A new evasive crypto wallet stealer named BHUNT has been noticed in the wild with the objective of monetary obtain, introducing to a checklist of electronic forex thieving malware these types of as CryptBot, Redline Stealer, and WeSteal.
“BHUNT is a modular stealer composed in .NET, capable of exfiltrating wallet (Exodus, Electrum, Atomic, Jaxx, Ethereum, Bitcoin, Litecoin wallets) contents, passwords saved in the browser, and passphrases captured from the clipboard,” Bitdefender researcher stated in a specialized report on Wednesday.
The campaign, dispersed globally throughout Australia, Egypt, Germany, India, Indonesia, Japan, Malaysia, Norway, Singapore, South Africa, Spain, and the U.S., is suspected to be delivered to compromised systems by using cracked software program installers.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The modus operandi of working with cracks as an an infection source for preliminary obtain mirrors identical cybercrime campaigns that have leveraged applications these as KMSPico as a conduit for deploying malware. “Most infected people also experienced some form of crack for Windows (KMS) on their units,” the scientists mentioned.
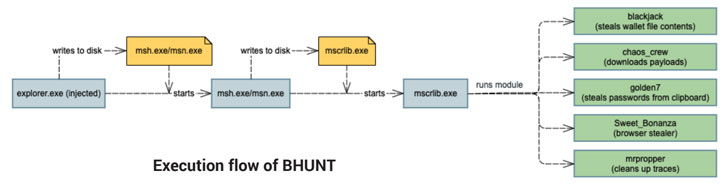
The attack sequence starts with the execution of an initial dropper, which proceeds to compose intensely-encrypted interim binaries that are then utilised to launch the major component of the stealer — a .NET malware that incorporates different modules to facilitate its malicious pursuits, the success of which are exfiltrated to a remote server —
- blackjack – steal wallet file contents
- chaos-crew – down load added payloads
- golden7 – siphon cookies from Firefox and Chrome as properly as passwords from clipboard
- Sweet_Bonanza – steal saved passwords from browsers these types of as Internet Explorer, Firefox, Chrome, Opera, and Safari, and
- mrpropper – clean up up traces
The facts theft could also have a privacy affect in that the passwords and account tokens stolen from the browser cache could be abused to commit fraud and to gain other economical advantages.
“The most effective way to protect towards this risk is to prevent setting up program from untrusted resources and to preserve security options up to date,” the scientists concluded.
Uncovered this write-up intriguing? Abide by THN on Facebook, Twitter and LinkedIn to examine a lot more exceptional content material we publish.
Some areas of this write-up are sourced from:
thehackernews.com

 Microsoft: Hackers Exploiting New SolarWinds Serv-U Bug Related to Log4j Attacks
Microsoft: Hackers Exploiting New SolarWinds Serv-U Bug Related to Log4j Attacks