4 substantial severity vulnerabilities have been disclosed in a framework utilized by pre-set up Android Process applications with millions of downloads.
The issues, now fastened by its Israeli developer MCE Methods, could have probably permitted threat actors to stage remote and neighborhood attacks or be abused as vectors to get hold of sensitive information and facts by getting benefit of their comprehensive process privileges.
“As it is with a lot of of pre-put in or default programs that most Android equipment occur with these times, some of the afflicted applications can’t be thoroughly uninstalled or disabled devoid of getting root obtain to the unit,” the Microsoft 365 Defender Investigate Staff claimed in a report printed Friday.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The weaknesses, which array from command-injection to regional privilege escalation, have been assigned the identifiers CVE-2021-42598, CVE-2021-42599, CVE-2021-42600, and CVE-2021-42601, with CVSS scores amongst 7. and 8.9.
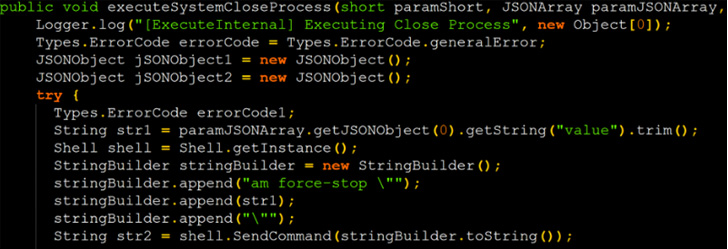 Command injection proof-of-concept (POC) exploit code
Command injection proof-of-concept (POC) exploit code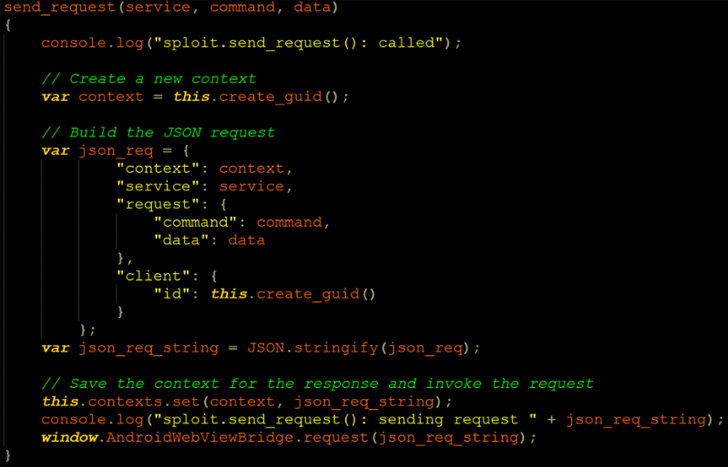 Injecting a equivalent JavaScript code to the WebView
Injecting a equivalent JavaScript code to the WebView
The vulnerabilities had been identified and noted in September 2021 and there is no evidence that the shortcomings are staying exploited in the wild.
Microsoft didn’t disclose the comprehensive record of applications that use the vulnerable framework in question, which is designed to present self-diagnostic mechanisms to determine and repair issues impacting an Android gadget.
This also intended that the framework had wide accessibility permissions, together with that of audio, camera, power, site, sensor details, and storage, to carry out its features. Coupled with the issues identified in the services, Microsoft stated it could allow an attacker to implant persistent backdoors and take about control.

Some of the affected applications are from significant worldwide cell service suppliers this sort of as Telus, AT&T, Rogers, Liberty Cell, and Bell Canada –
- Cellular Klinik Product Checkup (com.telus.checkup)
- Machine Enable (com.att.dh)
- MyRogers (com.fivemobile.myaccount)
- Independence System Care (com.liberty.mlp.uat), and
- Product Content material Transfer (com.ca.bell.contenttransfer)
On top of that, Microsoft is recommending consumers to look out for the app package deal “com.mce.mceiotraceagent” — an app that might have been mounted by mobile phone restore shops — and get rid of it from the phones, if discovered.
The inclined applications, though pre-mounted by the phone companies, are also out there on the Google Perform Store and are claimed to have passed the app storefront’s automatic safety checks without having increasing any red flags mainly because the course of action was not engineered to glance out for these issues, some thing that has since been rectified.
Identified this posting intriguing? Observe THN on Facebook, Twitter and LinkedIn to read extra distinctive content material we article.
Some elements of this report are sourced from:
thehackernews.com


 CISA Publishes 5G Security Evaluation Process Plan
CISA Publishes 5G Security Evaluation Process Plan