It truly is no solution that the occupation of SOC groups proceeds to grow to be increasingly tough. Improved quantity and sophistication of attacks are plaguing under-resourced teams with untrue positives and analyst burnout.
Nonetheless, like many other industries, cybersecurity is now commencing to lean on and gain from enhancements in automation to not only keep the position quo, but to achieve better security results.
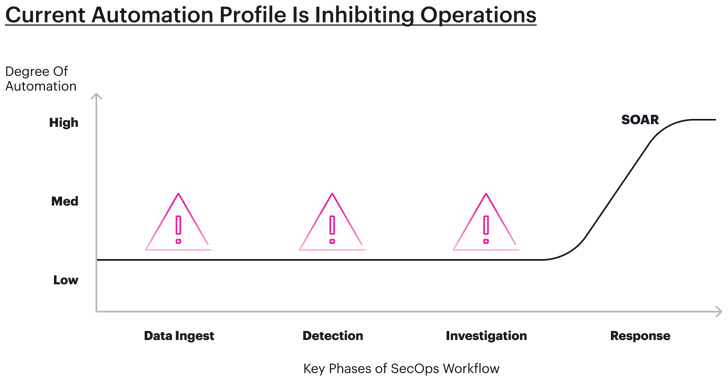
Automation across many phases of the SOC workflow
The have to have for automation is obvious, and it is obvious that it is getting table stakes for the field. Of all cyber resilient organizations, IBM estimates that 62% have deployed automation, AI and machine finding out applications and procedures.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Up until now, considerably of these developments in automation have been targeted on reaction, with SOAR and incident reaction instruments actively playing an instrumental role in tackling the most urgent stage of the SOC workflow.
Centering the concentrate only on response, however, suggests we are treating the indicators as an alternative of the root lead to of the condition. By breaking down the SOC workflow into phases, it is quick to see extra cases the place automation can boost the pace and efficacy of security teams.
The 4 phases where by it is achievable to develop protection of automation incorporate:
- Facts ingestion and normalization: Automating facts ingestion and normalization can empower groups to cope with large amounts of facts from numerous sources, laying the basis for extra automated processes
- Detection: Offloading the generation of a major proportion of the detection regulations can free of charge up time for security analysts to target on the threats that are special to their organization or marketplace phase
- Investigation: Offloading manual and tiresome perform to shorten investigation and triage procedures
- Reaction: Quickly responding to known and learned threats for fast and correct mitigation
Info: Laying the foundation for automation
Ingesting massive quantities of info might sound overwhelming to many security groups. Traditionally, groups have experienced a hard time connecting data sources or have simply had to dismiss the knowledge volumes that they couldn’t tackle because of to charge-prohibitive types of legacy instruments that cost for the amount of money of data that they keep.
With the environment continuously migrating to the cloud, it is vital that security teams do not shy away from huge info. As an alternative, they want to enact alternatives that assist them handle it and in turn, attain better security results by getting improved visibility on the whole attack surface area.
Security facts lakes have introduced with them a paradigm shift in security functions. They assist the ingestion of massive volumes and range of info, at the pace of cloud, and permit security platforms to operate analytics on prime of them with diminished complexity and at a predictable price tag.
Detection: Automating the 80%
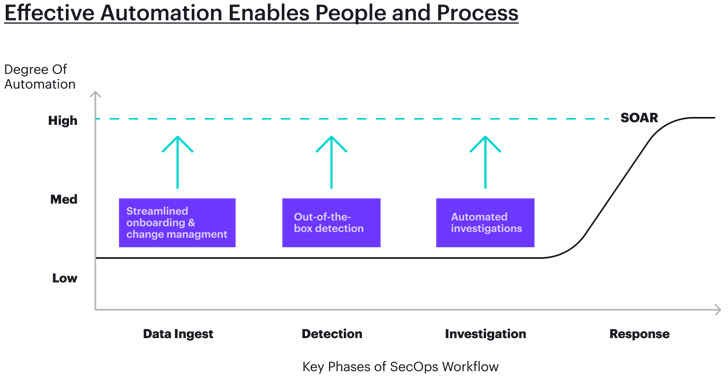
As far more info is ingested, there will inherently be extra alerts found out. All over again, this may well sound scary to overworked security groups, but automated processes, such as out-of-the-box detection policies across attack vectors, is a further excellent illustration in which automation can direct to an enhancement in coverage.
Typically talking, there are numerous similarities in the way networks are attacked, with around 80% of risk indicators becoming prevalent throughout most organizations.
A present day SOC platform gives out-of-the-box detection policies that go over this 80% by plugging into risk intelligence feeds, open up-source expertise bases, social media, or dark web discussion boards, to produce logic protecting versus the most frequent threats. Combining those people with supplemental rules penned by in-house security teams, platforms are capable to preserve up-to-date with risk techniques and use automatic detection all over them.
Investigation: Individual the signal from the sound
The investigation section of the SOC workflow is a person that is not often involved with automation. It is usually bogged down by several resources and handbook investigations limiting the efficiency and precision of security teams.
The procedures that can be bolstered with automation inside the investigation period consist of:
- Threat-centric clustering of alerts: Security resources will give you countless numbers of alerts, but in fact these boil down to only a couple of threats. At scale, this results in being an great source drain. If the alerts are mechanically grouped based mostly on their danger context, then security analysts can extra effortlessly understand and react to solitary incidents as opposed to chasing hundreds of alerts and phony-positives.
- Enrichment: By routinely enriching the entities linked with each signal or warn with added info from several unique info sources, groups get all the obtainable context to recognize the risk of the warn.
- Correlation: Instantly correlating activities prospects to superior visibility into the route of attackers inside the organization’s network.
