“Shifting (security)” remaining technique in Program Advancement Everyday living Cycle (SDLC) indicates setting up security previously in the method. As organizations understood that software package by no means comes out perfectly and are riddled with a lot of exploitable holes, bugs, and company logic vulnerabilities that have to have likely again to take care of and patch, they recognized that setting up secure software program involves incorporating and consolidating a lot of sources.
This conclusion led DevOps and R&D leaders to grow to be proactive, acquiring technology to locate and shut these gaps in progress, with the purpose of lessening the value and work while strengthening the high-quality of their results.
With emerging comprehensive constant security validation technology, the shown positive aspects of ‘shifting left’ as a essential portion of SDLC can now be utilized to your cybersecurity program, with effects considerably exceeding the purely specialized facets of security posture administration.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
At the growth amount, the conceptualization of SDLC is the end result of the convergence of many traces of thought to enhance the system. From a cybersecurity perspective, the identical imagined convergence system led to the concept of rolling out a continual security assurance application by employing the fundamentals of Prolonged Security Posture Administration (XSPM) technology.
The Security Posture Management Lifecycle
Like SDLC, XSPM is born out of the have to have to consider into consideration the entire security posture management lifecycle, including validation from an offensive standpoint. Considering that the time period ‘shifting left’ was coined, a plethora of detect and reaction alternatives integrable into the CI/CD course of action has emerged. Nevertheless, even postulating a flawlessly integrated and optimized advanced detection and reaction software stack, it will even now endure from a structural flaw. Detect and reply is a reactive approach that leaves the initiative in the hands of the attacker and presupposes the capability to detect any and all attacks.
In truth, the more and more dynamic nature of the cyber-risk landscape and the uneven mother nature of cyber protection – an attacker only desires to thrive when, whilst defenders require to block each solitary attack – necessarily mean that concentrating solely on the reactive detect and response technique is akin to battling the previous war. The time has occur to switch to shifting more still left to integrating a proactive continual security validation method.
XSPM includes all the continual security validation aspects and organizes them in a security posture 4 stages lifecycle – Assess, Enhance, Rationalize, Guarantee.
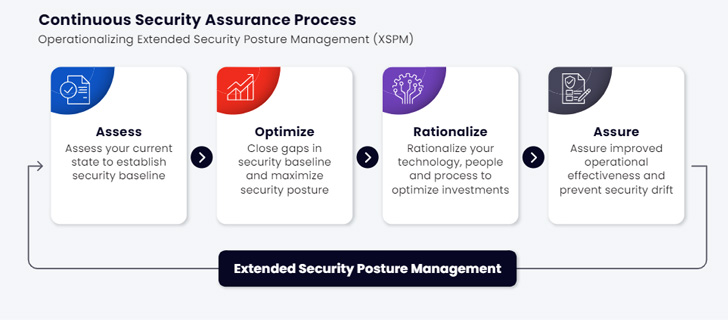
- The ‘Assessing’ step is composed of launching a detailed set of attacks masking the attack get rid of chain from commencing to conclude.
- The ‘Optimizing’ step identifies misconfigured security controls, enabling optimizing them to generally compensate for not but patched CVEs and decrease the IT group patching workload.
- The ‘Rationalizing’ action evaluates the efficacy of the detection and reaction tool stack, offers in depth info to boost their configuration and identifies overlapping applications and missing capabilities.
- The final move, ‘Assuring’, incorporates a dynamic analytic method that can be personalized as essential and made use of to visualize the security posture trends about time.
Productiveness tops security, let us make security productive
The optimization of cybersecurity packages as facilitated by XSPM’s framework and technology delivers for greater utilization of the cash and methods invested in cybersecurity. Decreasing overlap, reducing patching window, prioritizing workload, location KPIs, and other positive aspects immediately result from integrating security early on alternatively than retrospectively.
To realize this mixed optimization of resource allocation and security posture, each security and risk management leaders first will need to build a relatable, validated baseline. With information emanating completely from a detect and reaction array, the actuality is an unoptimized sequential process that pushes the proactive security validation step at the again of the queue and final results in antagonizing siloed DevOps and SOC groups. Misaligned goals concerning teams guide to a chaotic stream of contradictory details hampering the determination-building method, slowing down operations and probably top to unsecured deployment.
Combining the two for protected software program – the gains of baking XSPM in SDLC
When security testing only kicks in at the conclusion of the SDLC, the delays prompted in deployment due to uncovered critical security gaps induce rifts amongst DevOps and SOC teams. Security normally gets pushed to the back of the line, and you can find not substantially collaboration when introducing a new resource, or method, this sort of as launching occasional simulated attacks in opposition to the CI/CD pipeline.
Conversely, the moment a complete continuous security validation method is baked in the SDLC, day-to-day invoking attack methods emulations through the automation crafted-in XSPM technology identify misconfiguration early in the method, incentivizing shut collaboration among DevSecOps and DevOps. With built-in inter-team collaboration across both equally security and program development lifecycle, doing the job with quick visibility on security implications, the target alignment of both equally groups gets rid of erstwhile strife and friction born of inner politics.
Developing exponential outcomes
Shifting extreme still left with in depth constant security validation allows you to get started mapping and to understand the investments built in various detection and response technologies and applying findings to preempt attack procedures across the destroy chain and protect authentic functional specifications.
The procedure equips IT teams with all they need to have to recognize alternatives that solidify and stabilize security posture management from the quite commence, avoiding high-priced delays in deployment and reducing the risk of profitable breach makes an attempt, whilst SOC groups acquire specific facts on which to construct a threat informed strategy.
How are you likely to be proactive right now about your firm’s security posture?
Notice — This posting is penned and contributed by Ben Zilberman – Solution Marketing and advertising Director at Cymulate.
Uncovered this report intriguing? Stick to THN on Facebook, Twitter and LinkedIn to go through extra exclusive content we publish.
Some sections of this write-up are sourced from:
thehackernews.com


 CISA Warned About Critical Vulnerabilities in Illumina’s DNA Sequencing Devices
CISA Warned About Critical Vulnerabilities in Illumina’s DNA Sequencing Devices