The danger actor driving the prolific Emotet botnet is testing new attack techniques on a modest scale right before co-opting them into their larger sized quantity malspam strategies, probably in reaction to Microsoft’s go to disable Visual Basic for Apps (VBA) macros by default throughout its merchandise.
Contacting the new activity a “departure” from the group’s normal conduct, ProofPoint alternatively lifted the risk that the newest established of phishing email messages distributing the malware demonstrate that the operators are now “engaged in a lot more selective and constrained attacks in parallel to the common large scale email campaigns.”


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Emotet, the handiwork of a cybercrime team tracked as TA542 (aka Mummy Spider or Gold Crestwood), staged a revival of kinds late last 12 months following a 10-month-lengthy hiatus subsequent a coordinated legislation enforcement operation to consider down its attack infrastructure.
Considering that then, Emotet campaigns have specific 1000’s of shoppers with tens of 1000’s of messages in numerous geographic regions, with the message volume surpassing about a person million per marketing campaign in pick out cases.
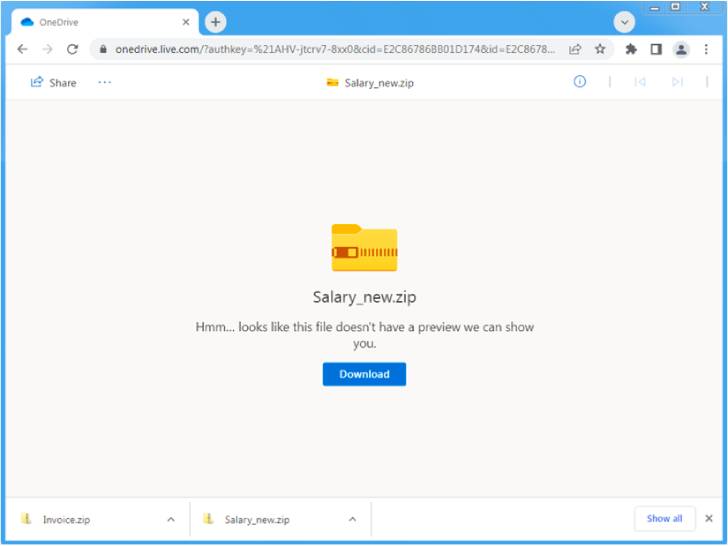
The new “very low volume” email campaign analyzed by the enterprise security firm associated the use of wage-themed lures and OneDrive URLs hosting ZIP archives that contain Microsoft Excel Incorporate-in (XLL) information, which, when executed, drop and operate the Emotet payload.
The new established of social engineering attacks is reported to have taken place concerning April 4, 2022, and April 19, 2022, when other common Emotet campaigns were place on keep.

The absence of macro-enabled Microsoft Excel or Term doc attachments is a substantial shift from formerly observed Emotet attacks, suggesting that the danger actor is pivoting away from the method as a way to get close to Microsoft’s plans to block VBA macros by default starting April 2022.
The development also will come as the malware authors very last 7 days mounted an issue that prevented prospective victims from receiving compromised on opening the weaponized email attachments.
“Immediately after months of consistent action, Emotet is switching points up,” Sherrod DeGrippo, vice president of risk investigate and detection at Proofpoint, mentioned.
“It is probable the risk actor is tests new behaviors on a tiny scale ahead of delivering them to victims additional broadly, or to distribute through new TTPs along with its present high-quantity strategies. Corporations should really be informed of the new techniques and assure they are employing defenses appropriately.”
Uncovered this report exciting? Abide by THN on Fb, Twitter and LinkedIn to read additional unique information we submit.
Some pieces of this short article are sourced from:
thehackernews.com


 Firms Push for CVE-Like Cloud Bug System
Firms Push for CVE-Like Cloud Bug System