Long gone are the days when ransomware operators ended up content with encrypting documents on-internet site and far more or considerably less discretely charged their victims cash for a decryption important. What we normally find now is encryption with the additional danger of leaking stolen knowledge, typically referred to as Double-Extortion (or, as we like to get in touch with it: Cyber Extortion or Cy-X). This is a distinctive variety of cybercrime in that we can notice and assess some of the criminal action by means of ‘victim shaming’ leak sites.
Since January 2020, we have applied ourselves to figuring out as lots of of these web sites as attainable to history and doc the victims who function on them. Including our own investigate, analyzing, and enriching information scraped from the a variety of Cy-X operators and industry web-sites, we can supply direct insights into the victimology from this specific perspective.
We will have to be obvious that what we are analyzing is a restricted point of view on the crime. Yet, the data gleaned from an investigation of the leak-threats proves to be really instructive.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
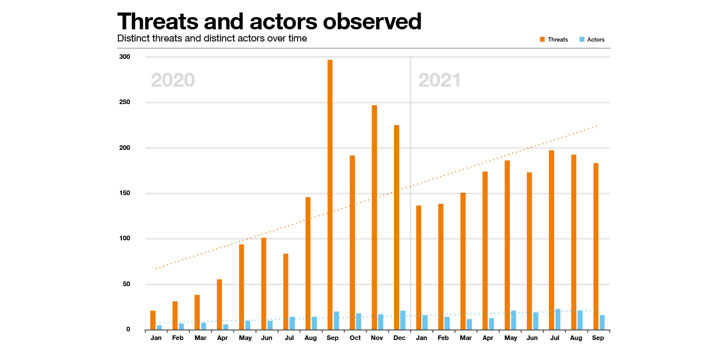
We will refer to the listing of a compromised firm on a Cy-X leak web page as a ‘leak threat’. The numbers you can see in most of the charts beneath refer to counts of this kind of unique threats on the onion web-sites of the Cy-X groups we’ve been equipped to identify and monitor more than the last two several years.
A growth in leak threats
Inspite of the vagaries of the environment we’re observing, the selection of distinctive leaks serves as trustworthy proxy for the scale of this crime, and its typical traits over time. We noticed an just about 6-fold enhance in leak-threats from the initial quarter of 2020 to the 3rd quarter of 2021.
Striking where the funds is: Leak threats by region
Let’s acquire a seem at the international locations the victims run in.
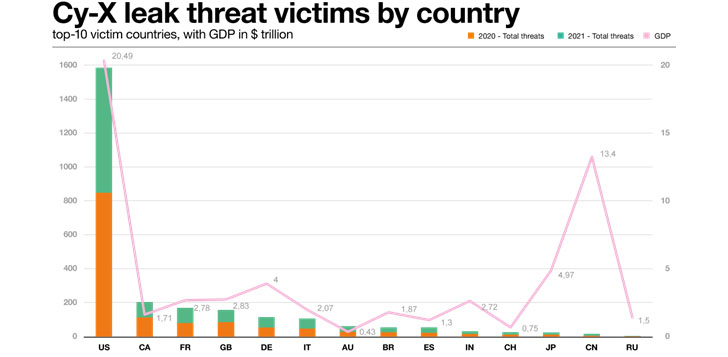
In the chart over we show the 2020 and 2021 leak danger counts per country, for the major 10 international locations featured in our information established. We also demonstrate the believed Gross Domestic Products (GDP) for the 12 wealthiest countries[1].
The prime victim nations have remained somewhat continuous across our details set. As a basic rule of thumb, the ranking of a region in our info established tracks the relative GDP of that state. The even bigger the economy of a region, the much more victims it is probable to have. In fact, eight of the leading 10 Cy-X victim nations around the world are between the prime 10 economies in the entire world.
The conclusion we attract from this, is that the relative quantity of victims in a region is merely a function of the amount of on the internet corporations in that place. This does not demonstrate definitively that Cy-X actors do not intentionally attack targets in precise international locations or regions from time to time. It can be also not to say that a organization in a large-GDP place is extra very likely to be attacked than a sufferer in a reduced-GDP state (since, with far more companies uncovered in just that state, the chances even out).
In our check out, the just take-absent from this details is just that organizations in virtually each and every nation are becoming compromised and extorted. Logically, the additional businesses a nation has, the additional victims we will see.
