Organization communications software package maker 3CX on Thursday verified that many versions of its desktop application for Windows and macOS are afflicted by a supply chain attack.
The version figures incorporate 18.12.407 and 18.12.416 for Windows and 18.11.1213, 18.12.402, 18.12.407, and 18.12.416 for macOS.
The firm mentioned it is engaging the products and services of Google-owned Mandiant to overview the incident. In the interim, it can be urging its shoppers of self-hosted and on-premise versions of the software program to update to model 18.12.422.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“3CX Hosted and StartUP customers do not need to have to update their servers as we will be updating them in excess of the night time automatically,” 3CX CEO Nick Galea stated in a put up on Thursday. “Servers will be restarted and the new Electron App MSI/DMG will be set up on the server.”
Proof out there so far details to either a compromise of 3CX’s program construct pipeline to distribute Windows and macOS variations of the app package, or alternatively, the poisoning of an upstream dependency. The scale of the attack is at the moment mysterious.
The earliest time period of most likely destructive exercise is explained to have been detected on or all over March 22, 2023, according to a write-up on the 3CX forum, despite the fact that preparations for the campaign are explained to have commenced no later than February 2022.
3CX mentioned the original warn flagging a probable security trouble in its app past 7 days was handled as a “false beneficial” owing to the actuality that none of the antivirus engines on VirusTotal labeled it as suspicious or malware.
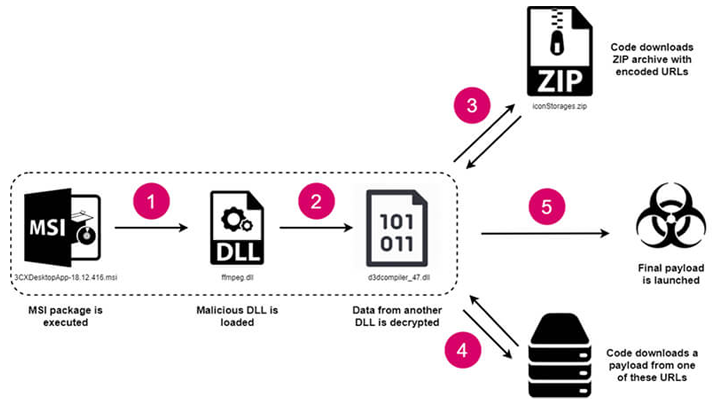
The Windows edition of the attack leveraged a technique termed DLL facet-loading to load a rogue library referred to as “ffmpeg.dll” that is made to examine encrypted shellcode from one more DLL referred to as “d3dcompiler_47.dll.”
This involved accessing a GitHub repository to retrieve an ICO file that contains URLs hosting the last-stage payload, an information and facts stealer (dubbed Legendary Stealer or SUDDENICON) able of harvesting procedure info and sensitive information stored in web browsers.
“The selection of these two DLLs – ffmpeg and d3dcompiler_47 – by the danger actors powering this attack was no accident,” ReversingLabs security researcher Karlo Zanki reported.
“The goal in issue, 3CXDesktopApp, is created on the Electron open up resource framework. Each of the libraries in concern commonly ship with the Electron runtime and, therefore, are not likely to increase suspicion in just buyer environments.”
 SUDDENICON downloading a new executable
SUDDENICON downloading a new executable
The macOS attack chain, in the identical vein, bypassed Apple’s notarization checks to obtain an unknown payload from a command-and-command (C2) server which is at present unresponsive.
“The macOS variation does not use GitHub to retrieve its C2 server,” Volexity said, which is monitoring the activity less than the cluster UTA0040. “As a substitute, a checklist of C2 servers is stored in the file encoded with a single byte XOR important, 0x7A.”
THN WEBINARBecome an Incident Response Pro!
Unlock the techniques to bulletproof incident response – Learn the 6-Stage system with Asaf Perlman, Cynet’s IR Chief!
Don’t Miss out on Out – Preserve Your Seat!
Cybersecurity company CrowdStrike, in an advisory of its personal, has attributed the attack with substantial self-confidence to Labyrinth Chollima (aka Nickel Academy), a North Korea-aligned condition-sponsored actor.
“The activity, which targets several companies throughout a wide vary of verticals with out any clear styles, has been attributed to Labyrinth Chollima based mostly on observed network infrastructure uniquely affiliated with that adversary, comparable installation tactics, and a reused RC4 crucial,” Adam Meyers, senior vice president of intelligence at CrowdStrike, advised The Hacker News.
“The trojanized 3CX applications invoke a variant of ArcfeedLoader, malware uniquely attributed to Labyrinth Chollima.”
Labyrinth Chollima, for every the Texas-based mostly company, is a subset of the Lazarus Group, which also constitutes Silent Chollima (aka Andariel or Nickel Hyatt) and Stardust Chollima (aka BlueNoroff or Nickel Gladstone).
The team “has been active at least considering the fact that 2009 and normally tries to deliver profits by focusing on crypto and fiscal corporations,” Meyers said, introducing it can be “probably affiliated with Bureau 121 of the DPRK’s Reconnaissance Normal Bureau (RGB) and generally conducts espionage functions and income era techniques.”
Uncovered this article exciting? Follow us on Twitter and LinkedIn to read additional unique written content we publish.
Some sections of this write-up are sourced from:
thehackernews.com


 UK Regulator: HIV Data Protection Must Improve
UK Regulator: HIV Data Protection Must Improve