A malicious campaign targeting the Center East is likely connected to BackdoorDiplomacy, an superior persistent menace (APT) team with ties to China.
The espionage activity, directed against a telecom business in the location, is claimed to have commenced on August 19, 2021 via the successful exploitation of ProxyShell flaws in the Microsoft Trade Server.
First compromise leveraged binaries susceptible to facet-loading methods, adopted by making use of a combine of legit and bespoke applications to conduct reconnaissance, harvest info, shift laterally across the surroundings, and evade detection.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“File attributes of the destructive resources confirmed that the initial tools deployed by the risk actors were the NPS proxy tool and IRAFAU backdoor,” Bitdefender researchers Victor Vrabie and Adrian Schipor explained in a report shared with The Hacker News.
“Beginning in February 2022, the danger actors used another instrument – [the] Quarian backdoor, alongside with a lot of other scanners and proxy/tunneling instruments.”

BackdoorDiplomacy was first documented by ESET in June 2021, with the intrusions mostly aimed at diplomatic entities and telecommunication organizations in Africa and the Middle East to deploy Quarian (aka Turian or Whitebird).
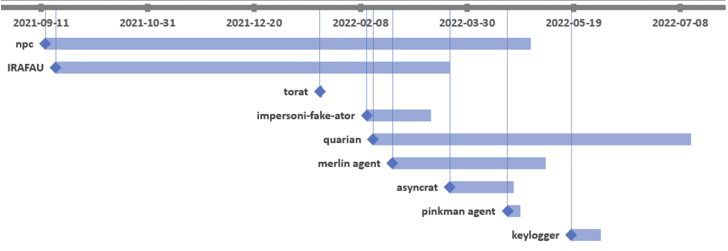
The espionage motives of the attack is evidenced by the use of keylogger and PowerShell scripts made to get email content. IRAFAU, which is the 1st malware element shipped right after obtaining a foothold, is utilized to perform facts discovery and lateral movement.
This is facilitated by downloading and uploading data files from and to a command-and-management (C2) server, launching a distant shell, and executing arbitrary information.
The 2nd backdoor utilised in the procedure is an up to date edition of Quarian, which arrives with a broader established of capabilities to command the compromised host.
Also set to use is a software dubbed Impersoni-pretend-ator that’s embedded into authentic utilities like DebugView and Putty and is engineered to seize process metadata and execute a decrypted payload been given from the C2 server.
The intrusion is more characterised by the use of open source computer software this sort of as ToRat, a Golang remote administration software, and AsyncRAT, the latter of which is very likely dropped through Quarian.
Bitdefender’s attribution of the attack to BackdoorDiplomacy arrives from overlaps in the C2 infrastructure recognized as employed by the group in prior campaigns.
Observed this article appealing? Comply with us on Twitter and LinkedIn to go through additional distinctive content we put up.
Some elements of this article are sourced from:
thehackernews.com


 Threat Actors Use Malicious File Systems to Scale Crypto-Mining Operations
Threat Actors Use Malicious File Systems to Scale Crypto-Mining Operations