The Iranian condition-sponsored threat actor tracked underneath the moniker Lyceum has turned to employing a new tailor made .NET-based mostly backdoor in recent campaigns directed against the Center East.
“The new malware is a .NET centered DNS Backdoor which is a custom-made variation of the open up supply device ‘DIG.net,'” Zscaler ThreatLabz researchers Niraj Shivtarkar and Avinash Kumar explained in a report released past 7 days.
“The malware leverages a DNS attack technique identified as ‘DNS Hijacking’ in which an attacker-controlled DNS server manipulates the response of DNS queries and resolves them as for each their destructive specifications.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

DNS hijacking is a redirection attack in which DNS queries to legitimate internet websites are intercepted to get an unsuspecting person to fraudulent pages beneath an adversary’s command. Unlike cache poisoning, DNS hijacking targets the DNS history of the web site on the nameserver, rather than a resolver’s cache.
Lyceum, also identified as Hexane, Spirlin, or Siamesekitten, is mainly regarded for its cyber attacks in the Middle East and Africa. Previously this yr, Slovak cybersecurity business ESET tied its pursuits to a further danger actor named OilRig (aka APT34).
The latest infection chain requires the use of a macro-laced Microsoft Document downloaded from a area named “news-place[.]stay,” impersonating a respectable information report from Radio Free Europe/Radio Liberty about Iran’s drone strikes in December 2021.
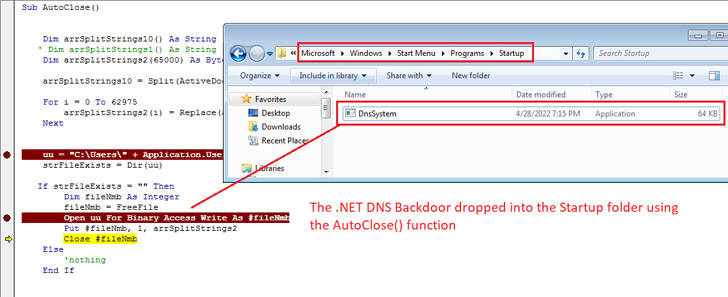
Enabling the macro success in the execution of a malicious code that drops the implant to the Windows Startup folder to establish persistence and make certain it mechanically operates every time the technique is restarted.

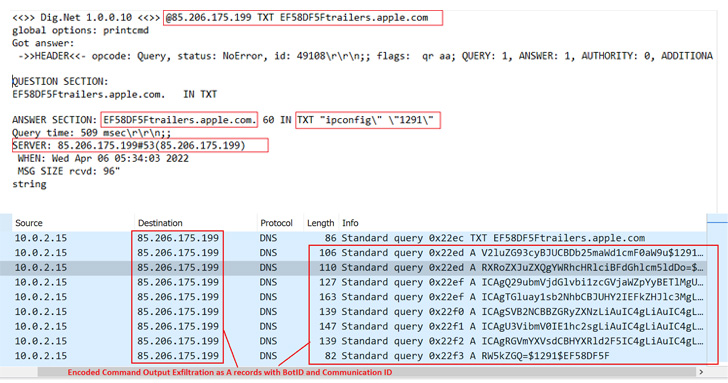
The .NET DNS backdoor, dubbed DnsSystem, is a reworked variant of the open up-source DIG.net DNS resolver instrument, enabling the Lyceum actor to parse DNS responses issued from the DNS server (“cyberclub[.]one”) and have out its nefarious plans.
In addition to abusing the DNS protocol for command-and-handle (C2) communications to evade detection, the malware is outfitted to upload and down load arbitrary data files to and from the remote server as well as execute malicious technique instructions remotely on the compromised host.
“APT danger actors are continuously evolving their techniques and malware to efficiently have out attacks towards their targets,” the researchers reported. “Attackers repeatedly embrace new anti-analysis tips to evade security options re-packaging of malware tends to make static examination even a lot more challenging.”
Uncovered this short article intriguing? Abide by THN on Fb, Twitter and LinkedIn to go through additional exceptional content we put up.
Some pieces of this article are sourced from:
thehackernews.com


 MIT Researchers Discover New Flaw in Apple M1 CPUs That Can’t Be Patched
MIT Researchers Discover New Flaw in Apple M1 CPUs That Can’t Be Patched