The danger actors driving the HiatusRAT malware have returned from their hiatus with a new wave of reconnaissance and focusing on activity aimed at Taiwan-centered companies and a U.S. navy procurement technique.
Aside from recompiling malware samples for unique architectures, the artifacts are mentioned to have been hosted on new digital personal servers (VPSs), Lumen Black Lotus Labs claimed in a report published final 7 days.
The cybersecurity agency described the activity cluster as “brazen” and “a person of the most audacious,” indicating no signs of slowing down. The id and the origin of the threat actors are presently not known.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Targets included industrial corporations, these kinds of as semiconductor and chemical makers, and at the very least 1 municipal govt firm in Taiwan as nicely as a U.S. Department of Defense (DoD) server connected with distributing and retrieving proposals for defense contracts.

HiatusRAT was to start with disclosed by the cybersecurity corporation in March 2023 as owning qualified company-quality routers to covertly spy on victims mainly situated in Latin The us and Europe as aspect of a campaign that commenced in July 2022.
As several as 100 edge networking equipment globally had been infected to passively accumulate targeted traffic and renovate them into a proxy network of command-and-command (C2) infrastructure.
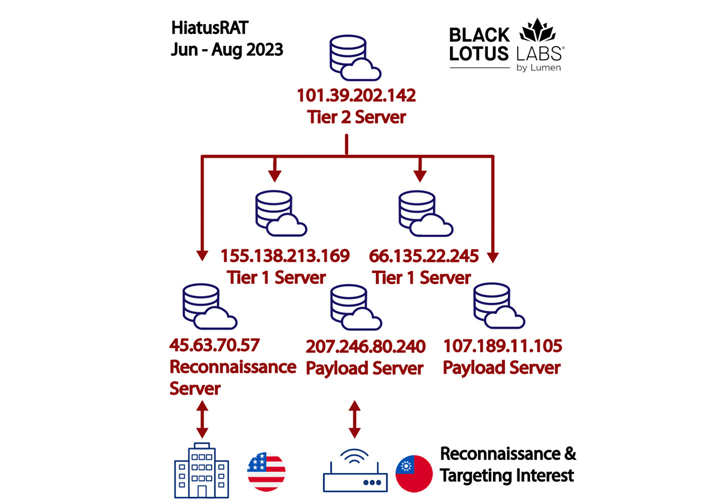
The latest established of attacks, observed from mid-June through August 2023, entail the use of pre-developed HiatusRAT binaries specifically designed for Arm, Intel 80386, and x86-64 architectures, alongside MIPS, MIPS64, and i386.
A telemetry analysis to establish connections designed to the server hosting the malware has exposed that “more than 91% of the inbound connections stemmed from Taiwan, and there appeared to be a choice for Ruckus-created edge gadgets.”
The HiatusRAT infrastructure consists of payload and reconnaissance servers, which right communicate with the victim networks. These servers are commandeered by Tier 1 servers, which, in convert, are operated and managed by Tier 2 servers.

The attackers have been identified as making use of two diverse IP addresses 207.246.80[.]240 and 45.63.70[.]57 to link to the DoD server on June 13 for close to a interval of two hours. 11 MB of bi-directional data is believed to have been transferred all through the interval.
It is really not clear what the finish objective is, but it truly is suspected that the adversary may have been on the lookout for publicly obtainable data relevant to existing and upcoming army contracts for long run concentrating on.
The concentrating on of perimeter belongings this kind of as routers has come to be some thing of a pattern in latest months, with threat actors involved with China joined to the exploitation of security flaws in unpatched Fortinet and SonicWall appliances to build very long-time period persistence within just concentrate on environments.
“In spite of prior disclosures of instruments and capabilities, the threat actor took the most minimal of steps to swap out current payload servers and carried on with their functions, devoid of even trying to re-configure their C2 infrastructure,” the enterprise said.
Uncovered this post intriguing? Adhere to us on Twitter and LinkedIn to go through additional exceptional material we write-up.
Some components of this short article are sourced from:
thehackernews.com


 WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams
WoofLocker Toolkit Hides Malicious Codes in Images to Run Tech Support Scams