Malicious actors can gain unauthorized accessibility to users’ on the internet accounts by means of a new method known as “account pre-hijacking,” new analysis has located.
The attack requires intention at the account creation course of action which is ubiquitous in sites and other on-line platforms, enabling an adversary to execute a set of actions in advance of an unsuspecting sufferer makes an account in a concentrate on services.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The analyze was led by unbiased security researcher Avinash Sudhodanan in collaboration with Andrew Paverd of the Microsoft Security Reaction Middle (MSRC).
Pre-hijacking banking companies on the prerequisite that an attacker is previously in possession of a one of a kind identifier associated with a target, these types of as an email handle or phone range, which can be obtained both from the target’s social media accounts or credential dumps circulating on the web.

The attacks can then enjoy out in 5 distinct means, such as the use of the identical email deal with for the duration of account creation by both equally the adversary and the target, perhaps granting the two get-togethers concurrent obtain to the account.
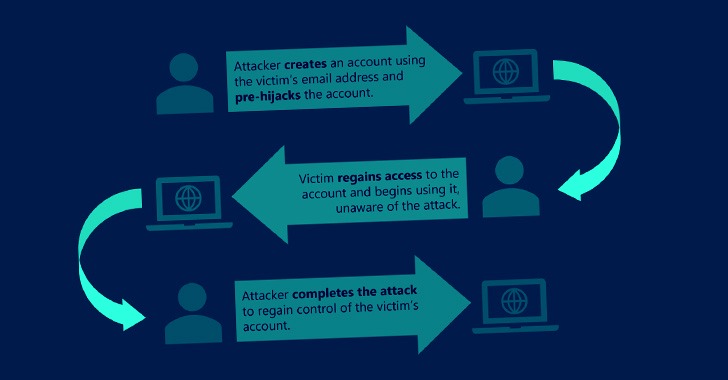
“If the attacker can make an account at a target services using the victim’s email address ahead of the sufferer produces an account, the attacker could then use a variety of procedures to put the account into a pre-hijacked condition,” the scientists mentioned.
“Immediately after the target has recovered entry and begun making use of the account, the attacker could get back accessibility and acquire above the account.” The five types of pre-hijacking attacks are down below –
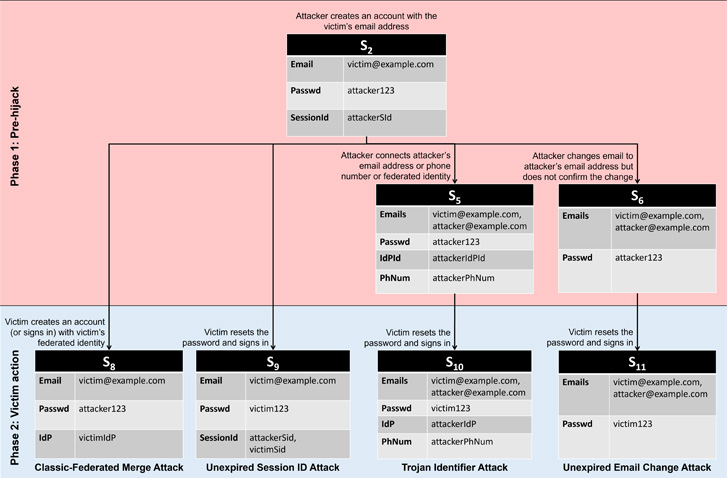
- Typical-Federated Merge Attack, in which two accounts designed applying typical and federated identity routes with the similar email address make it possible for the victim and the attacker to entry to the identical account.
- Unexpired Session Identifier Attack, in which the attacker creates an account working with the victim’s email address and maintains a prolonged-managing active session. When the person recovers the account using the similar email handle, the attacker proceeds to manage accessibility mainly because the password reset did not terminate the attacker’s session.
- Trojan Identifier Attack, in which the attacker results in an account working with the victim’s email handle and then provides a trojan identifier, say, a secondary email tackle or a phone variety below their control. Thus when the actual person recovers accessibility pursuing a password reset, the attacker can use the trojan identifier to get back obtain to the account.
- Unexpired Email Alter Attack, in which the attacker generates an account using the victim’s email handle and proceeds to improve the email handle to a single under their regulate. When the assistance sends a verification URL to the new email tackle, the attacker waits for the target to get better and get started making use of the account prior to completing the adjust-of-email process to seize manage of the account.
- Non-Verifying Id Provider (IdP) Attack, in which the attacker generates an account with the target provider employing a non-verifying IdP. If the target produces an account employing the vintage registration approach with the same email handle, it allows the attacker to obtain obtain to the account.
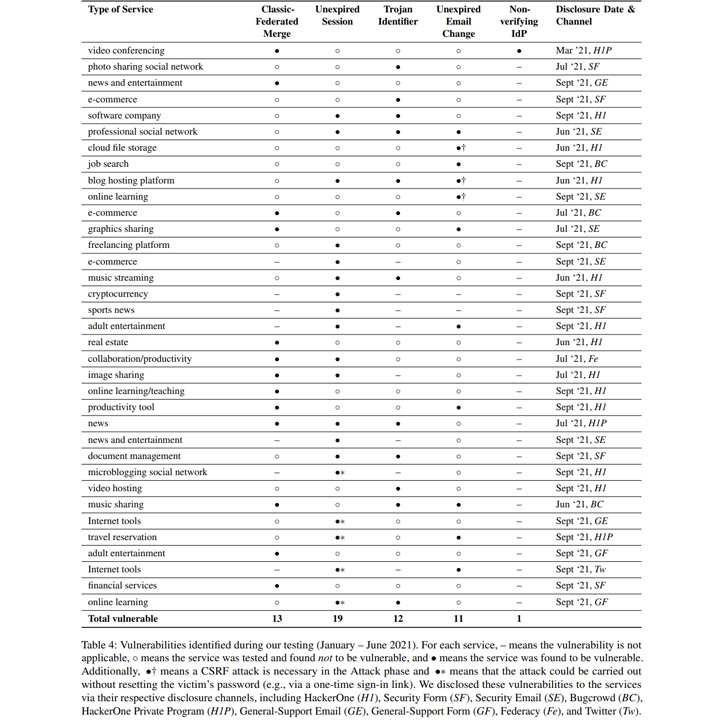
In an empirical analysis of 75 of the most common internet sites from Alexa, 56 pre-hijacking vulnerabilities have been recognized on 35 solutions. This includes 13 Common-Federated Merge, 19 Unexpired Session Identifier, 12 Trojan Identifier, 11 Unexpired Email Modify, and just one Non-Verifying IdP attacks –
- Dropbox – Unexpired Email Transform Attack
- Instagram – Trojan Identifier Attack
- LinkedIn – Unexpired Session and Trojan Identifier Attacks
- WordPress.com – Unexpired Session and Unexpired Email Transform Attacks, and
- Zoom – Traditional-Federated Merge and Non-verifying IdP Attacks
“The root cause of all of the attacks […] is a failure to confirm ownership of the claimed identifier,” the researchers claimed.

