An emerging menace cluster originating from North Korea has been connected to establishing and using ransomware in cyberattacks focusing on small companies due to the fact September 2021.
The team, which calls itself H0lyGh0st just after the ransomware payload of the same identify, is getting tracked by the Microsoft Danger Intelligence Heart underneath the moniker DEV-0530, a designation assigned for unknown, emerging, or a creating group of danger exercise.
Specific entities principally involve tiny-to-midsize companies these types of as producing organizations, banking companies, educational institutions, and function and conference preparing companies.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Alongside with their H0lyGh0st payload, DEV-0530 maintains an .onion website that the group takes advantage of to interact with their victims,” the scientists claimed in a Thursday evaluation.
“The group’s typical methodology is to encrypt all information on the concentrate on system and use the file extension .h0lyenc, mail the victim a sample of the documents as proof, and then demand payment in Bitcoin in exchange for restoring accessibility to the information.”
Ransom quantities demanded by DEV-0530 vary everywhere amongst 1.2 and 5 bitcoins, while an examination of the attacker’s cryptocurrency wallet shows no profitable ransom payments from its victims as of early July 2022.
DEV-0530 is believed to have connections with a different North Korean-based mostly team known as Plutonium (aka DarkSeoul or Andariel), a sub-team functioning beneath the Lazarus umbrella (aka Zinc or Concealed Cobra).
The illicit scheme adopted by the danger actor is also regarded to choose a leaf from the ransomware landscape, leveraging extortion techniques to implement pressure on victims into shelling out up or risk obtaining their information posted on social media.
DEV-0530’s dark web portal statements it aims to “near the gap concerning the prosperous and inadequate” and “assistance the lousy and starving folks,” in a tactic that mirrors a different ransomware relatives known as GoodWill that compels victims into donating to social brings about and giving economic aid to people in have to have.
The specialized breadcrumbs that tie the team to Andariel stem from overlaps in the infrastructure set as properly as dependent on communications between email accounts controlled by the two attacker collectives, with DEV-0530 exercise consistently observed during Korea Normal Time (UTC+09:00).
“In spite of these similarities, distinctions in operational tempo, targeting, and tradecraft advise DEV-0530 and Plutonium are unique groups,” the researchers pointed out.
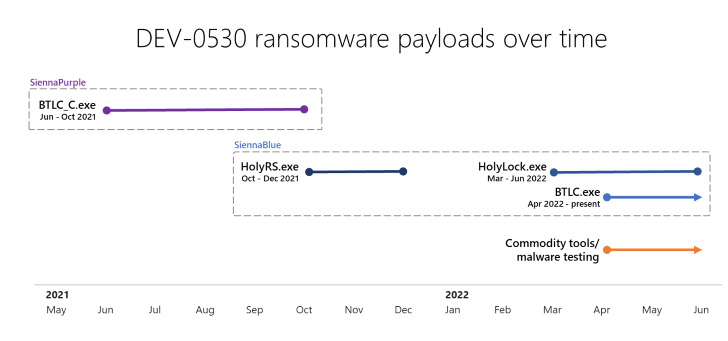
In a signal that suggests active improvement, four different variants of the H0lyGh0st ransomware had been churned out concerning June 2021 and May perhaps 2022 to concentrate on Windows units: BTLC_C.exe, HolyRS.exe, HolyLock.exe, and BLTC.exe.
When BTLC_C.exe (dubbed SiennaPurple) is created in C++, the other 3 versions (codenamed SiennaBlue) are programmed in Go, suggesting an endeavor on the aspect of the adversary to produce cross-system malware.
The newer strains also arrive with enhancements to their core features, such as string obfuscation and talents to delete scheduled responsibilities and get rid of them selves from the infected devices.
The intrusions are reported to have been facilitated by way of the exploitation of unpatched vulnerabilities in community-facing web programs and material management devices (e.g., CVE-2022-26352), leveraging the buy to fall the ransomware payloads and exfiltrate sensitive details prior to encrypting the documents.
The results arrive a week right after the U.S. cybersecurity, and intelligence organizations warned about the use of Maui ransomware by North Korean federal government-backed hackers to target the healthcare sector considering the fact that at minimum May possibly 2021.
The expansion from economic heists to ransomware is currently being seen as nevertheless another tactic sponsored by the North Korean federal government to offset losses from sanctions, purely natural disasters, and other financial setbacks.
But given the narrow established of victims than is ordinarily related with point out-sponsored activity against cryptocurrency organizations, Microsoft theorized the attacks could be a aspect-hustle for the risk actors concerned.

“It is equally achievable that the North Korean government is not enabling or supporting these ransomware attacks,” the researchers claimed. “Folks with ties to Plutonium infrastructure and tools could be moonlighting for individual acquire. This moonlighting idea may make clear the usually-random variety of victims specific by DEV-0530.”
The ransomware risk evolves in a post-Conti globe
The development also arrives as the ransomware landscape is evolving with current and new ransomware teams, specifically LockBit, Hive, Lilith, RedAlert (aka N13V), and 0mega, even as the Conti gang formally shuttered its operations in reaction to a enormous leak of its interior chats.
Including gasoline to the hearth, LockBit’s improved successor also comes with a brand new information leak web site that lets any actor to obtain information stolen from victims, not to point out incorporating a research function that can make it easier to floor delicate information and facts.
Other ransomware households have also added related abilities in an endeavor to build searchable databases of data stolen throughout attacks. Notable amongst this listing are PYSA, BlackCat (aka ALPHV), and the Conti offshoot recognised as Karakurt, according to a report from Bleeping Pc.
Based mostly on studies collected by Digital Shadows, 705 companies ended up named in ransomware information leak internet sites in the next quarter of 2022, marking a 21.1% maximize from Q1 2022. The top rated ransomware families through the period provided LockBit, Conti, BlackCat, Black Basta, and Vice Society.
Found this post intriguing? Adhere to THN on Fb, Twitter and LinkedIn to read more special material we publish.
Some sections of this posting are sourced from:
thehackernews.com


 Chinese authorities summon Alibaba executives over data breach
Chinese authorities summon Alibaba executives over data breach