An intercontinental legislation enforcement operation involving 11 nations has culminated in the takedown of a infamous cell malware menace termed FluBot.
“This Android malware has been spreading aggressively via SMS, stealing passwords, on the net banking specifics and other delicate details from contaminated smartphones throughout the entire world,” Europol stated in a statement.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The “intricate investigation” bundled authorities from Australia, Belgium, Finland, Hungary, Eire, Romania, Spain, Sweden, Switzerland, the Netherlands, and the U.S.
FluBot, also called Cabassous, emerged in the wild in December 2020, masking its insidious intent behind the veneer of seemingly innocuous package deal tracking purposes this kind of as FedEx, DHL, and Correos.
It principally spreads by means of smishing (aka SMS-dependent phishing) messages that trick unsuspecting recipients into clicking on a link to down load the malware-laced applications.
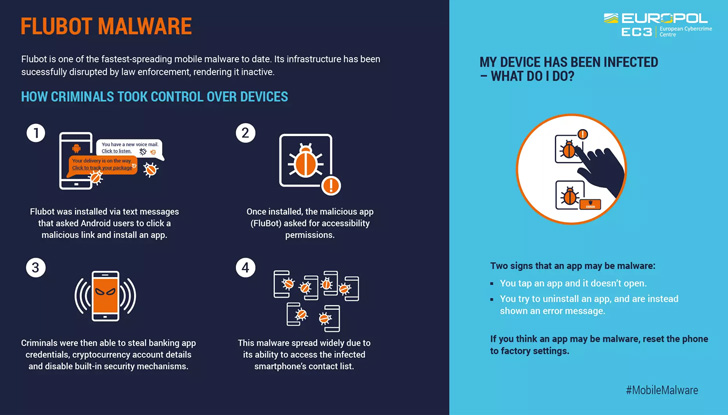
The moment introduced, the app would carry on to request obtain to Android’s Accessibility Services to stealthily siphon financial institution account credentials and other delicate information saved in cryptocurrency applications.
To make issues even worse, the malware leveraged its obtain to contacts saved in the contaminated unit to propagate the infection even further by sending messages that contains hyperlinks to the FluBot malware.

“This FluBot infrastructure is now below the handle of legislation enforcement, putting a stop to the harmful spiral,” the agency noted, adding that the Dutch Law enforcement orchestrated the seizure final thirty day period.
In accordance to ThreatFabric’s cell danger landscape report for H1 2022, FluBot was the second most active banking trojan driving Hydra, accounting for 20.9% of the samples observed involving January and May well.
Uncovered this post interesting? Abide by THN on Fb, Twitter and LinkedIn to read through more distinctive content we put up.
Some parts of this write-up are sourced from:
thehackernews.com


 YODA Tool Found ~47,000 Malicious WordPress Plugins Installed in Over 24,000 Sites
YODA Tool Found ~47,000 Malicious WordPress Plugins Installed in Over 24,000 Sites