A team of scientists has identified a new data leakage attack impacting fashionable CPU architectures supporting speculative execution.
Dubbed GhostRace (CVE-2024-2193), it is a variation of the transient execution CPU vulnerability identified as Spectre v1 (CVE-2017-5753). The approach combines speculative execution and race ailments.
“All the widespread synchronization primitives applied working with conditional branches can be microarchitecturally bypassed on speculative paths applying a branch misprediction attack, turning all architecturally race-free critical locations into Speculative Race Ailments (SRCs), allowing for attackers to leak information from the goal,” the scientists reported.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The results from the Methods Security Investigation Team at IBM Study Europe and VUSec, the latter of which disclosed yet another facet-channel attack known as SLAM targeting modern processors in December 2023.

Spectre refers to a class of aspect-channel attacks that exploit department prediction and speculative execution on contemporary CPUs to read privileged details in the memory, bypassing isolation protections concerning apps.
Although speculative execution is a efficiency optimization approach utilized by most CPUs, Spectre attacks get benefit of the actuality that erroneous predictions go away behind traces of memory accesses or computations in the processor’s caches.
“Spectre attacks induce a sufferer to speculatively complete operations that would not happen through strictly serialized in-get processing of the program’s guidance, and which leak victim’s private details through a covert channel to the adversary,” the researchers behind the Spectre attack observed in January 2018.
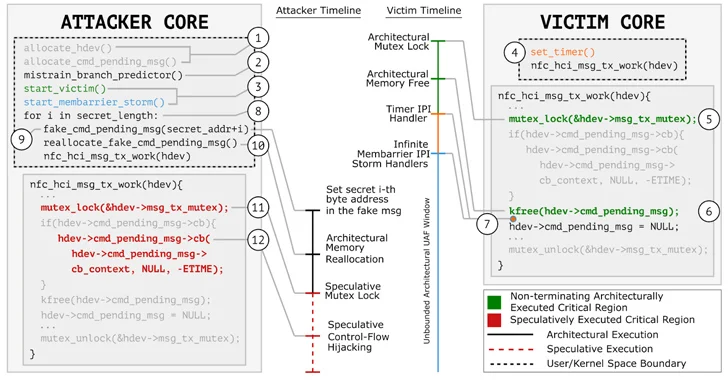
What will make GhostRace notable is that it allows an unauthenticated attacker to extract arbitrary information from the processor working with race situations to accessibility the speculative executable code paths by leveraging what is termed a Speculative Concurrent Use-Right after-Free of charge (SCUAF) attack.
A race problem is an undesirable situation that happens when two or far more procedures try to access the exact same, shared useful resource with out right synchronization, thereby primary to inconsistent results and opening a window of opportunity for an attacker to complete destructive actions.
“In features and exploitation tactic, an SRC vulnerability is similar to a basic race affliction,” the CERT Coordination Center (CERT/CC) discussed in an advisory.
“Nevertheless, it is diverse in that the attacker exploits reported race situation on a transiently executed path originating from a mis-speculated branch (comparable to Spectre v1), targeting a racy code snippet or gadget that eventually discloses information to the attacker.”
The net consequence is that it permits an attacker with access to CPU methods to accessibility arbitrary sensitive details from host memory.

“Any software, e.g., running process, hypervisor, etcetera., employing synchronization primitives by way of conditional branches with no any serializing instruction on that route and managing on any microarchitecture (e.g., x86, ARM, RISC-V, etc.), which permits conditional branches to be speculatively executed, is susceptible to SRCs,” VUSec said.
Following liable disclosure, AMD explained its current steering for Spectre “stays applicable to mitigate this vulnerability.” The maintainers of the Xen open-resource hypervisor acknowledged that all versions are impacted, though they explained it’s unlikely to pose a critical security risk.
“Out of caution, the Xen Security Crew have delivered hardening patches which includes the addition of a new LOCK_HARDEN system on x86 related to the existing Branch_HARDEN,” Xen reported.
“LOCK_HARDEN is off by default, owing to the uncertainty of there being a vulnerability less than Xen, and uncertainty above the functionality impression. Even so, we assume much more exploration to materialize in this region, and sense it is prudent to have a mitigation in location.”
Found this report fascinating? Comply with us on Twitter and LinkedIn to read through extra special material we post.
Some areas of this article are sourced from:
thehackernews.com

 Third-Party ChatGPT Plugins Could Lead to Account Takeovers
Third-Party ChatGPT Plugins Could Lead to Account Takeovers