“Despite the fact that many providers do accomplish this kind of verification, they generally do so asynchronously, enabling the person to use certain functions of the account just before the identifier has been verified. Though this could possibly enhance usability (lessens person friction during indication up), it leaves the user susceptible to pre-hijacking attacks.”
Though utilizing rigorous identifier verification in companies is critical to mitigating pre-hijacking attacks, it is recommended that end users safe their accounts with multi-factor authentication (MFA).
“Accurately executed MFA will stop the attacker from authenticating to a pre-hijacked account soon after the target commences applying this account,” the scientists noted. “The assistance should also invalidate any classes made prior to the activation of MFA to stop the Unexpired Session attack.”
On prime of that, online companies are also recommended to periodically delete unverified accounts, implement a lower window to ensure a transform of email tackle, and invalidate classes for the duration of password resets for a protection in-depth tactic to account management.
“When a provider merges an account established by using the classic route with a single developed by using the federated route (or vice-versa), the support should be certain that the user at the moment controls both equally accounts,” Sudhodanan and Paverd claimed.
Discovered this short article attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to read through additional exceptional content we submit.
Some components of this write-up are sourced from:
thehackernews.com


 UK Government Cybersecurity Advisory Board Applications Now Open
UK Government Cybersecurity Advisory Board Applications Now Open