Exceptions to the rule
Acquiring mentioned that, we have taken the liberty of which include India, Japan, China and Russia in the chart previously mentioned, as counterexamples of substantial-GDP international locations that rank reduced on our Cy-X victims record.
India, with a projected 2021 GDP of $ 2.72 trillion, and China with $ 13.4 trillion, look underrepresented, which could be due to numerous motives. India, for instance, has a enormous inhabitants and correspondingly substantial GDP, but the GDP per capita is lower, and the financial state normally appears significantly less modernized and digital, which means less online enterprises to concentrate on. It could be that criminals question that Indian enterprises could or would shell out their greenback-dependent ransoms. The language may possibly also engage in a purpose – organizations that don’t talk in English are a lot more tough to identify, recognize, navigate, and negotiate with, and their users are tougher to exploit employing commoditized social engineering tools.
Japan, as an additional apparent exception to our rule, has a really modernized economy, but will present criminals with the exact language and lifestyle boundaries as China and India, therefore probably accounting for the reduced prevalence in our sufferer data.
The conclusion here is that Cy-X is shifting from English to non-English economies, but gradually for the time getting. This is almost certainly the logical outcome of the expanding demand from customers for victims fueled by new actors, but it may also be the consequence of improved political signaling from the Usa, which may well be creating actors a lot more careful about who they and their affiliates exploit.
Regardless of the causes, the summary here after once again wants to be that victims are discovered in almost every single country, and countries who have hitherto appeared comparatively unaffected are not able to hope that this will keep on being the case.
A single dimension fits all: No proof of ‘big game hunting’
In the chart beneath we demonstrate the amount of victims by organization size in our facts set mapped to the major 5 actors. We outline organization dimensions as smaller (1000 or a lot less staff), medium (1000-10,000) and significant (10,000+).
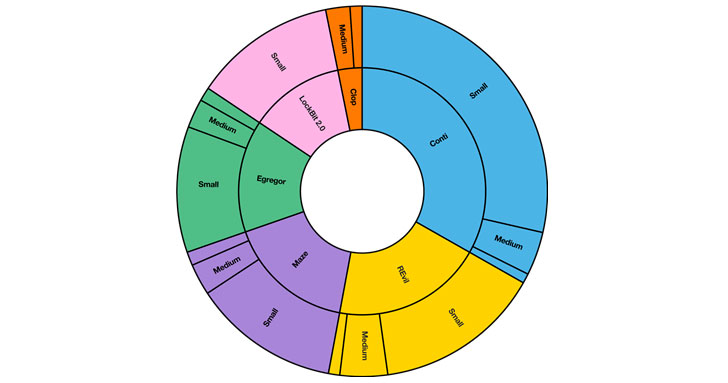
As demonstrated, organizations with considerably less than 1,000 employees are compromised and threatened most normally, with practically 75% of all leaks originating from them. We have viewed this sample constantly in our leak-threats knowledge over the past two decades, by marketplace, state, and actor.
The most obvious clarification for this sample is all over again that criminals are attacking indiscriminately, but that there are more smaller organizations in the world. Modest companies are also most likely to have fewer competencies and technical assets with which to protect themselves or recover from attacks.
This indicates once more that any and every single business enterprise can expect to be targeted, and that the primary deciding factor of starting to be a leak site target is the capacity of the organization to withstand attack and recover from compromise.
It is really worthy of also noting that, considering that the criminal offense we are investigating right here is extortion, and not theft, it is the benefit of the impacted digital asset to the sufferer that problems us, not the value of the knowledge to the prison.
Any organization that has electronic belongings of worth can hence be a target. Neither little dimension nor the perceived ‘irrelevance’ of data will provide significant security or ‘fly beneath the radar’.
This is just an excerpt of the analysis. Extra aspects like the menace actors determined or the industries specific most (as effectively as a ton of other intriguing exploration topics) can be found in the Security Navigator. It’s available for download on the Orange Cyberdefense web-site, so have a glance. It truly is value it!
Notice — This write-up was created and contributed by Carl Morris, guide security researcher, and Charl van der Walt, head of security exploration, of Orange Cyberdefense.
Identified this article exciting? Observe THN on Facebook, Twitter and LinkedIn to study far more exceptional content we publish.
Some parts of this short article are sourced from:
thehackernews.com


 New BHUNT Password Stealer Malware Targeting Cryptocurrency Wallets
New BHUNT Password Stealer Malware Targeting Cryptocurrency Wallets