Buyers of Zoho ManageEngine are getting urged to patch their occasions versus a critical security vulnerability forward of the release of a proof-of-concept (PoC) exploit code.
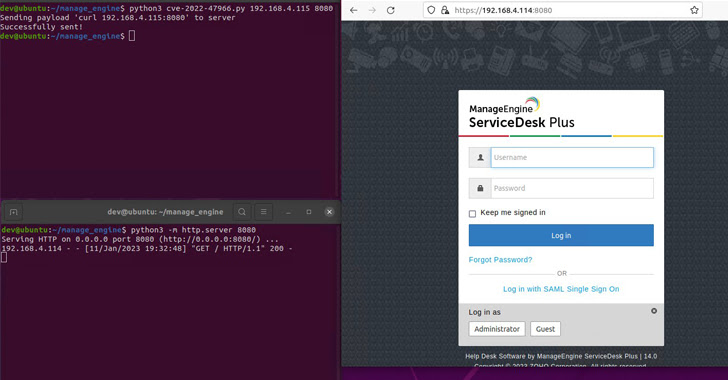
The issue in problem is CVE-2022-47966, an unauthenticated distant code execution vulnerability influencing quite a few goods due to the use of an outdated third-party dependency, Apache Santuario.
“This vulnerability makes it possible for an unauthenticated adversary to execute arbitrary code,” Zoho warned in an advisory issued late previous 12 months, noting that it impacts all ManageEngine setups that have the SAML single signal-on (SSO) element enabled, or had it enabled in the past.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Horizon3.ai has now produced Indicators of Compromise (IOCs) affiliated with the flaw, noting that it was equipped to correctly reproduce the exploit against ManageEngine ServiceDesk Furthermore and ManageEngine Endpoint Central products and solutions.
“The vulnerability is quick to exploit and a excellent applicant for attackers to ‘spray and pray’ across the internet,” researcher James Horseman explained. “This vulnerability enables for remote code execution as NT AUTHORITYSYSTEM, basically offering an attacker complete command in excess of the program.”
An attacker in possession of these elevated privileges could weaponize it to steal credentials with the purpose of conducting lateral movement, the San Francisco-headquartered business said, including the risk actor will have to have to send a specially crafted SAML request to trigger the exploit.
Horizon3.ai more termed consideration to the actuality that there are much more than 1,000 situations of ManageEngine items uncovered to the internet with SAML at the moment enabled, possibly turning them into valuable targets.
It really is not unheard of for hackers to exploit awareness of a main vulnerability for malicious strategies. It really is for that reason critical that the fixes are set up as shortly as feasible irrespective of the SAML configuration.
Observed this write-up appealing? Adhere to us on Twitter and LinkedIn to go through additional exceptional information we submit.
Some elements of this posting are sourced from:
thehackernews.com

 Russia’s Ukraine War Drives 62% Slump in Stolen Cards
Russia’s Ukraine War Drives 62% Slump in Stolen Cards