As numerous as 47,337 destructive plugins have been uncovered on 24,931 exclusive sites, out of which 3,685 plugins ended up bought on respectable marketplaces, netting the attackers $41,500 in unlawful revenues.
The conclusions occur from a new device identified as YODA that aims to detect rogue WordPress plugins and monitor down their origin, in accordance to an 8-12 months-prolonged examine carried out by a group of scientists from the Georgia Institute of Technology.
“Attackers impersonated benign plugin authors and distribute malware by distributing pirated plugins,” the scientists claimed in a new paper titled “Mistrust Plugins You Must.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

“The amount of destructive plugins on websites has steadily amplified more than the many years, and destructive action peaked in March 2020. Shockingly, 94% of the malicious plugins mounted above those 8 yrs are nevertheless lively these days.”
The massive-scale exploration entailed analyzing WordPress plugins put in in 410,122 exceptional web servers dating all the way back again to 2012, discovering that plugins that expense a whole of $834,000 had been infected post-deployment by threat actors.
YODA can be built-in right into a web-site and a web server hosting service provider, or deployed by a plugin market. In addition to detecting concealed and malware-rigged increase-ons, the framework can also be utilized to identify a plugin’s provenance and its ownership.
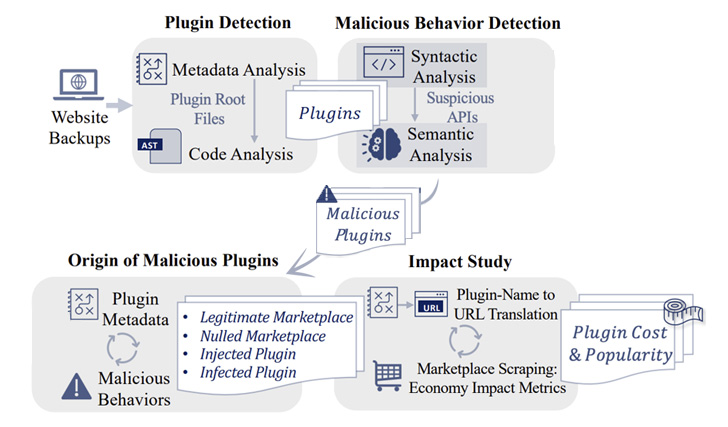
It achieves this by performing an investigation of the server-aspect code files and the associated metadata (e.g., reviews) to detect the plugins, adopted by carrying out a syntactic and semantic evaluation to flag malicious habits.
The semantic model accounts for a vast selection of crimson flags, including web shell, perform to insert new posts, password-guarded execution of injected code, spam, code obfuscation, blackout Search engine optimization, malware downloader, malvertising, and cryptocurrency miners.

Some of the noteworthy conclusions are as follows –
- 3,452 plugins readily available in legitimate plugin marketplaces facilitated spam injection
- 40,533 plugins were being infected article-deployment throughout 18,034 sites
- Nulled plugins — WordPress plugins or themes that have been tampered to down load malicious code on the servers — accounted for 8,525 of the full malicious incorporate-ons, with around 75% of the pirated plugins cheating developers out of $228,000 in revenues
“Using YODA, site house owners and hosting providers can establish destructive plugins on the web server plugin builders and marketplaces can vet their plugins in advance of distribution,” the researchers pointed out.
Observed this write-up exciting? Comply with THN on Facebook, Twitter and LinkedIn to browse much more unique information we put up.
Some elements of this article are sourced from:
thehackernews.com


 Twice as Many Healthcare Organizations Now Pay Ransom
Twice as Many Healthcare Organizations Now Pay Ransom