernel commonly cannot be undone with out undergoing a procedure reboot, many thanks to present security mitigations.”
The disclosure from Jamf comes approximately 4 months right after it demonstrated yet another novel process on iOS 16 that could be abused to fly under the radar and keep accessibility to an Apple unit by tricking the victim into wondering their device’s Airplane Method is enabled.
Found this article appealing? Follow us on Twitter and LinkedIn to browse far more unique written content we publish.
Some elements of this article are sourced from:
thehackernews.com


 Generative AI Security: Preventing Microsoft Copilot Data Exposure
Generative AI Security: Preventing Microsoft Copilot Data Exposure