The high-severity RCE flaw is in the KCodes NetUSB kernel module observed in well-liked close-user routers from Netgear, TP-Connection, DLink, and Western Electronic, et al.
Hundreds of thousands of well known conclusion-consumer routers are at risk of distant code execution (RCE) owing to a high-severity flaw in the KCodes NetUSB kernel module.
The module allows link to USB products in excess of IP (NetUSB), enabling distant devices to interact with USB products related to a router as if they had been directly plugged into your pc through USB. For illustration, the module allows end users to accessibility printers, speakers or webcams as nevertheless they were being plugged directly into a laptop by means of USB: accessibility that is enabled by a computer system driver that communicates with the router by way of the kernel module.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In accordance to a Tuesday writeup from SentinelOne vulnerability researcher Max Van Amerongen, attackers could remotely exploit the vulnerability to execute code in the kernel.
NetUSB is accredited to a slew of well-liked router vendors, which includes:
- Netgear
- TP-Link
- Tenda
- EDiMAX
- DLink
- Western Electronic
Thankfully, SentinelOne hasn’t noticed evidence of the flaw possessing been exploited in the wild.
SentinelLabs started the disclosure system on Sept. 9, and the patch was sent to all distributors on Oct. 4. As of Dec. 14, Netgear experienced introduced fastened firmware for its R6700v3 product: the design that was named as a Pwn2Personal goal for Pwn2Very own Austin 2021.
On Dec. 20, Netgear introduced an advisory about the flaw, which it described as a pre-authentication buffer overflow security vulnerability that it set in its DSL Modem Routers
D7800 with firmware variation 1..1.68, as properly as in its R6400v2 routers (fastened in firmware edition 1..4.122) and R6700v3 routers (set in firmware version 1..4.122).
All of the other suppliers influenced by the NetUSB bug are aware of the vulnerability and have both fastened it or in the course of action of repairing it.
Who Does not Appreciate a Distant Kernel Bug?
As is his wont, Van Amerongen located the bug although poking all around at a concentrate on of the Pwn2Have hacking contests: namely, a Netgear router, R6700v3, that appeared in the 2019 Pwn2Have meeting as nicely as being named as a focus on in Pwn2Own Austin 2021.
He came across the NetUSB kernel module when sifting through several paths via many binaries, where he saw a little something fishy: “As it turned out, this module was listening on TCP port 20005 on the IP …,” Van Amerongen explained. “Provided there had been no firewall policies in put to block it, that would signify it was listening on the WAN as well as the LAN. Who would not like a remote kernel bug?”
He does love to pop kernels: In November, Van Amerongen wrote up a bug (CVE-2021-43267) that he found in a TIPC concept variety that permits Linux nodes to ship cryptographic keys to every single other. The critical heap-overflow security vulnerability in the Clear Inter Approach Communication (TIPC) module of the Linux kernel could have authorized nearby exploitation and RCE, main to complete system compromise.
This is not the first time for a critical NetUSB vulnerability to have been found out. In 2015, there was another kernel stack buffer overflow in KCodes NetUSB. That discovery led to a “very useful exploit” that served to immediately verify the extra recent vulnerability, Van Amerongen recounted.
The Interaction Handshake
It begins with a handshake in between the Personal computer and router that initializes interaction: a handshake that SentinelOne depicted in the graphic under.

The handshake that initializes communication. Source: SentinelOne.
What will come upcoming after the handshake is a command-parsing when-loop which is executed and which contains the next code:
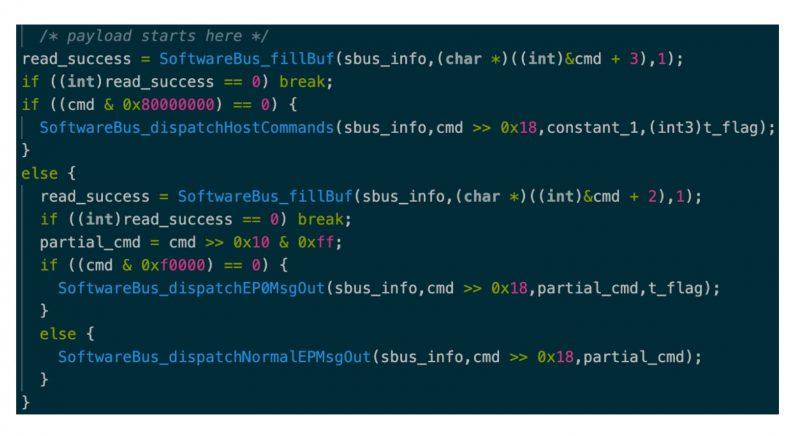
The code that can take a command range and routes the information to the appropriate SoftwareBus purpose. Resource: SentinelOne.
“SoftwareBus_fillBuf functions in a very similar way to recv by getting both a buffer and its size, filling the buffer with knowledge go through from the socket,” Van Amerongen wrote.
The Bug
The susceptible chunk of code in the kernel module is brought on when the command 0x805f reaches the adhering to code in the functionality SoftwareBus_dispatchNormalEPMsgOut:

The vulnerable section of code in the kernel module. Source: SentinelOne.
“4 bytes are fetched from the remote Personal computer,” the researcher ongoing. “The range 0x11 is included to it and then employed as a sizing benefit in kmalloc. Considering that this supplied sizing is not validated, the addition of the 0x11 can outcome in an integer overflow. For illustration, a measurement of 0xffffffff would outcome in 0x10 after 0x11 has been extra to it.”
This allotted location is then used and prepared to via both of those dereferencing and as a result of the SoftwareBus_fillBuf operate, he ongoing, as proven beneath.
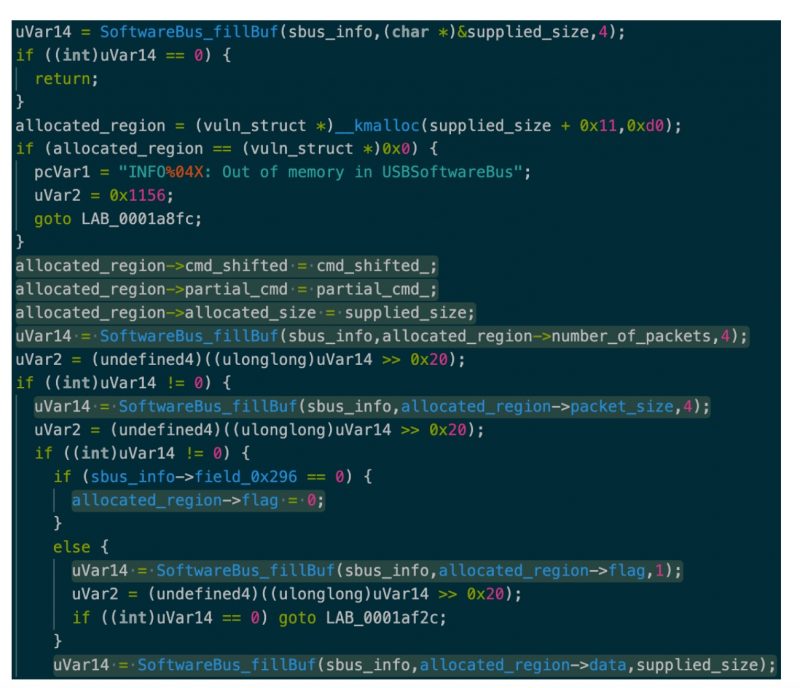
Out-of-bounds writes having location on the compact allocated region. Resource: SentinelOne.
“Looking at the ultimate phone to SoftwareBus_fillBuf, the provided size is used as a optimum price to read from the distant socket,” Van Amerongen mentioned. “From the past case in point, the sizing 0xffffffff would be utilized right here (not the overflown price) as the dimensions sent to recv.”
Alongside with its report, SentinelOne sent a suggested mitigation technique, shown under. This integer overflow verify ought to be performed in advance of allocating memory with person provided measurements:
if(user_provided_dimension + 0x11 < 0x11) return
Exploitability
There are a amount of aspects that engage in into how easy it is to exploit this bug:
Dimensions that can be allocated: The minimal sizing that can be allocated is 0x0, and the most is 0x10. “That indicates that the allotted object will generally be in the kmalloc-32 slab of the kernel heap,” Van Amerongen observed.
The amount of money of manage around the overflow by itself: The attacker controls the knowledge being acquired over the socket, but is the dimensions negotiable? “Since a dimension of 0xffffffff is not realistically exploitable on a 32-little bit program, it’s needed to get a glance at how SoftwareBus_fillBuf in fact functions,” the vulnerability researcher spelled out. “Underneath this purpose is the regular socket recv functionality. That implies that the dimension provided is only applied as a optimum receive dimension and not a rigid amount, like memcpy.”
Ease of laying out the kernel heap for the overflow: “Many exploits have to have the use of heap holes in buy to make confident that the vulnerable heap framework will be put just before the item that will be overwritten,” Van Amerongen stated. “In the scenario of this kernel module, there is a timeout of 16 seconds on the socket for obtaining data, meaning the struct can be overflown up to 16 seconds immediately after it is allocated. This eliminates the need to create a heap gap.”
Constraints with regards to which focus on buildings could be overwritten: Namely,
- The framework must be less than 32 bytes in size in order to in shape into kmalloc-32.
- The framework will have to be sprayable from a remote perspective.
- The composition ought to have some thing that can be overwritten that would make it handy
- as a focus on (e.g. a Type-Duration-Benefit structure or a pointer)
Translation: It’s challenging to write an exploit for this vulnerability, but SentinelOne doesn’t imagine it is unattainable, and it’s too critical to dismiss. “This vulnerability influences tens of millions of equipment about the entire world and in some scenarios may perhaps be fully remotely accessible,” Van Amerongen pressured.
Offered that the vulnerability is in a third-party ingredient certified to different router sellers, that implies the only correct is a firmware update – if it is even offered. If your router is end-of-daily life, that update may well never ever appear.
Prolonged story small: Router homeowners should be on the lookout for a firmware update, Van Amerongen concluded. If none’s forthcoming, the mitigation detailed over is the way to go.
“While we are not likely to release any exploits for it, there is a opportunity that one may perhaps become community in the foreseeable future regardless of the instead considerable complexity involved in developing 1,” he explained. “We endorse that all end users comply with the remediation info above in order to lessen any likely risk.”
Password Reset: On-Desire Function: Fortify 2022 with a password security tactic created for today’s threats. This Threatpost Security Roundtable, created for infosec experts, centers on enterprise credential administration, the new password basics and mitigating article-credential breaches. Sign up for Darren James, with Specops Computer software and Roger Grimes, protection evangelist at KnowBe4 and Threatpost host Becky Bracken. Register & Stream this No cost session now – sponsored by Specops Program.
Some elements of this post are sourced from:
threatpost.com


 New KCodes NetUSB Bug Affect Millions of Routers from Different Vendors
New KCodes NetUSB Bug Affect Millions of Routers from Different Vendors