- Visualization: At the time correlated, attack “tales” can be mapped and visualized in an easy-to-browse timeline earning it simpler for analysts and other stakeholders to obtain distinct insights.
Alongside one another, these automated responsibilities provide analysts quickly indications of which incidents are the greatest precedence and will need additional investigation. This is a drastic improvement compared to legacy units exactly where analysts are continually checking and rechecking incidents, investigating redundancies and manually piecing collectively situations.
Automated investigation, when in conjunction with handbook lookup procedures, can lead to additional serious incidents investigated, triaged and comprehended with more accuracy.
Reaction: Act immediately and confidently
At the time a risk is discovered, the apparent future move would be to reply to it. As mentioned before, SOARs do a superior job with automating the response period with acknowledged threats.
The effectiveness of this automation, on the other hand, depends seriously on info that is offered by other sources, i.e. when previously phases of the SOC workflow can produce usable and reliable outputs that can be sent to a reaction software.
Integrating additional accurate info that has been normalized and investigated by expertly engineered automation would make response instruments much extra reliable and effective.
Naturally, not all responses can be automatic as attackers keep on to evolve their strategies. In lots of scenarios, it can be essential for analysts to investigate incidents extensively and enact responses manually. But like the other phases of the workflow, the extra that these jobs can be automatic, the a lot more security groups will be freed up to handle far more intricate attacks.
So, why aren’t more organizations using automation?
Several groups know that automation will enhance their efficiency, but modifying processes and computer software is usually tough for a number of motives:
- Changing legacy computer software is time consuming, highly-priced and possibly dangerous
- Acquiring stakeholder acceptance for significant implementations is demanding and slow
- Educating analysts on working with new program normally takes time and resources
- At any time-evolving attack procedures retain security teams occupied with the “in this article and now”
These blockers piled on major of excessive staff shortages can make the undertaking seem daunting.
But, as automation continues to get center stage, the business will proceed to see significant reductions in complete value of possession (TCO), mean time to detection/reaction (MTTD/MTTR), analyst burnout and CISO annoyance.
SOC Platforms to the rescue
When numerous parts of the SOC workflow are combined and automatic, the weight and pressure of the typical workload commence to dissolve. Analysts will get started to be able to wave goodbye to spending prolonged several hours bouncing from instrument to instrument, chasing fake positives or simply retaining classic SIEM answers.
The new generation of SOC platforms have a large amount to give, at each phase of the SOC workflow. Obtaining been born in the cloud, SOC platforms are equipped to employ present day knowledge architectures to more very easily develop further attributes and enhancements. This, alongside with the advantage of getting in a position to ingest all security data at a fraction of the price tag of legacy instruments, has resulted in a craze towards greater automation embedded in them.
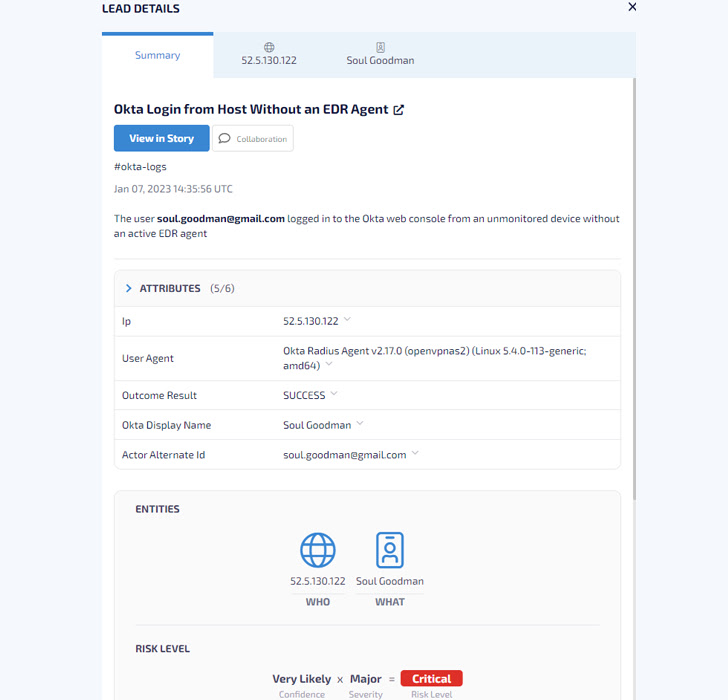 A sample Vehicle-Investigation summary on the Hunters SOC Platform demonstrating the essential entities of an notify generated just after a consumer logged in to the Okta web console from an unmonitored system without the need of an energetic EDR agent, as effectively as the Risk Score connected with it
A sample Vehicle-Investigation summary on the Hunters SOC Platform demonstrating the essential entities of an notify generated just after a consumer logged in to the Okta web console from an unmonitored system without the need of an energetic EDR agent, as effectively as the Risk Score connected with it
An instance of that can be the investigation of threats: this is regarded by most analysts to be a monotonous, handbook task, involving sorting by limitless false positives. But modern SOC platforms have launched automation, drastically improving upon the investigation procedure. Enhancements like automated cross-supply correlation, ML versions, and designed-in info interrogation queries have emerged to help analysts by the repetitive and most laborious danger investigation jobs.
Now is the time to commence leveraging automation as it proceeds to modify the sector. Groups not actively adopting these improvements will obtain by themselves behind the curve, possibly leaving their companies vulnerable and their personnel confused.
Discover more about how Hunters SOC Platform can aid your SOC: www.hunters.ai
Uncovered this posting fascinating? Abide by us on Twitter and LinkedIn to browse extra unique content material we article.
Some elements of this posting are sourced from:
thehackernews.com

 Zoho ManageEngine PoC Exploit to be Released Soon – Patch Before It’s Too Late!
Zoho ManageEngine PoC Exploit to be Released Soon – Patch Before It’s Too Late!