SOC 2, ISO, HIPAA, Cyber Necessities – all the security frameworks and certifications nowadays are an acronym soup that can make even a compliance expert’s head spin. If you’re embarking on your compliance journey, go through on to discover the variations amongst requirements, which is very best for your company, and how vulnerability management can aid compliance.
What is cybersecurity compliance?
Cybersecurity compliance suggests you have met a established of agreed guidelines concerning the way you secure delicate details and buyer information. These principles can be set by legislation, regulatory authorities, trade associations or business groups.
For illustration, the GDPR is established by the EU with a large vary of cybersecurity requirements that each and every firm inside its scope need to comply with, when ISO 27001 is a voluntary (but internationally regarded) set of very best techniques for details security administration. Buyers more and more hope the assurance that compliance provides, for the reason that breaches and information disclosure will impression their operations, profits and reputation way too.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Which cybersecurity compliance typical is correct for you?
Every enterprise in just about every marketplace is operationally diverse and has various cybersecurity needs. The safeguards applied to continue to keep clinic individual records private are not the similar as the regulations for maintaining customers’ fiscal info protected.
For particular industries, compliance is the regulation. Industries that offer with sensitive private information and facts these types of as healthcare and finance are very controlled. In some scenarios, cybersecurity laws overlap across industries. For case in point, if you happen to be a organization in the EU that handles credit rating card payments, then you will require to be compliant with both of those credit and banking card regulations (PCI DSS) and GDPR.
Security basic principles like risk assessments, encrypted facts storage, vulnerability administration and incident reaction plans are quite prevalent across benchmarks, but what programs and functions need to be secured, and how, are specific to each individual standard. The requirements we take a look at below are much from exhaustive, but they are the most common compliance for begin-ups and SaaS organizations that tackle electronic info. Let us dive in.
GDPR
The Standard Facts Defense Regulation (GDPR) is a significantly-reaching piece of laws that governs how businesses – together with individuals in the US – accumulate and retailer the private details of European Union citizens. Fines for non-compliance are large and the EU is not shy about enforcing them.
Who requirements to comply with GDPR?
Buckle up because it truly is anybody that collects or procedures the personal data of everyone in the EU, wherever they go or store on the net. Personalized info or “personal data” includes just about nearly anything from the name and date of birth to geographic details, IP address, cookie identifiers, wellbeing details and payment information. So, if you do organization with EU residents, you happen to be necessary to comply with GDPR.
How vulnerability scanning can support compliance with GDPR
Your IT security policy for GDPR does not have to be a sophisticated document – it just demands to lay out in quick-to-recognize phrases, the security protocols your small business and workforce should really follow. You can also use no cost templates from SANS as products.
You can begin taking easy actions correct absent. There are automatic platforms that make it much easier to perform out which demands you by now satisfy, and which kinds you will need to right. For example, you are demanded to “build and apply ideal safeguards to restrict or consist of the affect of a probable cybersecurity function” which vulnerability scanning making use of a resource like Intruder can aid you attain.
SOC 2
SaaS and born-in-the-cloud corporations that give digital providers and units will be most acquainted with SOC 2 as it handles the storage, dealing with and transmission of digital details, although certification is getting increasingly common with all service companies.
There are two reviews: Style 1 is a stage-in-time assessment of your cyber security posture Variety 2 is an ongoing audit by an external assessor to check out you’re meeting these commitments, reviewed and renewed each individual 12 months. SOC 2 gives you some wiggle space on how to meet up with its standards, while PCI DSS, HIPAA and other security frameworks have incredibly express requirements.
Who desires SOC 2 compliance?
When SOC 2 isn’t a lawful prerequisite, it’s the most sought-just after security framework for rising SaaS providers. It’s more quickly and less expensive to obtain than most of the other standards in this list, although even now demonstrating a concrete commitment to cyber security.
How do you comply with SOC 2?
SOC 2 compliance involves you to set in spot controls or safeguards on procedure monitoring, information warn breaches, audit strategies and electronic forensics. The subsequent SOC 2 report is the auditor’s viewpoint on how these controls in shape the demands of 5 ‘trust principles’: security, confidentiality, processing integrity, availability and privacy.
ISO 27001
ISO generates a established of voluntary benchmarks for a wide range of industries – ISO 27001 is the typical for best observe in an ISMS (details security management procedure) to handle the security of fiscal info, intellectual residence, staff info, and other third-party details. ISO 27001 is not a lawful prerequisite by default, but numerous substantial enterprises or governing administration businesses will only work with you if you might be ISO qualified. It can be recognised as a person of the most arduous frameworks but it is really notoriously complicated, expensive and time consuming to entire.
Who wants it?
Like SOC 2, ISO 27001 is a superior way to show publicly that your business is committed and diligent when it arrives to facts security, and that you have taken techniques to maintain the information you share with them safe.
How do you comply with ISO 27001?
