A week following Atlassian rolled out patches to include a critical flaw in its Queries For Confluence application for Confluence Server and Confluence Information Centre, the shortcoming has now occur less than energetic exploitation in the wild.
The bug in issue is CVE-2022-26138, which problems the use of a really hard-coded password in the application that could be exploited by a distant, unauthenticated attacker to gain unrestricted obtain to all pages in Confluence.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The serious-entire world exploitation follows the launch of the difficult-coded qualifications on Twitter, prompting the Australian software program enterprise to prioritize patches to mitigate opportunity threats concentrating on the flaw.
“Unsurprisingly, it didn’t choose very long […] to notice exploitation at the time the challenging-coded credentials had been unveiled, offered the high price of Confluence for attackers who normally leap on Confluence vulnerabilities to execute ransomware attacks,” Quick7 security researcher Glenn Thorpe mentioned.
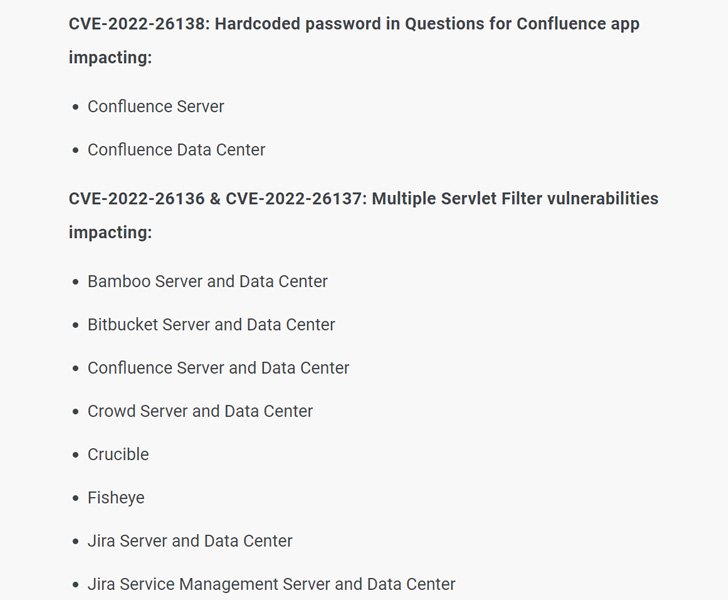
It’s really worth noting that the bug only exists when the Queries for Confluence application is enabled. That mentioned, uninstalling the Queries for Confluence app does not remediate the flaw, as the established account does not get quickly eliminated following the app has been uninstalled.

End users of the impacted item are encouraged to update their on-premise circumstances to the most current variations (2.7.38 and 3..5) as before long as doable, or consider techniques to disable/delete the account.
The growth also arrives as Palo Alto Networks, in its 2022 Device 42 Incident Response Report, found that danger actors are scanning for susceptible endpoints inside of 15 minutes of community disclosure of a new security flaw.
Observed this write-up intriguing? Follow THN on Fb, Twitter and LinkedIn to browse additional unique written content we post.
Some pieces of this article are sourced from:
thehackernews.com


 Spanish Police Arrest Alleged Radioactive Monitoring Hackers
Spanish Police Arrest Alleged Radioactive Monitoring Hackers