Networking tools maker Cisco has launched a new variation of its Jabber video clip conferencing and messaging app for Windows that features patches for multiple vulnerabilities—which, if exploited, could permit an authenticated, distant attacker to execute arbitrary code.
The flaws, which have been uncovered by Norwegian cybersecurity agency Watchcom for the duration of a pentest, impact all now supported versions of the Jabber customer (12.1-12.9) and has because been preset by the business.
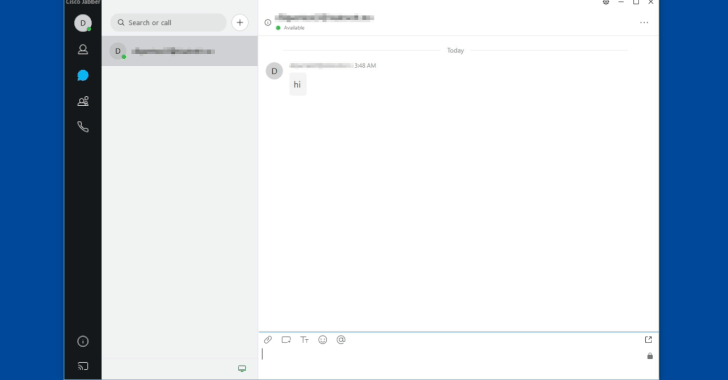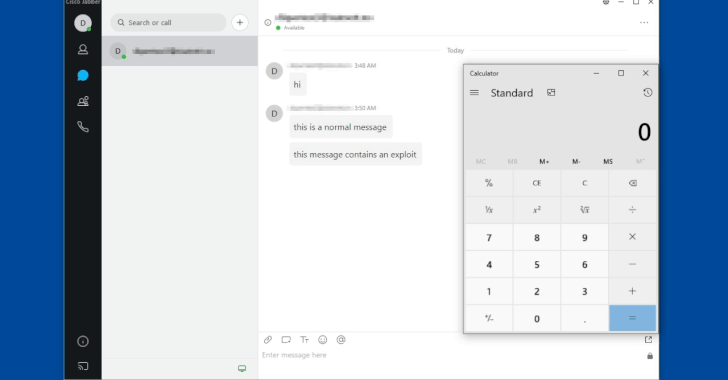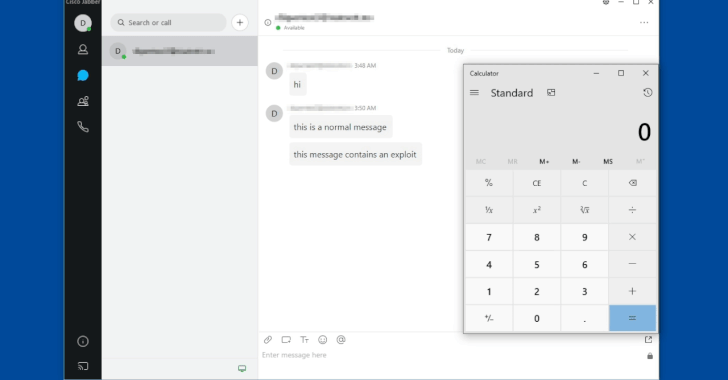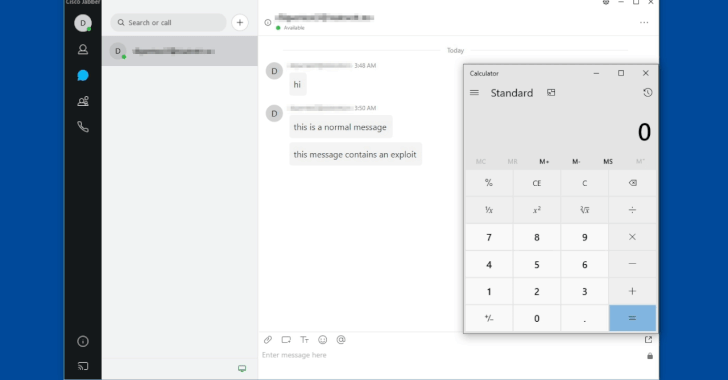
Two of the 4 flaws can be exploited to get remote code execution (RCE) on focus on techniques by sending specifically crafted chat messages in team discussions or specific folks.