Third-party auditors validate that you’ve carried out all of the related very best procedures in accordance with the ISO common. There just isn’t a universal ISO 27001 checklist that guarantees certification. It is really up to you to choose how to make your mind up what is actually in scope and implement the framework, and auditors will use their discretion to assess just about every circumstance.
Keep in mind that ISO 27001 is mainly about risk administration. Risks are not static and evolve as new cyber threats emerge, so you must build automatic vulnerability management with a tool like Intruder into your security controls to appraise and examine new hazards as they emerge. Automated compliance platforms these as Drata can support speed up the course of action.
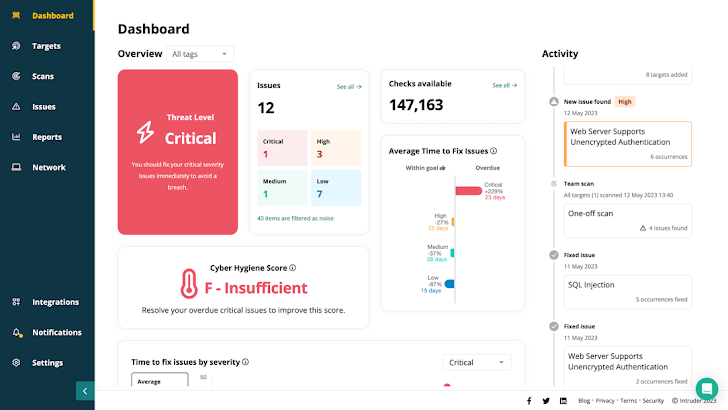 Intruder offers actionable, audit ready reports, so you can simply exhibit your security posture to auditors, stakeholders and customers
Intruder offers actionable, audit ready reports, so you can simply exhibit your security posture to auditors, stakeholders and customers
PCI DSS
The PCI DSS (Data Security Common) was produced by the PCI Security Specifications Council and the significant card brand names (American Convey, Mastercard and Visa) to regulate any one that suppliers, processes, and/or transmits cardholder data.
Who demands it?
In principle, anyone that procedures card payment transactions, but there are diverse guidelines dependent on the amount and form of payments you consider. If you use a 3rd-party card payment service provider like Stripe or Sage, they should really control the course of action and offer validation for you.
How to comply with PCI DSS
Not like ISO 27001 and SOC 2, PCI DSS demands a demanding vulnerability management method but accreditation is intricate. Third-party payment vendors will usually populate the PCI sort mechanically, giving validation at the simply click of a button. For smaller sized firms, this can help you save hours of function.
HIPAA
HIPAA (the Overall health Insurance policy Portability and Accountability Act) regulates the transfer and storage of individual info in the US health care field, the place compliance is a authorized prerequisite.
Who requirements it?
HIPAA compliance is mandatory for any enterprise that handles affected person data in the US, or any person doing business in the US with companies that are also HIPAA compliant.
How to comply with HIPAA
HIPAA can be challenging to navigate. It requires a risk management plan with security measures enough to minimize risk to a reasonable and appropriate amount. Although HIPAA won’t specify the methodology, vulnerability scans or penetration tests with a device like Intruder should be integral factors of any risk analysis and management method.
Cyber Necessities
Cyber Essentials is a UK federal government-backed plan created to test firms are adequately secured against typical cyberattacks. Similar to SOC 2, imagine of it as excellent cyber cleanliness – like washing your fingers or brushing your enamel. Developed for the more compact business enterprise without having focused security skills, it ought to be just the starting position of a far more sturdy security software
Who requires Cyber Necessities compliance?
Any organization bidding for a UK governing administration or general public sector agreement which will involve sensitive and individual info or furnishing particular specialized products and services.
How to comply with Cyber Necessities
The standard certificate is a self-assessment of standard security controls. Cyber Necessities Plus is a more sophisticated, thorough, arms-on technical certification that features a series of vulnerability exams that can be furnished by an automatic device like Intruder. The inner take a look at is an authenticated internal scan and a check of the security and anti-malware configuration of every single product.
Compliance won’t have to signify complexity
Compliance can seem to be like a labour-intense and high priced work out, but it can pale in comparison to the price tag of fixing a breach, spending settlements to customers, shedding your popularity, or having to pay fines. You can also miss out on out on potential business if you you should not have the certifications consumers be expecting.
But cybersecurity compliance would not want to be tough with present day automatic resources. If you use Intruder’s vulnerability administration that presently integrates with automatic compliance platforms like Drata then auditing, reporting and documentation for compliance will become a total large amount a lot quicker and simpler. Irrespective of whether you happen to be just starting your compliance journey or looking to improve your security, Intruder can help you get there speedier. Get started off currently with a free of charge trial.
Observed this post intriguing? Comply with us on Twitter and LinkedIn to go through a lot more exclusive content we publish.
Some elements of this post are sourced from:
thehackernews.com


 Xenomorph Banking Trojan: A New Variant Targeting 35+ U.S. Financial Institutions
Xenomorph Banking Trojan: A New Variant Targeting 35+ U.S. Financial Institutions