A security shortcoming in Microsoft Azure Energetic Directory (Advertisement) Open Authorization (OAuth) approach could have been exploited to obtain full account takeover, scientists claimed.
California-centered id and accessibility management services Descope, which found and noted the issue in April 2023, dubbed it nOAuth.
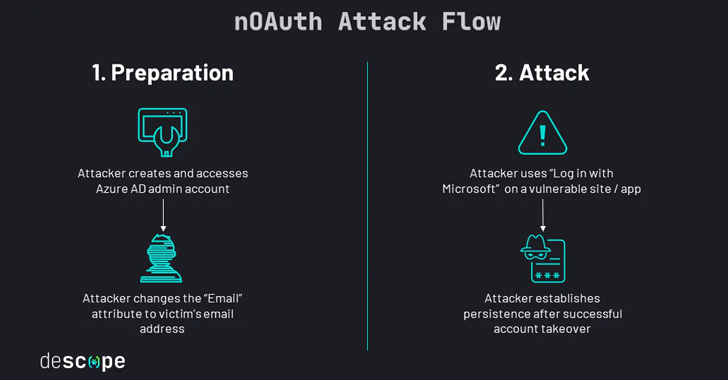
“nOAuth is an authentication implementation flaw that can have an effect on Microsoft Azure Advert multi-tenant OAuth programs,” Omer Cohen, chief security officer at Descope, reported.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The misconfiguration has to do with how a malicious actor can modify email attributes beneath “Call Facts” in the Azure Advertisement account and exploit the “Log in with Microsoft” function to hijack a victim account.

To pull off the attack, all an adversary has to do is to produce and obtain an Azure Ad admin account and modify their email deal with to that of a sufferer and consider benefit of the one sign-on scheme on a vulnerable app or site.
“If the application merges person accounts without having validation, the attacker now has full manage above the victim’s account, even if the target doesn’t have a Microsoft account,” Cohen discussed.
Productive exploitation grants the adversary an “open up subject” to established up persistence, exfiltrate facts, and have out other submit-exploitation actions dependent on the nature of the app.
This stems from the reality that an email tackle is both equally mutable and unverified in Azure Ad, prompting Microsoft to issue a warning not to use email promises for authorization needs.
Approaching WEBINAR🔐 Mastering API Security: Comprehending Your Genuine Attack Area
Learn the untapped vulnerabilities in your API ecosystem and just take proactive techniques towards ironclad security. Sign up for our insightful webinar!
Join the Session.wn-button,.wn-label,.wn-label:right afterscreen:inline-block.examine_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px strong #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-leading-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-proper-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-measurement:13pxmargin:20px 0font-excess weight:600letter-spacing:.6pxcolor:#596cec.wn-label:followingwidth:50pxheight:6pxcontent:”border-top:2px sound #d9deffmargin: 8px.wn-titlefont-dimensions:21pxpadding:10px 0font-weight:900text-align:leftline-height:33px.wn-descriptiontext-align:leftfont-dimensions:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-sizing:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-fat:500letter-spacing:.2px
The tech giant characterised the issue as an “insecure anti-sample made use of in Azure Advertisement (AAD) programs” wherever the use of the email claim from obtain tokens for authorization can lead to an escalation of privilege.
“An attacker can falsify the email claim in tokens issued to purposes,” it noted. “Moreover, the danger of details leakage exists if apps use this kind of promises for email lookup.”
It also said it identified and notified many multi-tenant applications with end users that make use of an email handle with an unverified area owner.
Observed this report appealing? Follow us on Twitter and LinkedIn to browse additional unique material we post.
Some sections of this posting are sourced from:
thehackernews.com

 Chinese Hacker Group ‘Flea’ Targets American Ministries with Graphican Backdoor
Chinese Hacker Group ‘Flea’ Targets American Ministries with Graphican Backdoor