Scientists have shown what they get in touch with the “lively contactless attack in opposition to capacitive touchscreens.”
GhostTouch, as it’s named, “employs electromagnetic interference (EMI) to inject faux touch factors into a touchscreen without having the need to have to bodily touch it,” a team of academics from Zhejiang College and Technical College of Darmstadt claimed in a new study paper.
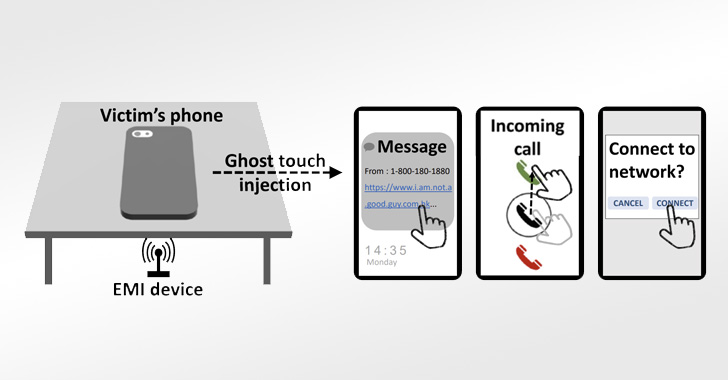
The main concept is to get gain of the electromagnetic alerts to inject bogus contact activities this kind of as faucets and swipes into qualified spots of the touchscreen with the target of getting about distant manage and manipulating the fundamental product.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The attack, which functions from a distance of up to 40mm, hinges on the reality that capacitive touchscreens are sensitive to EMI, leveraging it to inject electromagnetic signals into transparent electrodes that are built into the touchscreen so as to sign-up them as contact gatherings.
The experimental set up includes an electrostatic gun to make a solid pulse signal that’s then despatched to an antenna to transmit an electromagnetic discipline to the phone’s touchscreen, therefore resulting in the electrodes — which act as antennas them selves — to decide up the EMI.
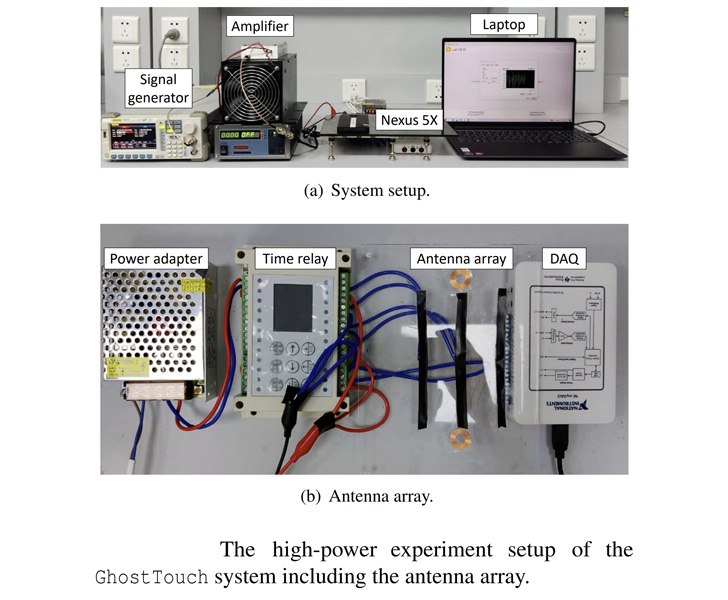
This can be even further wonderful-tuned by tweaking the sign and the antenna to induce a selection of touch behaviors, these kinds of as press and hold and swipe to decide on, relying on the device model qualified.
In a serious-environment circumstance, this could participate in out in distinctive techniques, including swiping up to unlock a phone, connecting to a rogue Wi-Fi network, stealthily clicking on a destructive connection made up of malware, and even answering a phone phone on the victim’s behalf.
“In areas like a cafe, library, conference place, or meeting lobbies, individuals may well position their smartphone encounter-down on the desk,” the scientists said. “An attacker may possibly embed the attack equipment below the table and launch attacks remotely.”

As a lot of as 9 diverse smartphone types have been identified vulnerable to GhostTouch, which includes Galaxy A10s, Huawei P30 Lite, Honor View 10, Galaxy S20 FE 5G, Nexus 5X, Redmi Note 9S, Nokia 7.2, Redmi 8, and an iPhone SE (2020), the latter of which was utilised to create a malicious Bluetooth link.
To counteract the threat, the researchers endorse including electromagnetic shielding to block EMI, strengthening the detection algorithm of the touchscreen, and prompting people to enter the phone’s PIN or verify their faces or fingerprints prior to executing substantial-risk steps.
“GhostTouch controls and designs the in the vicinity of-subject electromagnetic signal, and injects contact functions into the targeted place on the touchscreen, with out the want for bodily contact or accessibility to the victim’s device,” the researchers explained.
Located this article fascinating? Observe THN on Fb, Twitter and LinkedIn to read through more exclusive material we post.
Some pieces of this report are sourced from:
thehackernews.com

 UK Government Seeks Views to Bolster the Nation’s Data Security
UK Government Seeks Views to Bolster the Nation’s Data Security