Cybersecurity scientists have detailed a high severity flaw in KCodes NetUSB part that’s integrated into thousands and thousands of close-user router products from Netgear and TP-Link, amongst many others.
KCodes NetUSB is a Linux kernel module that enables gadgets on a area network to offer USB-dependent products and services above IP. Printers, external really hard drives, and flash drives plugged into a Linux-primarily based embedded procedure (e.g., a router) are built offered by means of the network making use of the driver.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
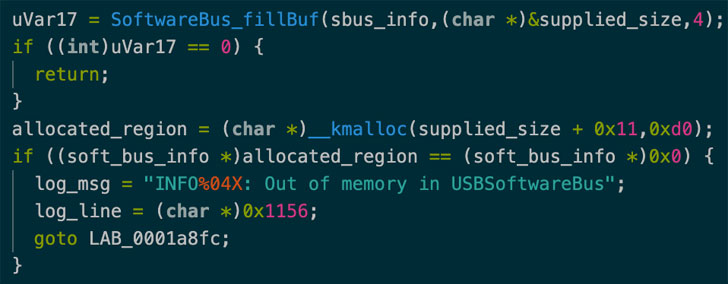
CVE-2021-45608 (CVSS rating: 9.8), as the security flaw is tracked as, relates to a buffer overflow vulnerability that, if properly exploited, can permit attackers to execute code remotely in the kernel and perform destructive things to do of their selection, in accordance to a report shared by SentinelOne with The Hacker Information.
This is the most recent in a string of NetUSB vulnerabilities that has been patched in current yrs. In Might 2015, researchers from SEC Consult disclosed one more buffer overflow flaw (CVE-2015-3036) that could consequence in a denial-of-assistance (DoS) or code execution.
Then in June 2019, Cisco Talos divulged information of two weaknesses in NetUSB (CVE-2019-5016 and CVE-2019-5017) that could enable an attacker to inappropriately drive pick out Netgear wi-fi routers into disclosing delicate information and even offering the attacker the skill to remotely execute code.
Following liable disclosure to KCodes on September 20, 2021, the Taiwanese business issued a patch to all sellers on November 19, right after which Netgear launched firmware updates containing fixes for the vulnerability.
SentinelOne has refrained from releasing a proof-of-thought (PoC) code in gentle of the simple fact that other vendors are continue to in the procedure of transport updates. But the cybersecurity firm cautioned the risk of an exploit rising in the wild despite the specialized complexity concerned, creating it essential that consumers implement the fixes to mitigate any likely risk.
“Because this vulnerability is in a third-party element licensed to many router suppliers, the only way to deal with this is to update the firmware of your router, if an update is available,” researcher Max Van Amerongen mentioned. “It is significant to verify that your router is not an close-of-lifetime model as it is unlikely to get an update for this vulnerability.”
Identified this article intriguing? Stick to THN on Fb, Twitter and LinkedIn to read through extra unique written content we write-up.
Some pieces of this posting are sourced from:
thehackernews.com



 Cyber-Thieves Raid Grass Valley
Cyber-Thieves Raid Grass Valley