
Get unique insights from a true ransomware negotiator who shares reliable stories from network hostage situations and how he managed them.
The Ransomware Sector
Ransomware is an field. As this sort of, it has its very own business logic: organizations fork out cash, in crypto-currency, in buy to regain command over their techniques and data.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
This industry’s landscape is created up of somewhere around 10-20 main risk actors who originally produced the ransomware’s malware. To distribute the malware, they get the job done with affiliates and distributors who use common phishing attacks to breach corporations. Earnings are distributed with approximately 70% allotted to the affiliate marketers and 10%-30% to these developers. The use of phishing renders online-centered industries, like gaming, finance and coverage, in particular vulnerable.
In addition to its fiscal motivations, the ransomware business is also influenced by geo-political politics. For illustration, in June 2021, following the ransomware attacks on the Colonial Pipeline and JBS, the Byden administration announced that ransomware was a danger to National Security. The administration then mentioned critical infrastructures that were “off limitations” to attackers.
Subsequent these methods, a variety of menace actors resolved to modify course: declaring they would not attack vital and basic corporations like hospitals, power vegetation and educational establishments. A number of months afterwards, the FBI described they experienced attacked popular ransomware team REvil:
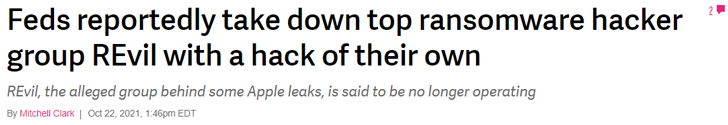
The attack garnered a reaction from the Conti team, which reflected their ideological motives:

Ransomware Vaccinations
Controlling a ransomware celebration is equivalent to controlling a hostage problem. For that reason, to prepare for a ransomware incident, it is advisable for organizations to hire a comparable crisis management construction. This composition is primarily based on the subsequent features:
1. A crisis supervisor:
- Coordinates the technological, organization and legal tracks.
- The technological track consists of forensic, investigation, containment, remediation and recovery, as perfectly as professional dialogue. At this phase, the corporation and the incident response teams evaluate the scope of the party. For example, how deep the attackers are in the technique, how considerably facts was exfiltrated, and so on.
- The business observe addresses organization continuity plans and media and PR. These are usually executed when the scope of the function is clear. It is advisable to be as transparent and precise as achievable when issuing public statements.
- The legal keep track of contains authorized, regulatory and compliance criteria. They keep track of what tips require to be complied and in which time frames. In some cases, they will also be the disaster professionals.
- The disaster supervisor are not able to be the choice-maker.
2. A final decision earning group:
- The group or human being that tends to make knowledgeable conclusions dependent on the details from the crisis supervisor.
3. Legislation enforcement:
- It is encouraged to outline this romantic relationship in advance. The extent could be as nominal as just informing them and as deep as allowing for them to handle the overall disaster.
4. Insurance coverage:
In accordance to Etay Maor, Senior Director Security Approach at Cato Networks, “We’re observing far more and extra corporations featuring bundles of these ransomware products and services. However, it is proposed to separate these roles to ensure the most professional reaction.”
The Part of the Professional Negotiator
Qualified negotiation is the act of using advantage of the experienced conversation with the hacker in a variety of extortion circumstances. The role comprises 4 essential things:
1. Determining the scope of the party – Requires put within just the very first 24-48 hrs. Features understanding what was compromised, how deep the attackers are in the procedure, whether the act is a single, double or triple ransomware, if the attack was financially enthusiastic or if it was a political or private attack, and so on.
In 90% of situations, the attack is financially determined. If it is politically inspired, the data may possibly not be recovered, even right after paying the ransom.
2. Profiling the menace actor – Includes knowledge whether or not the group is identified or not known, their behavioral styles and their organizational structure. Knowing who the attacker is influences communication.
For instance, by locating out what the neighborhood time is for the attacker, the negotiator can recognize in which they came from. This can be made use of for enhancing negotiation conditions, like leveraging general public holidays to talk to for a price reduction.
3. Assessing the “expense-of-no-offer” – Reflecting to the determination makers and the crisis administrators what will occur if they really don’t fork out the ransom.
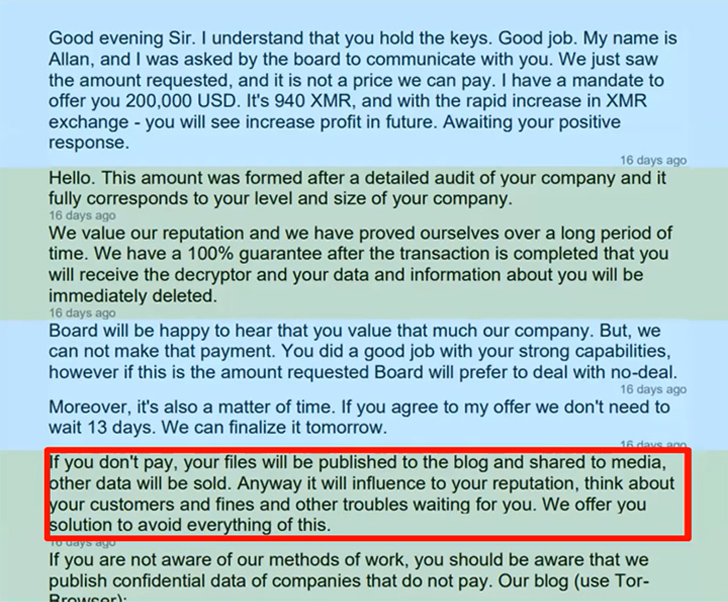
4. Defining negotiation plans – The problem is not regardless of whether to pay out or not. That is a business enterprise final decision. The goals of the negotiations are to negotiate for facts, for time and for greater phrases. Sometimes, this can result in a reduce payment, or even making it possible for the firm to recover on its individual.
For example, 1 enterprise was ready to purchase 13 times as a result of negotiations, allowing for them to get better their information and facts and relinquish having to pay the ransom altogether.
To Shell out or Not to Fork out?
Etay Maor opinions, “Ransomware is not an IT issue, it truly is a enterprise issue. “The determination regardless of whether to spend or not is a business conclusion, motivated by quite a few elements. Whilst the official FBI plan is not to shell out, they allow companies to do so, if the CEO decides.
For case in point, in one case an on the internet gaming organization was dropping extra revenue than the ransom request each and every hour their operations had been down, influencing their final decision to spend the ransom as quickly as probable although minimizing negotiation time. US lawmakers have not banned ransomware payment possibly. This exhibits how complex the issue is.
Tips for Shielding From Ransomware Attacks
Ransomware is getting to be a lot more outstanding, but companies can secure against it. Ransomware relies on phishing attacks and unpatched products and services. Therefore, it is encouraged that CEOs satisfy their IT crew consistently to be certain application and infrastructure are patched and up-to-date and that all crucial data is backed up. This will noticeably lessen the chance of ransomware becoming able to exploit vulnerabilities and penetrate methods.
To discover additional about ransomware attacks and how they are managed in authentic-time, enjoy the full masterclass below.
Identified this report exciting? Follow us on Twitter and LinkedIn to go through extra special content we put up.
Some sections of this posting are sourced from:
thehackernews.com


 Cisco Counterfeiter Pleads Guilty to $100m Scheme
Cisco Counterfeiter Pleads Guilty to $100m Scheme