A new analysis carried out by a group of lecturers from the College of California San Diego has discovered for the to start with time that Bluetooth signals can be fingerprinted to keep track of smartphones (and consequently, men and women).
The identification, at its main, hinges on imperfections in the Bluetooth chipset hardware released during the producing process, resulting in a “exclusive actual physical-layer fingerprint.”
“To perform a actual physical-layer fingerprinting attack, the attacker will have to be equipped with a Software package Described Radio sniffer: a radio receiver able of recording uncooked IQ radio signals,” the scientists reported in a new paper titled “Evaluating Physical-Layer BLE Place Tracking Attacks on Cellular Units.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The attack is produced doable due to the ubiquitous character of Bluetooth Reduced Strength (BLE) beacons that are continuously transmitted by modern-day equipment to enable very important functions these types of as call tracing throughout community health and fitness emergencies.
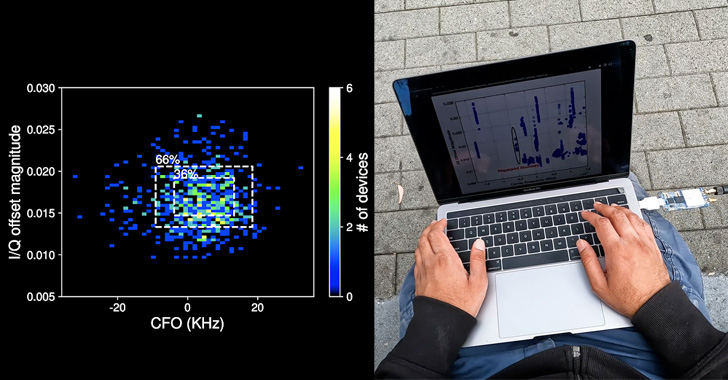
The hardware problems, on the other hand, stem from the truth that each Wi-Fi and BLE components are typically integrated alongside one another into a specialised “combo chip,” efficiently subjecting Bluetooth to the similar set of metrics that can be made use of to uniquely fingerprint Wi-Fi products: carrier frequency offset and IQ imbalance.
Fingerprinting and tracking a gadget then entails extracting CFO and I/Q imperfections for each and every packet by computing the Mahalanobis length to identify “how close the functions of the new packet” are to its earlier recorded hardware imperfection fingerprint.
“Also, considering the fact that BLE units have quickly steady identifiers in their packets [i.e., MAC address], we can recognize a machine centered on the normal above numerous packets, escalating identification precision,” the scientists reported.

That mentioned, there are various challenges to pulling off such an attack in an adversarial setting, chief amongst them currently being that the means to uniquely detect a gadget depends on the BLE chipset employed as very well as the chipsets of other products that are in shut actual physical proximity to the target.
Other critical variables that could have an affect on the readings include things like product temperature, distinctions in BLE transmit energy concerning iPhone and Android gadgets, and the quality of the sniffer radio employed by the destructive actor to execute the fingerprinting attacks.
“By evaluating the practicality of this attack in the discipline, specially in active options these as coffee retailers, we observed that specific units have distinctive fingerprints, and as a result are notably vulnerable to tracking attacks, many others have typical fingerprints, they will usually be misidentified,” the scientists concluded.
“BLE does present a locale tracking menace for mobile products. Having said that an attacker’s skill to track a unique concentrate on is basically a make any difference of luck.”
Discovered this post appealing? Observe THN on Fb, Twitter and LinkedIn to examine extra special written content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Palermo ransomware attack: Vice Society claims responsibility as city details recovery strategy
Palermo ransomware attack: Vice Society claims responsibility as city details recovery strategy