The Black Basta ransomware-as-a-company (RaaS) syndicate has amassed nearly 50 victims in the U.S., Canada, the U.K., Australia, and New Zealand within two months of its emergence in the wild, creating it a notable danger in a shorter window.
“Black Basta has been noticed focusing on a variety of industries, which include producing, construction, transportation, telcos, prescription drugs, cosmetics, plumbing and heating, automobile dealers, undergarments companies, and additional,” Cybereason mentioned in a report.
Identical to other ransomware functions, Black Basta is regarded to utilize the tried out-and-analyzed tactic of double extortion to plunder delicate info from the targets and threaten to publish the stolen info unless of course a digital payment is made.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A new entrant in the previously crowded ransomware landscape, intrusions involving the risk have leveraged QBot (aka Qakbot) as a conduit to manage persistence on the compromised hosts and harvest qualifications, right before going laterally across the network and deploying the file-encrypting malware.
In addition, the actors driving Black Basta have formulated a Linux variant developed to strike VMware ESXi digital equipment (VMs) working on enterprise servers, placing it on par with other groups this sort of as LockBit, Hive, and Cheerscrypt.
The results appear as the cybercriminal syndicate added Elbit Techniques of The united states, a manufacturer of defense, aerospace, and security alternatives, to the list of its victims about the weekend, according to security researcher Ido Cohen.
Black Basta is stated to be comprised of users belonging to the Conti group soon after the latter shuttered its operations in response to amplified legislation enforcement scrutiny and a important leak that saw its instruments and methods entering the community area right after siding with Russia in the country’s war towards Ukraine.
“I are unable to shoot nearly anything, but I can fight with a keyboard and mouse,” the Ukrainian laptop expert behind the leak, who goes by the pseudonym Danylo and introduced the treasure trove of info as a type of digital retribution, informed CNN in March 2022.
The Conti team has because refuted that it can be associated with Black Basta. Very last week, it decommissioned the past of its remaining general public-dealing with infrastructure, including two Tor servers utilized to leak info and negotiate with victims, marking an formal conclude to the criminal enterprise.
In the interim, the team ongoing to retain the facade of an active procedure by concentrating on the Costa Rican governing administration, whilst some associates transitioned to other ransomware outfits and the brand name underwent a organizational revamp that has witnessed it devolve into smaller subgroups with distinct motivations and company products ranging from info theft to doing work as independent affiliate marketers.
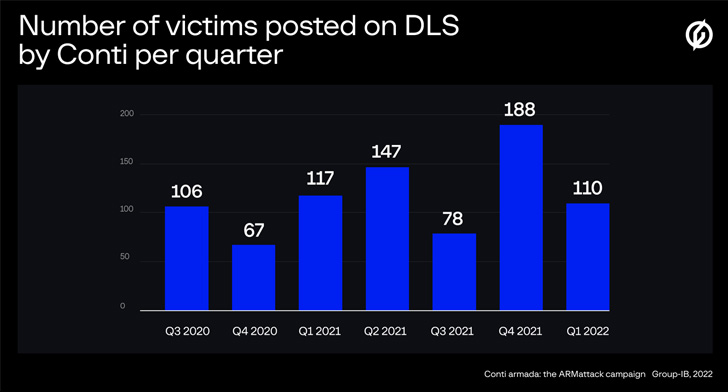
In accordance to a thorough report from Group-IB detailing its things to do, the Conti team is thought to have victimized a lot more than 850 entities considering that it was very first observed in February 2020, compromising over 40 businesses all over the world as element of a “lightning-quickly” hacking spree that lasted from November 17 to December 20, 2021.

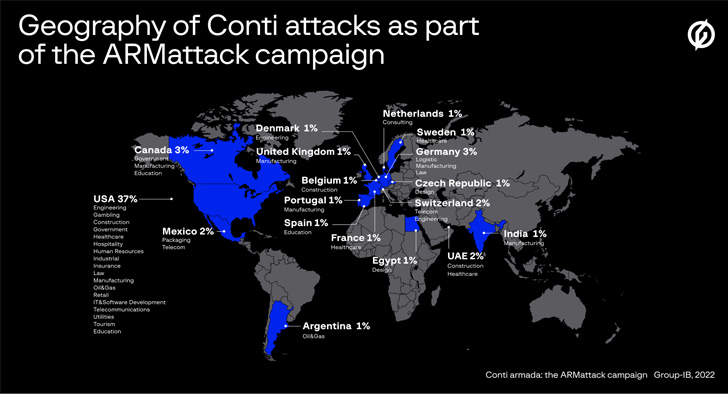
Dubbed “ARMattack” by the Singapore-headquartered enterprise, the intrusions were largely directed in opposition to U.S. organizations (37%), adopted by Germany (3%), Switzerland (2%), the U.A.E. (2%), the Netherlands, Spain, France, the Czech Republic, Sweden, Denmark, and India (1% every).
The prime five sectors historically specific by Conti have been producing (14%), genuine estate (11.1%), logistics (8.2%), professional solutions (7.1%), and trade (5.5%), with the operators specially singling out corporations in the U.S. (58.4%), Canada (7%), the U.K. (6.6%), Germany (5.8%), France (3.9%), and Italy (3.1%).
“Conti’s enhanced exercise and the data leak propose that ransomware is no for a longer period a activity among normal malware builders, but an illicit RaaS marketplace that presents work to hundreds of cybercriminals throughout the world with a variety of specializations,” Group-IB’s Ivan Pisarev claimed.
“In this marketplace, Conti is a notorious participant that has in point established an ‘IT company’ whose intention is to extort massive sums. It is apparent […] that the group will proceed its functions, both on its have or with the support of its ‘subsidiary’ projects.”
Located this article attention-grabbing? Follow THN on Fb, Twitter and LinkedIn to examine more distinctive written content we put up.
Some components of this short article are sourced from:
thehackernews.com

 Google warns of ISP-controlled Hermit spyware
Google warns of ISP-controlled Hermit spyware