The most critical of the ton is a flaw (CVE-2020-3495, CVSS rating 9.9) that is triggered by incorrect validation of message contents, which could be leveraged by an attacker by sending maliciously-crafted Extensible Messaging and Existence Protocol (XMPP) messages to the afflicted software program.
“A thriving exploit could let the attacker to lead to the application to execute arbitrary systems on the qualified program with the privileges of the person account that is running the Cisco Jabber shopper computer software, potentially resulting in arbitrary code execution,” Cisco claimed in an advisory printed yesterday.
The advancement will come times just after Cisco warned of an actively exploited zero-day flaw in its IOS XR router software.
An XSS Flaw to an RCE Flaw
XMPP (at first known as Jabber) is an XML-based communications protocol employed for facilitating prompt messaging in between any two or extra network entities.
It really is also designed to be extensible so as to accommodate further functionality, one of which is XEP-0071: XHTML-IM — a specification that lays down the rules for exchanging HTML content utilizing the XMPP protocol.
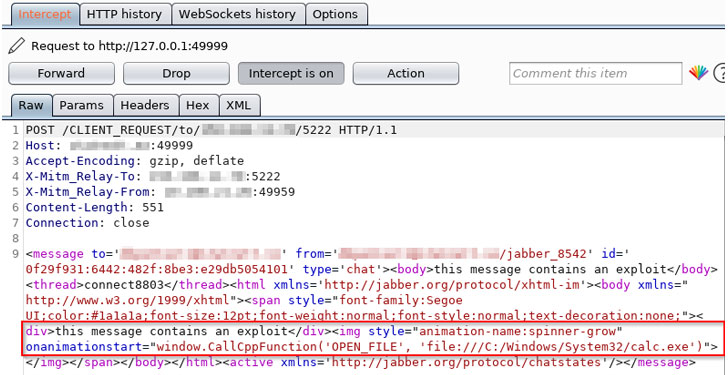
The flaw in Cisco Jabber occurs from cross-internet site scripting (XSS) vulnerability when parsing XHTML-IM messages.
“The software does not correctly sanitize incoming HTML messages and instead passes them as a result of a flawed XSS filter,” Watchcom scientists described.
As a consequence, a genuine XMPP information can be intercepted and modified, thus producing the software to run an arbitrary executable that previously exists in just the community file route of the software.
To obtain this, it usually takes edge of a different susceptible operate in Chromium Embedded Framework (CEF) — an open up-resource framework which is utilised to embed a Chromium web browser in other apps — that could be abused by a poor actor to execute rogue “.exe” files on the victim’s equipment.
Attackers, nonetheless, are needed to have access to their victims’ XMPP domains to send the destructive XMPP messages wanted to exploit the vulnerability effectively.
Additionally, three other flaws in Jabber (CVE-2020-3430, CVE-2020-3498, CVE-2020-3537) could be exploited to inject malicious instructions and cause facts disclosure, which include the probability of stealthily collecting users’ NTLM password hashes.
With movie conferencing applications turning into preferred in the wake of the pandemic, it is really vital that Jabber customers update to the newest edition of the software package to mitigate the risk.
“Specified their newfound prevalence in organizations of all dimensions, these programs are starting to be an significantly attractive focus on for attackers,” Watchcom stated. “A whole lot of delicate information and facts is shared by way of online video phone calls or immediate messages and the purposes are used by the the greater part of staff members, which includes all those with privileged obtain to other IT methods.”
“The security of these programs is hence paramount, and it is essential to make certain that each the purposes on their own, and the infrastructure they are applying, are routinely audited for security gaps.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Discovered this report appealing? Observe THN on Fb, Twitter and LinkedIn to go through far more special information we write-up.

 How to use cybersecurity to accelerate development
How to use cybersecurity to accelerate development