The North Korean nation-point out menace actor regarded as Kimsuky has been linked to a social engineering marketing campaign concentrating on specialists in North Korean affairs with the purpose of stealing Google qualifications and providing reconnaissance malware.
“More, Kimsuky’s objective extends to the theft of subscription qualifications from NK Information,” cybersecurity company SentinelOne claimed in a report shared with The Hacker News.
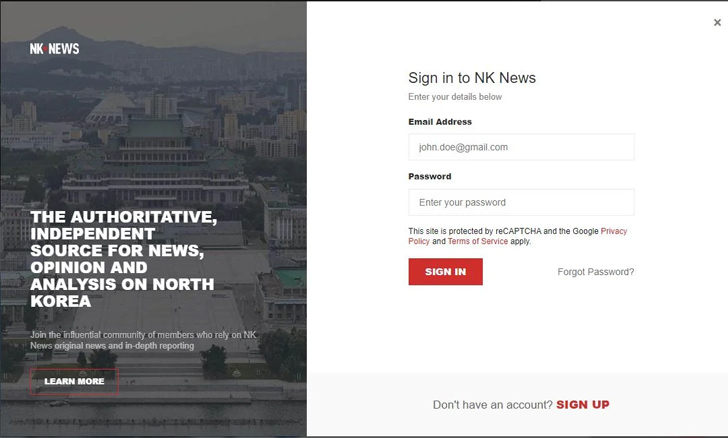
“To accomplish this, the group distributes email messages that lure specific people to log in on the malicious web site nknews[.]pro, which masquerades as the reliable NK News site. The login form that is presented to the concentrate on is designed to capture entered credentials.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
NK Information, recognized in 2011, is an American membership-centered news site that delivers stories and assessment about North Korea.
The disclosure comes days after U.S. and South Korean intelligence agencies issued an inform warning of Kimsuky’s use of social engineering practices to strike feel tanks, academia, and information media sectors. Last week, the threat group was sanctioned by South Korea’s Ministry of Foreign Affairs.

Active because at minimum 2012, Kimsuky is acknowledged for its spear-phishing practices and its tries to build rely on and rapport with meant targets prior to providing malware, a reconnaissance instrument referred to as ReconShark.
The best aim of the strategies is to acquire strategic intelligence, geopolitical insights, and entry sensitive info that are of worth to North Korea.
“Their technique highlights the group’s determination to producing a perception of rapport with the people today they concentrate on, probably escalating the good results rate of their subsequent malicious things to do,” security researcher Aleksandar Milenkoski mentioned.
The conclusions also adhere to new revelations from the South Korean authorities that extra than 130 North Korean watchers have been singled out as portion of a phishing campaign orchestrated by the government-backed hacking team.
What is a lot more, with North Korea earning a substantial chunk of its foreign-forex cash flow from cyber attacks and cryptocurrency heists, menace actors operating on behalf of the regime’s passions have been noticed spoofing economical institutions and venture capital firms in Japan, the U.S., and Vietnam.
Cybersecurity firm Recorded Long term related the exercise to a team tracked as TAG-71, a subgroup of Lazarus which is also known as APT38, BlueNoroff, Nickel Gladstone, Sapphire Sleet, Stardust Chollima, and TA444.
Impending WEBINAR🔐 Mastering API Security: Comprehension Your Genuine Attack Floor
Find out the untapped vulnerabilities in your API ecosystem and choose proactive steps to ironclad security. Be a part of our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:immediately afterexhibit:inline-block.look at_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px stable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-still left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-appropriate-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-fat:600letter-spacing:.6pxcolor:#596cec.wn-label:followingwidth:50pxheight:6pxcontent:”border-best:2px stable #d9deffmargin: 8px.wn-titlefont-dimension:21pxpadding:10px 0font-bodyweight:900textual content-align:leftline-height:33px.wn-descriptiontext-align:leftfont-dimension:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-shade:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-bodyweight:500letter-spacing:.2px
The adversarial collective has an proven track record of mounting financially motivated intrusion strategies targeting cryptocurrency exchanges, industrial financial institutions, and e-commerce payment methods throughout the world to illegally extract resources for the sanctions-hit region.
“The compromise of fiscal and investment decision companies and their customers might expose sensitive or confidential data, which may perhaps final result in lawful or regulatory action, jeopardize pending organization negotiations or agreements, or expose facts harmful to a company’s strategic expense portfolio,” the business famous.
The chain of evidence so far indicates that Lazarus Group’s motives are both equally espionage and financially pushed, what with the menace actor blamed for the new Atomic Wallet hack that led to the theft of crypto property worthy of $35 million, creating it the hottest in a prolonged listing of crypto companies to be stung by hacks in excess of the previous couple of a long time.
“The laundering of the stolen crypto assets follows a collection of ways that specifically match those people utilized to launder the proceeds of previous hacks perpetrated by Lazarus Team,” the blockchain analytics company stated.
“The stolen property are staying laundered working with unique expert services, like the Sinbad mixer, which have also been employed to launder the proceeds of earlier hacks perpetrated by the Lazarus Team.”
Located this post interesting? Observe us on Twitter and LinkedIn to read much more unique articles we article.
Some parts of this posting are sourced from:
thehackernews.com


 Barracuda Urges Immediate Replacement of Hacked ESG Appliances
Barracuda Urges Immediate Replacement of Hacked ESG Appliances